Circuits and Systems
Vol.07 No.13(2016), Article ID:72033,21 pages
10.4236/cs.2016.713340
Dynamic Spectrum Access Protocol for the Digital Dividend
Raoul Zamblé1*, Raymond Gbégbé2, Jean-Marie Kadjo1, Olivier Asseu1,2*, Pacôme Brou2
1Ecole Supérieure Africaine des Technologies de l’Information et de la Communication (ESATIC), Abidjan, Côte d’Ivoire
2Institut National Polytechnique Houphouet Boigny (INPHB), Yamoussoukro, Côte d’Ivoire

Copyright © 2016 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY 4.0).
http://creativecommons.org/licenses/by/4.0/



Received: May 10, 2016; Accepted: November 13, 2016; Published: November 16, 2016
ABSTRACT
It is not more and more, easy to satisfy the important and growing spectrum demands in the context of the static conventional policy spectrum allocation. Therefore, to find a suitable solution to this problem, we are to days observing the apparition of flexible dynamic spectrum allocation methods. These methods that ought to improve more significantly the spectrum use have gained much interest. In fact, the digital dividend due to the change-over from the analog television to the digital terrestrial television must be efficiently used. So the Dynamic Spectrum Access (DSA) can potentially play a key role in shaping the future digital dividend use. In the DSA, two kinds of users or networks coexist on different channels. The first one, known as the primary user, accesses to a channel with high priority; and the second one, known as secondary user has a low priority. This paper presents a dynamic spectrum access protocol based on an auction framework. Our protocol is an interesting tool that allows the networks to bid and obtain on the available spectrum, the rights to be primary and secondary users according their valuations and traffic needs. Based on certain offers, our protocol selects primary and secondary users for each idle channel in order to realize the maximum economic for the regulator or social benefits. We deal with the case in which the offers of the networks are independent one another even if they will share the same channels. We design an algorithm in accordance with our dynamic spectrum access protocol. The algorithm is used here to find an optimal solution to the access allocation problem, specifically to digital dividend. Finally, the results in the numeric section, regarding the three suggested scenarios, show that the proposed dynamic spectrum access protocol is viable. The algorithm is able to eliminate all non-compliant bidders for the available spectrum sharing. We notice that the revenue or social benefits of the regulator is maximized when we have on each channel, one primary user and the maximum number of secondary users.
Keywords:
Dynamic Spectrum Access Protocol, Centralized Spectrum Sharing, Spectrum Auctions, Digital Dividend

1. Introduction
The allocation and management of radio spectrum are administered by national regulatory authorities. These authorities work together within a harmonized framework established by international policy initiatives. Radio spectrum refers to a specific range of frequencies of electromagnetic energy that is used to communicate information. Applications important for society such as radio and television broadcasting, civil aviation, satellites, defense and emergency services depend on specific allocations of radio frequency. Recently, the demand for spectrum has increased dramatically, driven by growing quantities of data transmitted over the internet and rapidly increasing numbers of wireless devices, including smart phones and tablets, Wi-Fi networks and everyday objects connected to the internet. However, since existing wireless networks occupy extensive parts of the available radio spectrum, there is insufficient spectrum available to all new wireless networks. In fact, the natural and inextensible character of the radio spectrum makes it a rare commodity that should be used sparingly. It appears that the spectral resource managed by the regulatory agencies seems to be almost completely occupied and is not being utilized efficiently [1] . In addition, experts believe that spectrum use for communication will increase from 200% to 300% in the coming years [2] . Furthermore, the traditional management does not allow an actual effective use. For example, it was noted that many frequencies are unoccupied during the day when they are officially assigned [3] . This paradoxical situation obliges policy makers and regulators around the world to focus again on spectrum regulation by emphasizing more and more on the best possible balance to achieve between the certainty required to ensure the stable deployment of services and stable flexibility leading to an improvement of costs, services and the use of innovative technologies. A new approach is then proposed to address this problem: the dynamic spectrum access which allows a secondary use of spectrum holes left by the primary users [4] . Mostly, the spectrum is available according time and geographic location. Under the lead of the FCC, the next generation wireless communication systems are being designed for the dynamic use of spectrum. This new way of spectrum use is going to emerge in order to encourage the intensive and efficient use of the spectrum. Regarding the context, we can notice that the expression dynamic spectrum access has different connotations [5] . This approach was possible with the advent of the concepts of “software defined radio” and “Cognitive Radio”. In this context, two main architecture approaches for the spectrum distribution were developed: decentralized and centralized distribution.
The decentralized or distributed sharing spectrum approach presents some disadvantages like huge risk of signals collision between secondary users; each user must have a secondary detection function of the spectrum holes and the protocols of cooperation [6] .
In centralized spectrum sharing [7] , a centralized entity possesses detailed information about the network and handles with all the spectrum allocation and access procedures. Hence, compared to distributed, centralized approaches simplify the design of spectrum sharing. Among centralized spectrum techniques, dynamic spectrum access protocol (DSAP) [7] is a representative one and is the focus of this paper. In fact, the dynamic spectrum access involves two kinds of users: the primary user and the secondary user. Therefore, it is important for the regulator bodies to find the best mechanism to assign primary and secondary user rights on the spectrum under their control. A primary user has high priority access on a channel whereas a secondary user has a low priority. For instance, if we have a network which wishes to mainly transmit a real time traffic, such as video or voice, it ought to access on a channel as primary user with high priority. Otherwise, this network opts for a secondary user rights to transmit its elastic traffic like e-mail or file transfer. So we can remark that the secondary user price must be lower than the price of the primary user rights. In case of mixture traffic types, i.e. mixture of real time and elastic traffic, the network bids for a primary user rights on some channels and for a secondary user rights on others.
Indeed, we can obviously see that auctions are well indicated for assigning primary and secondary user rights. So auctions are a mechanism for the regulator to obtain higher income than that obtained from static pricing, especially the regulator is not required to know in advance the prices offered by bidders [8] . It is also beneficial for the bidders to participate in auctions since in general they have opportunity to suggest prices of goods according their needs [8] . The FCC has been conducting spectrum auctions since 1994 to allocate licenses for radio spectrum in the static allocation context [9] . But, so far no auctions have been conducted for cognitive radio networks in the dynamic spectrum access context.
The development of digital terrestrial television (DTT) technology has given rise to a major change in spectrum use throughout the world. As well as increasing the number and quality of television services, digital television has freed up a significant part of the Ultra High Frequency (UHF) band that has been used principally for broadcasting. The spectrum available for new services as a result of this switchover is referred to as the “digital dividend”. Depending on the country, the digital dividend is located in the VHF bands (174 to 230 MHz) and UHF bands (470 to 862 MHz).
In this paper, we suggest the dynamic spectrum access protocol based on auction to use this digital dividend. As far as we are concerned, we have no knowledge to date of work done in relation to this scenario. Here, we present a particular form of auction for the allocation of idle channels in one step through the simultaneous sale of primary and secondary user rights on those channels.
We consider three scenarios to highlight our algorithm performances. In these scenarios, the regulator broker leads the auction in all allocation periods that can be time slots about 30 or 60 minutes to sell primary and secondary users rights on the different available channels within the digital dividend specifically. The broker sets a guaranteed minimum price for each kind of user at each allocation period. This flexibility of our algorithm allows the regulator through its broker to determine the minimum prices based on demand. For instance, during the usual allocation period where there are lot of demands, the broker may increase the primary and the secondary minimum prices, and in the allocation periods usually supposed to receive less traffic demands, it can decrease these prices. The three scenarios present five idle channels that must be allocate to the different bidders and we supposed four maximum secondary users. Here the bidders are obviously any kind of wireless networks that can transmit theirs traffics through the digital dividend. And they can opt for the primary or secondary user rights according to their traffic types. When they are supposed to transmit a real time traffic, automatically they choose the primary user right and when it is to transmit traffic without time constrain, they opt to the secondary user right. The first and the third scenarios present the cases where the bidders sent offers that are all superior to the minimum prices set by the regulator. But, in the third scenario, we have less bidders compared to the number of available channels. In the second scenario, we can explore the case in which our algorithm eliminated the bidders that proposed prices inferior to the minimum prices set by the broker. In all these three scenarios, we can see that the broker maximize its revenue or the social benefits when there are one primary user and the maximum allowed secondary users.
The rest of this paper is organized as follows. Section 2 presents the different existing approaches of the spectrum trade. Section 3 talks about the proposed DSAP, while Section 4 presents the numerical outcomes. Finally, the paper ends with a conclusion and the perspectives in Section 5.
2. Approach of Spectrum Trade
The centralized and dynamic access to the spectrum shows two examples: on the first hand the DIMSUNnet (Dynamic Intelligent Management of Spectrum for Ubiquitous Mobile-access network) inspired by the Dim Sum operations in Chinese restaurants [10] and on the other hand the agnostic technology, suggested by a study of Ofcom [11] . The common feature of the architectures related to these two examples is the use of a broker as a central entity to coordinate the access to the free spectrum. The distribution of the resources with the broker is based on the principle of auction. In fact, auctions are an economic instrument as regards sales known for the selling of certain goods; i.e. allocate the goods and simultaneously determine their prices based on offers from potential buyers. In the example of wired networks, using the protocol of the resource auction multiple access (or Resource Auction Multiple Access-RAMA) [12] , the nodes of the networks send random numbers that represent their offers. The node having placed the highest number is authorized to use the resource under very specific conditions. However, the offers contain no valuable information. So, by integrating this valuable information, it is possible to have real time auction in which market value and resource allocation can be combined simultaneously. In the reference [13] , some auctions are proposed in real time between some service providers and users. In these auctions, all the users try to access to the available spectrum resources at each time slot, measured in seconds or even milliseconds. The service provider is mainly the auctioneer who is authorized to establish a guaranteed price in order to ensure a minimum benefit. Then a cognitive radio terminal dynamically calculates the offers. Different radio access technologies are used at different access point by multi-standard cognitive radio nodes for their bids. Thus, a cognitive radio network will try to maximize the utility functions of its users by upgrading the quality of service (QoS) at the possible lowest price. The disadvantage of this method of auction is that it cannot give any guarantee QoS to the nodes, for each time interval another cognitive radio node could place a higher offer than the active user and interrupt its communication. In [14] , auctions at the inter-operators level are presented. Given that the long-term frequency planning of the operators must take into account the request of maximum traffic time during a busy hour, there will be parts of the radio resources unoccupied during the day. Thus, operators with base stations in areas of service request can lease their unused channels. As in spectrum overlay approach, known as spectrum pooling [15] , article [14] considers the access to spectrum based on OFDM, in which a carrier OFDM can be used as a sellable spectral unit during a time interval. Thus these auctions take advantage of the flexibility inherent in the OFDM technique in relatively the frequency and time domains. The reference [16] , also discusses a spectrum auction in accordance with a temperature interference constraint assumption applied to a certain point of measurement. The system includes a central spectrum manager, but the nodes of the users do not trade their spectrum resources. Instead, they receive the interference signal and the signal to noise ratio (SINR), and their authorized transmission power.
As we can see through the various approaches of research presented above, the best way to increase the spectral efficiency, is to allow local adjustment and short-term of the current traffic volume. The traffic varies stochastically both with time and the geographical area. In the case of operators operating in licensed frequency bands, during the busy hour, it may happen that an operator has its resources fully saturated and must refuse further connections, whereas another one in the same cell has his resources unused. But few minutes after, things could change and the operator, who was facing a bottleneck, finds itself in the situation of second one and vice versa, the first in its turn is faced with a situation its resources congestion. Thus, operators facing to an important rate of traffic, could buy extra resources. Then other service providers at the same time, locally and temporarily located in a case of under-utilization of their resources, could offer some to others. So by selling and buying extra resources for a limited time, operators could benefit from this appropriate allocation.
As already mentioned above, auctions are economic tools to determine arbitrarily the price of a commodity and at the same time, allot that commodity. So auctions have a particular interest because any absolute price of item is not indicated. A good price depends on the offers and demands of the stakeholders. As a matter of fact, we have two types of auctions that are continuous and discontinuous. The continuous form of the auction is specified by asynchronous ascent of offer with regular prices updates. In the discontinuous auction, all the bids are collected once in a limited time and after that the contract may carry out.
Unlike licensed bands, the distribution of spectrum resources available in the digital dividend due to passage from the analog television to the digital terrestrial television as mentioned in introduction will not be driven in the same manner. Here, a regulator through a broker conducts a discontinuous auction to sell primary and secondary users rights to the networks for a set of idle channels.
We suggest that a structural frame divided into time slots of short durations is introduced, about 30 minutes for instance, called allocation periods. The distribution principle of allocation periods is shown by the example in Figure 1. This figure only takes into account the temporal dimension by grouping time slots in hours and days.
During each allocation period, the regulator broker allocates the primary and secondary users rights through our proposed Dynamic Spectrum Access Protocol (DSAP).
3. Dynamic Spectrum Access Protocol
3.1. Architecture Assumption
DSAP enables dynamic spectrum access through a coordinating central entity which can be called a broker and allows efficient resource sharing and utilization in a limited geographical environment. The architecture of DSAP used in this paper is shown in Figure 2.
DSAP consists of client, server, and relay [6] . DSAP clients are here the bidder networks in a vicinity of a broker. They collect local needs of spectrum resources and send
Figure 1. Diagram showing an example of allocation periods following the temporal dimension.
Figure 2. Architecture of DSAP.
them to the broker in all the allocation period. We precise that the digital dividend is supposed to be free. It is not assigned to any technology or any service. The DSAP server is the broker directly linked to the DSAP database and based on the different information from the digital dividend constructs a global view of network called Radio Map. DSAP client cannot choose a wireless communication channel arbitrarily, instead it has to request appropriate channel assignment from DSAP server. DSAP server accepts communication requests from clients, and based on various optimization goals mentioned in the following section and the set of policies defined by the regulator and the Radio Map, determines an optimal radio spectrum allocation for the clients. Under different optimization goals, various algorithms and policies can be applied in the procedure of obtaining the optimal distribution of radio spectrum. After deciding spectrum assignment, DSAP server sends a feedback with a time-limited spectrum allocation, called a lease. Once the lease is done, the DSAP server must charge the client in terms of payment for the allocation period even if the client didn’t use the allocated spectrum. We have also, at least two wireless interfaces belonging to the DSAP server. The first one is used to sense the spectrum holes. And, the other interface operates on a pre-defined Common Control Channel (CCC), which is used for exchanging control traffic between server and client. The main role of DSAP relay is to allow communications between broker server and network nodes that are not inside its geographic area.
According to the spectrum sharing taxonomy, spectrum sharing of DSAP is centralized, cooperative, with CCC and multiple radio interfaces [6] .
3.2. System Model
We assume there are two groups of networks coexisting in a geographic cell domain, sharing the digital dividend: primary networks and secondary networks. In fact, the TDMA which is one of the traditional methods of statistical multiplexing can be associated to the OFDM to provide an environment of multiuser. However the intrinsic characteristics of OFDM provide a multiple users environment. Indeed, the OFDM has a multicarrier nature that gives a sole opportunity to share the spectrum at the very fine granularity level.
Therefore, to achieve the dynamic spectrum access goal for our problem, OFDM is chosen as the underlying technology. We can also mention the robustness of OFDM against multipath distortion and its easy implementation. With its different subcarriers, OFDM is more flexible in terms of channel allocation and more appropriate for a dynamic spectrum access environment. To date orthogonal frequency division multiple access (OFDMA) is known as the only one multiuser version of OFDM. The OFDMA technique allows the allocation of single or multiple groups of subcarriers to one or several users for their traffics transmission. Further, the adaptation of modulation, coding and bandwidth are other main benefits of OFDMA that make it more flexible in terms of spectrum resource management.
Through this paper, we mainly deal with the scenario in which there are identical orthogonal OFDMA subcarriers in the cellular domain. Each OFDMA subcarrier represents a channel. So a broker associated with DSAP, drives an auction for selling primary and secondary user rights on a set of idle channels in the range of the digital dividend. Each network is bidder with several wireless nodes and participates independently in the auction. Finally, the regulator’ broker allocates the primary and secondary user rights on the channels based on the different offers of the networks. The trade of spectrum between the networks, performed here by our centralized model, allows the short-term flexibility over small geographical areas, like cell in order to satisfy current traffic demands. Once, the spectrum resources have been sold to a certain network, these resources are entirely at its disposal for the allocation period unless the broker announces a new one.
It is mandatory for this model to authorize only one primary network on a channel in order to avoid any harmful interference between two primary users. However, several networks can obtain secondary user rights on a channel. The intuitive goal behind the presence of multiple secondary users is to increase the spectral efficiency of the network, while, depending on the type of network, not affecting higher priority users which are primary networks. In addition, to simplify our system model, all the secondary users are supposed to have equal rights on each channel they share together.
Now, we precise that the model is concerned with two types of traffic: the real time traffic or traffic with delay constraint such as video or voice, and elastic traffic or traffic without delay constraint such as file transfer or email, for instance. In our scenario, we can find a single network as primary user on a channel and one of the secondary users on the others channels. So, this network must transmit its real time traffic with its primary user rights and uses its secondary user rights to transmit its traffic without delay constraint. During its traffic with delay constraint transmission time, there is no secondary network traffic transmission to avoid harmful interference.
We denote L the set of the different possibilities to N share idle channels among P networks. In this paper, we consider that the number of channels allocation possibilities is not exponential in size. This assumption allows the system to avoid the exponential valuations of network in general, in order to facilitate the computation of our model. Then, depending on its traffic demands, i.e., the volumes of real time and elastic traffic, let 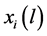 be network’s valuation or utility from the channel allocation
be network’s valuation or utility from the channel allocation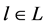 . Therefore, without know any information about others networks transmission patterns a network submits its offers, only based on its expected valuations
. Therefore, without know any information about others networks transmission patterns a network submits its offers, only based on its expected valuations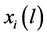 . These expectations are in relation with the actual valuations that it shall probably receive. For the rest,
. These expectations are in relation with the actual valuations that it shall probably receive. For the rest,  must be taken as the network i conjectured valuation or utility for the channel allocation
must be taken as the network i conjectured valuation or utility for the channel allocation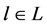 . In the allocation l, these traffic demands may require several sub- carriers on which network i has primary and secondary user rights. So, at the same time, the broker allocates the channel and determines the payment that each network i has to make for different allocations
. In the allocation l, these traffic demands may require several sub- carriers on which network i has primary and secondary user rights. So, at the same time, the broker allocates the channel and determines the payment that each network i has to make for different allocations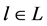 . Then, the following quantity defines the net utility of the network:
. Then, the following quantity defines the net utility of the network:
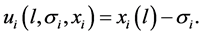 (1)
(1)
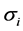 is the amount of money that network i pay to the regulator broker. The social benefits of an allocation are defined to be the quantity
is the amount of money that network i pay to the regulator broker. The social benefits of an allocation are defined to be the quantity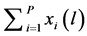 . Thus, the sum of the valuation of all networks gives the social benefits from the allocation l.
. Thus, the sum of the valuation of all networks gives the social benefits from the allocation l.
Considering the concepts of price and social benefits, our auction model could be drive by two main objectives. The first objective is to maximize the income or revenue of the regulator and the second one, is to maximize the social benefits. For this purpose, we assume that 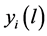 represents in the allocation
represents in the allocation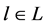 , the offer of network i that is also the money it will pay in the first goal context. And then, for the second goal, it represents the declared valuations of the networks. In these two cases, the channel allocation that maximizes the regulator income or the social benefits of the N bidders, is the allocation
, the offer of network i that is also the money it will pay in the first goal context. And then, for the second goal, it represents the declared valuations of the networks. In these two cases, the channel allocation that maximizes the regulator income or the social benefits of the N bidders, is the allocation 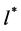 that satisfies the following Equation (2).
that satisfies the following Equation (2).
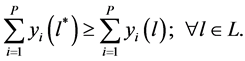 (2)
(2)
So according the objective of the auction, the spectrum sharing problem is to find out the channel allocation that satisfies the Equation (2) within each allocation period. As said above, an allocation period may take about thirty minutes or one hour for instance. Therefore, a bidding algorithm based on the DSAP is introduced here for our auction model. In case of an exponential number of utilities, the network offers are approximately expressed by the language used through our protocol.
3.3. Solution Approach
This section focuses on the solution approaches to our access allocation problem. The proposed solutions must be found for an auction with independent bids. Here, the regulator could conduct an auction for two different goals. As already mentioned, through an auction, the regulator could sell the rights to use the digital dividend in order to maximize its income for a given set of offers. In this case, the channel allocation 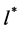 satisfying Equation (2) is chosen when
satisfying Equation (2) is chosen when 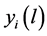 represents the offer of network i.
represents the offer of network i.
In other hand, the regulator has the opportunity to drive the auction in order to achieve efficiency maximizing the social benefits. To reach this second possible objective, each network is asked to declare its utility function, arbitrarily designated by 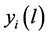 for the network i in accordance withthe allocation. Here, again, we have the channel allocation satisfying the Equation (2) that can be chosen.
for the network i in accordance withthe allocation. Here, again, we have the channel allocation satisfying the Equation (2) that can be chosen.
Each network i offers take the form of a vector





We consider an allocation 










where 

Hence, the solution to the access allocation problem is definitively given by a feasible allocation 

We consider:

as a feasible allocation and L as the set of all feasible allocations.
Now, to consider the financial aspect of the offers and to simplify the implementation of an offer algorithm at each network level, let 




So, we divide the allocation process into two steps: the first allocates the primary rights and the second assigns the secondary rights. Then the revenue of regulator’ broker

where
Finally, the amount of money that network i pay to the regulator broker for an allocation period is:

3.4. Proposed Protocol Description
This current section presents for the auction described above, a protocol (algorithm) to determine an optimal solution to the access allocation problem. Our procedure for bidders to acquire a new lease of spectrum is as follows. In each allocation period, the brokers’ network initiates communication with all bidder networks already registered in the broker’ database through the CCC. This communication is divided into 3 steps listed as follow: 1) the brokers’ network sends a Channel Offer Message; 2) all auctioneer’ networks send their bids according to their needs of spectrum resources through a Channel Requesting Message; 3) the brokers’ network responds with a Channel Acknowledgments Message confirming or denying the channel lease request to all the bidders based on optimization goals, policies, and its Radio Map.
3.4.1. Protocol Structure
Channel Offer Message: Each allocation period starts with a message, called channel offer message, broadcast by the broker to all networks previously registered in his database. This message is divided in five data, consisting of the identifier of the message




Channel Request Message: all bidder networks establish a connection with the respective dedicated broker via a backbone brokers’ network. Networks must be authenticated to each connection to the brokers’ backbone network. There may be more than one DSAP server in the vicinity of a network node (a bidder), to increase robustness for instance. Hence, it is possible that each server makes a Channel Offer to the requesting network node. Therefore it is required that the network node picks only one of these offers for its own use through a Channel Request message to the appropriate DSAP server, thereby implicitly declining offers from all others.
The bidders send a Channel Request Message through a triplet of data. The first data




The offer vector can be formulated as indicated above


Acknowledgments Message: upon reception of the channel request messages, the broker initiates the available spectral resources sharing process based on our optimization goals after the authentication process. The channels sharing procedure is done into two steps: the first step is to eliminate all the bids that do not respect the minimum prices and the second step is to share the available resources between the others networks.
In order to give information about the outcome of the internal process of available resources allocation; finally the DSAP server will respond with a Channel Acknowledgments message confirming or denying the channel lease request to each of the authorized networks that have taken part in the auction. And, a network which has not been authenticated receives a notification indicating an authentication problem. The Channel Acknowledgments message is a triplet of data listed as following: 



We note that the broker keeps track of all transactions in its database. This information will be used to define any royalty payable by networks based on the volume of resources used and their using time.
3.4.2. Algorithm
The algorithm is composed of five main functions. The first function is used to eliminate all the bidders with wrong prices. The second one allows us to organize networks proposals depending on the bids, starting from the highest bid to the lowest. Then, the third and fourth functions assign the right to be respectively primary or secondary user. The main goal of the last function is to estimate the broker revenue.
We present with minimum details in this paper the last three important functions algorithms as follows:
where ALLOC1 is a matrix of 


where NSU is the number of bidder networks requesting the right to be secondary user on a channel.
T1 and T2 are two matrices with 2 columns and respectively 



Figure 3 shows the flow chart of this algorithm.
Figure 3. Algorithm flow chart.
4. Numerical Results
4.1. General Test Configuration
We consider a simple cell in which 

We can also see below, Table 2 and Table 3 respectively show the channel needs and
Table 1. Channel needs and bids of the networks for scenario 1.
a. Network ID represents network identity.
Table 2. Channel needs and bids of the networks for scenario 2.
Table 3. Channel needs and bids of the networks for scenario 3.
offers of the different networks in the scenario 2 and scenario 3. In the scenario 2, we have 

All the information concerning the channel needs and proposed bids of all the bidder networks are loaded in external files of our programme. Therefore, we consider two different files that can be called by the computer program: one containing the bids for primary user rights and the other containing the bids for secondary user rights.
4.2. Results and Discussions
After running the computer program of our DSAP based on the input data given by the previous tables, we obtain the following window in Figure 4. For instance, in the scenario 1, this window gives the number of channel


As it is shown on Figure 4, we have the 5 channels allocation in each of the three scenarios where the column “CHANNEL” gives the channels numbered from 1 to 5. The abbreviation “PU” represents the selected primary user according the network identities defined in the different tables mentioned above. The abbreviations “SU1”, “SU2”, “SU3”, and “SU4” defined the four different secondary networks on each channel.
In this present result explanation, we are going to focus on the first scenario as the three scenarios give substantially the same explanation. For example in the scenario 1, on the channel 1, the network 4 becomes the primary network; the networks 10, 3, 2 and 1 become the secondary users. Hence, the network 10 becomes primary user on channels 3, 4 and 5; and secondary user on the channels 1 and 2. On the channel 3, the networks 3, 2, 8 and 7 become secondary users. On the channel 4, the networks 3, 8, 7 and 9 become secondary users. Finally, on the channel 5, in addition to the network 4 as previously mentioned, the networks 7, 5 and 6 become secondary users. Obviously, all these allocations are based on the different offers of the bidders in order to maximize the income of the broker. And, we can see that the first scenario gives the maximum number of secondary users on each of the 5 channels. We can notice that we have only one primary user on each channel and four secondary networks on all channels. Then, according to Table 1, we remark that networks 10 and 4 proposed the higher bids to get
Figure 4.Result of the allocation procedure for the three scenarios.
a primary user right on a channel. Therefore, there are the only two networks that obtain the primary user rights on three channels for the network 10, and on two channels for the network 4. At the opposite, the networks 4 and 5 proposed the lower bids to get the secondary user rights on a channel. Therefore, they obtain only one channel on which they are secondary networks. Then, it is important to see that networks 4 and 10 are entirely satisfied for their primary user rights demands with respectively two channels requested by network 4 and three channels by network 10. So here, the broker has retained only the two highest proposals, we can imagine, in order to maximize its revenue. In other hand for the secondary user rights demands, networks 1, 2, 3, 5, 7, 8 and 9 are totally satisfied. But, we can observe the lack of two channels for networks 4 and 6; and one channel for network 10. Comparing this result to the Table 1 values, networks 4 and 6 proposed the lowest offers for the secondary user rights. So, it is obvious the reason why these networks have not been entirely satisfied.
Finally, in our test configuration, we can easily say that this channel allocation represents the allocation that maximizes the income of the broker among all the allocation possibilities in which the 

It is also important to precise that the allocation is only for one allocation period and in each allocation period of a day for example, the broker has the possibility to set the minimum prices for the primary and secondary use on the different channels. In this way, the algorithm is very flexible and the broker can set the minimum prices regarding the usual allocation periods with or without lot of traffic demands.
In addition to the explanation provided for the first scenario, in the second scenario, the number “0” mentioned for secondary user (US 4) on the channel 5, means that there is no fourth secondary network on this channel. This is simply because of lack of secondary user right demand. We have the same example in the scenario 3 on the five channels. On the channel 1, 2 and 4, we have three secondary networks less than the maximum allowed number of secondary networks. On the channel 3, we obtain two secondary networks and on the channel 5, only one secondary network.
Despite Table 2 for the scenario 2 shows twelve bidders, we remark only ten selected networks; it means that two of them have been eliminated by the algorithm surely because they proposed offers inferior to the minimum prices set by the broker as we can see in Figure 5 for the primary user rights offers and in Figure 6 for the secondary user rights offers. In fact Figure 5 shows the ten networks selected accordingly to their offers that are superior or equal to the minimum primary user price set by the broker. Indeed, for the scenario 2, networks 8 and 12 have not been selected and this corresponds to the lowest values proposed by these two networks for the primary user rights. In the scenario 3, all the four networks have been retained as selected bidders for the primary user rights. This scenario may correspond for example to an allocation period where there is no enough traffic transmission requests.
At the level of secondary user rights, in scenario 2, networks 11 and 12 have not been retained by the broker, while in the scenario 3, all the four networks have been selected. Regarding the offers’ table of the scenario 2, networks 11 and 12 suggested the lowest values. Yet, we can say it is obvious that the broker has no selected these two networks.
After the elimination of networks with proposed offers strictly less than the minimum primary and secondary prices, the algorithm reorganizes the network numbering starting with the number 1. That is why we can notice in the rest of the results that networks are renumbered from 1; of course the algorithm is able to recognize all the bidder networks and sends the right Acknowledgments Message to the right network.
Figure 5. Curves of the selected primary user networks for the three scenarios.
Figure 6. Curves of the selected secondary user networks for the three scenarios.
Figure 7 shows the curves giving the revenue of the broker in the previous channels allocation for the three scenarios. The red curve represents the evolution of the revenue of the broker according to the number of secondary networks for the scenario 1 and the blue curve for the scenario 2; then the green curve for the scenario 3. All these curves increase with the number of secondary networks. We precise that we have only one primary network on each channel and when the number of secondary networks increase, the revenue of the broker also increase for all the three scenarios. We observe the saturation of the green curve from three secondary networks because in the scenario
Figure 7. Broker’s revenue based on the number of secondary user networks on a channel.
3, the number of networks for the secondary use of the channels is less than the maximum allowed number of secondary networks.
Finally, we remark that the broker maximizes its revenue when the maximum allowed number of secondary networks on each channel is reached.
5. Conclusions and Perspectives
We describe in this paper a simple dynamic spectrum access protocol (DSAP) that can be used to find out a suitable solution to the problem of access allocation mentioned here for the use of digital dividend. The numerical results presented in Section 5 allow us to conclude that our proposed protocol is viable regarding the spectrum scarcity.
This paper opened two main problems that we can focus on for our future work. We worked with N orthogonal and identical channels, but the non-identical channels case shall be a new configuration of our problem which must be solved. Finally, we mentioned the case of several DSAP servers in the vicinity of a network node and we required that the network node picks only one of their offers. The procedure of choosing one offer also remains an open problem.
Acknowledgements
We cannot express enough thanks to the research department of ESATIC for their continued support and encouragement: Dr. Francklin Kouassi and Pr. Olivier Asseu, the Chief of the department. We offer our sincere appreciation for the collaboration opportunities provided by this department.
Cite this paper
Zamblé, R., Gbégbé, R., Kadjo, J.-M., Asseu, O. and Brou, P. (2016) Dynamic Spectrum Access Protocol for the Digital Dividend. Circuits and Systems, 7, 4124-4144. http://dx.doi.org/10.4236/cs.2016.713340
References
- 1. Kaur, M.J., Uddin, M. and Verma, H.K (2012) QoS Provisioning of Cognitive Radio Using Soft Computing Techniques—A Survey. International Journal of Computational Intelligence and Information Security, 3, 51-63.
- 2. Reed, D.P. (2003) Bits Aren’t Bites: Constructing a “Communications Ether” That Can Grow and Adapt. International Symposium on Advanced Radio Technologies (ISART), Boulder, 4 March 2003, 39-46.
- 3. OFcom (2004) A Guide to the Spectrum Framework Review.
- 4. Ghosh, G., Das, P. and Chatterjee, S. (2014) Cognitive Radio and Dynamic Spectrum Access—A Study. International Journal of Next-Generation Networks, 6, 43-60.
http://dx.doi.org/10.5121/ijngn.2014.6104 - 5. Zhao, Q. and Sadler, B.M. (2007) A Survey of Dynamic Spectrum Access. IEEE Signal Processing Magazine, 24, 79-89.
http://dx.doi.org/10.1109/MSP.2007.361604 - 6. Ren, P., Wang, Y., Du, Q. and Xu, J. (2012) A Survey on Dynamic Spectrum Access Protocols for Distributed Cognitive Wireless Networks. EURASIP Journal on Wireless Communications and Networking, 2012, 60.
http://dx.doi.org/10.1186/1687-1499-2012-60 - 7. Liu, C. (2009) Spectrum Sharing in Dynamic Spectrum Access Networks: WPE-II Written Report. Technical Report Available at Scholarly Commons.
- 8. Gandhi, S., Buragohain, C., Cao, L., Zheng, H. and Suri, S. (2008) Towards Real-Time Dynamic Spectrum Auctions. Computer Network, 52, 879-897.
http://dx.doi.org/10.1016/j.comnet.2007.11.003 - 9. FCC Auctions.
http://wireless.fcc.gov/auctions - 10. Buddhikot, M.M., Kolodzy, P., Miller, S., Ryan, K. and Evans, J. (2005) DIMSUMNet: New Directions in Wireless Networking Using Coordinated Dynamic Spectrum Access. 6th IEEE International Conference on a World of Wireless Mobile and Multimedia Networks (WoWMoM), Taormina, 16 June 2015, 78-85.
http://dx.doi.org/10.1109/WOWMOM.2005.36 - 11. Office of Communications (Ofcom) (2007) A Study into Dynamic Spectrum Access—Final Report. Report No. 72/06/R/353/U, London, England.
- 12. Amitay, N. and Greenstein, L.J. (1994) Resource Auction Multiple Access (RAMA) in the Cellular Environment. IEEE Transactions on Vehicular Technology, 43, 1101-1111.
http://dx.doi.org/10.1109/25.330174 - 13. Kock, C., Jaekel, H. and Jondral, F. (2005) Auction Sequence as a New Resource Allocation Mechanism. 61st Vehicular Technology Conference (VTC), 1, 240-244.
- 14. Grandblaise, D., Moessner, K., Vivier, G. and Tafazolli, R. (2006) Credit Token Based Rental Protocol for Dynamic Channel Allocation. 1st International Conference on Cognitive Radio Oriented Wireless Networks and Communications (CrownCom), Mykonos Island, 8-10 June 2006, 1-5.
- 15. Weiss, T.A. and Jondral, F.K. (2004) Spectrum Pooling: An Innovative Strategy for the Enhancement of Spectrum Efficiency. IEEE Communications Magazine, 42, S8-S14.
http://dx.doi.org/10.1109/mcom.2004.1273768 - 16. Huang, J.W., Berry, R.A. and Honig, M.L. (2006) Auction-Based Spectrum Sharing. Mobile Networks and Applications, 11, 405-418.
http://dx.doi.org/10.1007/s11036-006-5192-y













