Applied Mathematics
Vol.05 No.02(2014), Article ID:42160,14 pages
10.4236/am.2014.52026
Reliable Network Design Problem under Node Failure with Benders Decomposition
Tie Liu1, Wenguo Yang2*, Jun Huang1
1College of Engineering, University of Chinese Academy of Sciences, Beijing, China
2School of Mathematics Sciences, University of Chinese Academy of Sciences, Beijing, China
Email: *yangwg@ucas.ac.cn, liutie_@126.com
Copyright © 2014 Tie Liu et al. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. In accordance of the Creative Commons Attribution License all Copyrights © 2014 are reserved for SCIRP and the owner of the intellectual property Tie Liu et al. All Copyright © 2014 are guarded by law and by SCIRP as a guardian.
ABSTRACT
Received June 15, 2013; revised July 15, 2013; accepted July 23, 2013
The design of telecommunication network with capacity constraints of links, routers and ports of routers is considered in this paper. Specially, we limit each demand flow traversed through a pre-specified maximal number of links (called hops) under node failure scenarios in IP layer network. Such a design must be the most cost-effec- tive and ensure that feasible flows continue to exist even when any relay node of the network fails. We propose a reliable mixed-integer programming (MIP) model with multi-scenario constraints to optimally design a mini- mum-cost survivable IP network that continues to support a good communication under any node failure scena- rio. Then we transform the MIP model into many single scenario models, that is, simplified MIPs, nonlinear programming (NLP) models and MIP models under Benders decomposition Then we transform the MIP model into many single scenario models, that is, simplified MIPs, nonlinear programming (NLP) models and MIP mod- els under Benders decomposition. Three heuristic methods are proposed to solve these models including branch-and-bound algorithm, global algorithm for NLP, and heuristic algorithm based on benders decomposition. We mainly study the application of Benders decomposition method, where dual model and bounding procedures are given for each MIP model under Benders decomposition at each scenario. The results of our computational experiments validate the effectiveness of the proposed models and algorithms.
Keywords:
Mixed-Integer Programming; Benders Decomposition; Network Design; Node Failure
1. Introduction
Network design problems [1-3] involve a number of applications including logistics, power systems, transporta- tion, telecommunication and military scenarios. The idea is to establish a network of links (roads, bridges, air- lines, optical fibers, electric lines, etc.) that enables the flow of commodities (people, rescue materials, data packets, electricity, etc.) in order to satisfy some demand characteristics like minimum cost. In addition, the idea con- taining design of survivable or reliable networks has become a major objective for telecommunication operators [4,5].
Telecommunication network has been developed rapidly in China with the characteristics of more complex flow, wider bandwidth, and higher level of QoS (quality of service) in recent years. Network survivability is de- fined as the ability of a network to maintain its communication capabilities in the face of equipment failure [6]. In most cases, it means that a network is still functional after the failure of certain network components like node failure. In this paper, we treat the concept of reliability the same as survivability. Take IP-over-WDM network in telecommunication as an example, IP layer nodes employ optical cross-connects and IP routers and they are connected by fibers to form a mesh topology. Unlike physical layer, an important and special case in IP layer
is that IP nodes are more vulnerable than the links. A common reason for interrupted connections with node failures is caused by hardware failures or by an overloaded network. A node has to cope with more traffic than it is able to handle [7], and it usually happens in uncertain issues such as disruptions from disasters. So contin- gency plans for providing relief to affected areas in IP network design need to consider the potential failure of certain vulnerable nodes. Many measures have been taken like installing redundant communication lines and connecting equipment, design node-disjoint (and edge-disjoint) path [8] or enough link capacity [9]. And there have been lots of researches on the related issues.
The main contributions of this paper can be summarized as follows. First, we provide a reliable mixed-integer programming model for telecommunication network design problem from a more practical point of view. Al- though the model has been designed to be mostly technology-independent for a single layer IP network, it can be extended easily with practical needs.
Second, according to origin model, we transformed it to other three mathematical models including simple MIP model, NLP model, and MIP model with Benders decomposition form.
Third, we present various model-specific algorithms including branch-and-bound algorithm, global algorithm for NLP, and heuristic algorithm based on benders decomposition, and compare them by looking at the results and computing time. Meanwhile, we show that our methods are effective by comparing the price of robustness between our methods and the method using 1 + 1 dedicated path protection, and highlight the performance of the heuristic algorithm based on benders decomposition and the gap design is influenced by convergence of Benders algorithm bounds.
The remainder of the paper is organized as follows. In Section 2, we review the related literature. We then define our problem and build a reliable network design model and some smart model transformations in Section 3. In Section 4, a heuristic algorithm is developed based on benders decomposition, followed by computational re- sults in Section 5 and conclusions in Section 6.
2. Literature Review
As stated in the introduction, design of survivable or reliable networks has been addressed by a number of researchers and the network design problem considering reliability constraints is NP-hard [4,5]. Soni provided a classification scheme as physical survivability and logical survivability and further classification within each group. Actually, logical survivability would be achieved if and only if the underlying physical network was survivable. In order to handle the reliable problem, protection schemes have been proposed mainly in three aspects including dedicated path protection, shared path protection and demand-wise shared protection [10,11]. These schemes are different within measures like good reaction times, good bandwidth requirements and simple network management.
In particular, some authors used failure probability as the factor of reliability [8] and some used scenario-base failure without probability factor to support robust solutions [6,9]. For simplicity, it usually makes sense to try and protect the network against single link or single node failures only [6,7,9,12]. And it can be expand to the general scenarios of arbitrary set of failure configurations, including multiple link and node failures. Our paper concentrates on single node failure. A node represents equipment, such as a switch or router. The diameter bound, also called “hop constraints”, ensures efficient use of node resources and limits the maximum delay, which is usually used as a surrogate for service restrictions. The node degree bound models the limited number of physical ports on a node, which often has capacity constraints. Therefore, more and more papers have focused on hop constrained network design problem [13,14] and capacitated network design problem [7,9,15].
Uncertainty in the traffic requirements is an important factor that affects reliable network design, and we must take it into account. Lots of researchers have studied the network design with demand uncertainty [15-20]. Alper [18] allows one to control conservatism of the solutions by means of an allowed “budget for demand uncertainty.” The idea is robust optimization, which was first proposed by Soyster [21]. In our reliable network design, we consider the worst node failure scenario and try to get the robust solutions.
Our problem is very closely related to the well-known hub location problem [22-25], but differs in the fact that the demand nodes can communicate with each other directly and we consider more constrains together in the model such as various capacity constraints and hop constraints. On the other hand, hierarchical or layered topological network design [26-28] is common in real telecommunication networks. But we concentrate IP layer for simplicity and consider multi-layer network design later.
Network design problems are usually modeled as mixed-integer programming formulation or two-stage mixed-integer program formulation. The models are often large-scale and hard to solve. Many solution approaches or heuristics have been proposed for these problems in recent years, such as Benders decomposition
[29-33], branch and bound, branch and cut, branch cut and price, column generation, Lagrangian relaxation, dy- namic programming and so on. Benders [29] proposed benders decomposition methods first for solving mixed variables programming problems followed by many researchers. In Section 4, we prefer Benders decomposition for structured optimization.
3. Reliable Network Design Model
The network design problem that we consider examines the network as a graph with a set of nodes and potential links. The nodes are divided into two types, demand nodes as a set of communication pairs (or origin-destination pairs) and relay nodes with fixed router construction cost and port cost in the router. Every origin-destination pair has a flow demand and the hop constraint. Associated with each link is a construction cost and a capacity. Meanwhile, we consider the failure of any potential relay node that may necessarily render the remaining operational links incapable of transmitting the information flow and we denote such a situation with a failing node as a failure scenario. So the aim of this article is to build a reliable network design model to minimize network construction cost with node failure scenarios and develop heuristic algorithms to get robust solutions. The robust solutions contain the number of ports of every router (that is relay node), whether link is established, and the amount of flow of every link.
3.1. Notation and Model Parameters
First of all, we define a network in telecommunication with parameters as follows:
 : A graph
: A graph 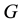 standing for the IP network with node set
standing for the IP network with node set and potential directed link set
and potential directed link set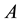 .We substitute
.We substitute 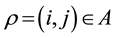 where convenient in this discussion.
where convenient in this discussion.
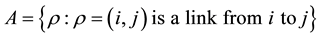
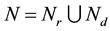 ,
, 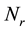 denotes a set of relay nodes,
denotes a set of relay nodes, 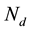 denotes a set of demand nodes
denotes a set of demand nodes
 is a set of origin-destination pairs, and
is a set of origin-destination pairs, and 
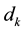 : The amount of flow demand for the kth pair from
: The amount of flow demand for the kth pair from  to
to 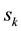
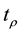 : The capacity of link
: The capacity of link 
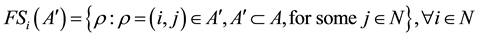 is the set of links in
is the set of links in 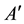 that exit node
that exit node 
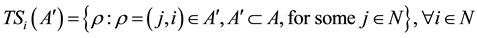 is the set of links in
is the set of links in 






The decision variables in our models are as follows:









3.2. The Basic Model
With the above parameters, the model of our original problem can be stated as follows:












The objective function (1) serves to minimize the total cost of constructing routers and flows of links, in which parameter 



Remark 1. The model (1) above considers a reliable telecommunication network design problem. Its advantage is that the reliable flow allocation is designed in advance with the possible failure nodes. Under the design, the network operates with little jitter or delay connection specially when there is enough bandwidth. Survivable network design deals with the problem of designing telecommunication networks that can survive a specified number of node or link failures. Although considering failure with only one relay node here, it can be applied to the occasion that a set of nodes or arcs could simultaneously fail.
3.3. Model Transformation
The Model (1) is a large-scale mixed-integer programming problem, and the variables contain binary variables, integer variables and continuous variables. Overall, there are 






Proposition 1 Model (1) is a multi-scenario model and can be transformed to many simplified single scenario model (2) for every scenario









Proof Since 




from model (1) where its value can be deduced from



approximately to Model (3) with the same optimal solutions as follows:









In model (3), 


“

Here the simplified form of model (1) is obtained, and it is a mixed integer programming model with decision variables 

Remark 2 The MIP model (2) has either detected infeasibility or has an optimal solution to the original problem and gets its optimal solution on the extreme points.
Notice that the model (2) is a multi-commodity flow problem with hop constraints from actual telecommunication background. If it has feasible solutions, the feasible solution region is a bounded polyhedral region. So it will get its optimal solution on the extreme points to make the minimum total cost. Otherwise, the problem is infeasible because of limited capacity and hops or other conditions.
We can also transform the MIP model (2) into a nonlinear programming model with only one decision variables 


equals

and we note it as NLP model:







4. Heuristic Algorithms
The algorithmic approaches apply robust ideas such as using a worst-case approach, and this idea is often useful in practice. Initial results on robust linear optimization were given by Soyster in [21]. His model is equivalent to the LP in which all uncertain parameters have been fixed at their worst-case values from the uncertainty set. However, our model has the uncertain parameter of node failure which may influence flow allocation. We can choose uncertain part of node failure scenarios but not all of the node failure necessarily. To avoid considering the probability of choosing node failure, we consider every node failure scenario.
Here we propose three methods to solve the model (2). First, solve it directly with branch-and-bound algorithm provided by lingo or Xpress optimizer software. Second, it can be transformed to model (4) and solve model (4) with global algorithm by the similar software. Third, we can employ a Benders decomposition approach [29] which may get solutions more effectively. As Benders decomposition approach is concerned, it is a classical method for combinatorial optimization problem, especially mixed integer programming model, such as routing, distribution and location problems. It begins by partitioning the model to be solved into two simpler problems, named master problem and sub-problem [31]. The master problem is a relaxed version of original problem, containing only a subset of the original variables and the associated constraints. The sub-problem is the dual problem of original problem with the variables obtained in the master problem fixed. Specifically, we can divide the variables of a problem into two vectors 





4.1. Heuristic Algorithms to Solve Model (2) and Model (4) Directly
Since model (2) and model (4) has the similar basic process to solve except the inner algorithm in Lingo, we describe them in the same framework here.
Initialization: Set iteration counter


Step 1: Choose a scenario w satisfying 





Step 2: If
Step 3: We obtain the final optimal solution 

The Algorithm will be executed 



4.2. Heuristic Algorithm Based on Benders Decomposition to Solve Model (2)
In the MIP model (2), 









Where
The inner minimization model (5) is a linear program. For a given value 

















Since the original problem has optimal solution if it is feasible, and then by duality theory of linear programming, we have:

Using the partitioning and delayed constraint generation ideas [30], we can now decompose model (2) into two small problems referred to as the Benders sub-problem (SP) and the Benders relaxed master problem (MP), in that, SP and MP will be employed for computing upper bound UB and lower bound LB on model (2) in an iterative procedure called the Benders algorithm.
Here SP for every scenario 

Next, let 






where 


To obtain optimal solution of model (9), consider only the extreme points and extreme rays that will be generated one-by-one by solving SP. If SP is feasible and bounded, one can identify an optimal extreme point

where 


then add constraint (9b) to MP and re-solve MP. However, to find the extreme rays in practice is often difficult. A method is to solve the auxiliary sub-problem AP [32], which is the same as SP except that the objective function of model (6) set to zero, and the right side of the constraints (6a)-(6c) are forced to be zero, that is

However, when model (6) has an unbounded solution, that is we find an extreme ray, we often don’t find the extreme ray in practical operation, but adopt to add the following constraint to model (6) that assures a bounded solution:

where 
In order to reduce running time to solve Model (2) with benders decomposition, and get an acceptable solution, we define the relative gap of our algorithm:

This gives the accuracy of the approximation for the optimal solution value, which provides a stopping criterion or convergence criterion of iterative algorithms. Then start with a partial network solution from the current network design, and add arcs to the network as necessary until a feasible solution is obtained. Although we need not get extreme ray in our problem, we write the entire frame of the algorithm in favor of algorithm expansions. The heuristic algorithm based on the Benders decomposition is given as follows.
Algorithm: Heuristic algorithm based on benders decomposition
So the optimal solutions of the original model (1) are:
The algorithm is provably finite. When our problem has feasible solutions, it results in the optimal solution and at any time during its execution lower and upper bounds on the optimal solution of the original MP can be obtained. In our implementation, the heuristic will follow the detail steps in the reference of multiple models and parallel solving with Mosel [32].
5. Computational Experiments
We propose three methods to solve three transformations of the same model of our problem in telecommunication background, and they are the branch-and-bound algorithm provided by Lingo9.0 used in the MIP model (BBMIP), global algorithm provided by Lingo9.0 used in the NLP model (GNLP) and the heuristic algorithm based on benders decomposition applied in the MIP model (BDMIP). The BDMIP is implemented with Mosel in Xpress-ive and solved with Xpress optimizer (version 19.00). All results are collected on a Dell computer with 2.0 GB memory and 2.93 GHz dominant frequency. Here let’s compare them by looking at the results and computing times (in CPU seconds).
Considering a random example as Figure 1 illustrated. Here we compare the methods by looking at the processes and results, including solver iterations. 








Case 1:


In this simple instance, the results in Table 2 demonstrate different solver iterations for different methods, and they can get the same objective values and robust solutions. The program execution time of each method is very little, but we can see the BBMIP has the fewest solver iterations.
In order to show the price of robustness with our method is acceptable, we can compare our reliable protection (called “reliable node failure protection”) with the method using 1 + 1 dedicated path protection [12,13].
To ensure service connectivity in case of single network element failures, two link- or node disjoint paths (depending on planning requirements) are set up for 1 + 1 dedicated path protection. The signal is broadcasted over both the working and the backup path simultaneously. In case of a single link or node failure, the sink of the demand still receives a copy of the data from one of the two paths.
If we don’t consider the node failure scenario, that is no node of the network will fail, then the results of this case can be computed from our model (2) without the factors of node failure scenarios. We list the objective value of original model with 1 + 1 dedicated path protection and with reliable node failure protection in the last row of Table 2, from which we can compare total cost of the telecommunication network design problem and the price of robustness. Here we note “objective value of original model with reliable node failure protection” as OV1, and note “objective value of original model 1 + 1 dedicated path protection” as OV2. The savable price of
Figure 1. Illustration of a simple network structure.
Table 1. Cost of flow on arc (i, j).
network is noted as SPN, and it equals (OV2-OV1)/OV1.
For the BDMIP, when experimented on this illustrative example of node E failure, it converged to the optimal solution in 46 iterations. The convergence of the algorithm and the bounds obtained at each iteration are illustrated in Figure 2. The final network topology from this example is shown in Figure 3.
Case 2:


For the purpose of demonstrating the influence of numbers of demands, we consider more demands than Case 1 and the results are displayed in Table 3, Figures 4 and 5. By comparing Case 1 and Case 2, we can observe that the methods with the increasing speed of solver iterations from low to high are BBMIP, GNLP and BDMIP respectively. For the savable price robustness, the value is 21.8% in case 1% and 4.3% in Case 2 which guarantee the reliability of the network and save more price of the network than that of the 1 + 1 dedicated path protection.
Table 2. Results in Case 1.
Figure 2. Convergence of Benders algorithm with node E failure in Case 1.
Figure 3. Solution for Case 1.
Table 3. Results in Case 2.
Figure 4. Details for Case 2.
Figure 5. Solution for Case 2.
Since the CPU time to solve the model (2) with BDMIP mainly depends on the numbers of the master problem [8], and solving the master problem will spend more and more time as the solver iterations increase,. This can be seen clearly in Figure 6. So we must decrease the solver iterations by making the Gap > 0 and permit an approximate solution.
Here we compare the different Gap to allow the approximate solutions with BDMIP in Table 4. A very important observation from the results is that the value to set the Gap is influenced by convergence of Benders algorithm bounds which is partly shown in Figures 7 and 8.
For example, by examining the results for node E failure in Case 2, the Gap equals 0.05 and the Gap equals 0.1 make no difference at the iterations. That’s because the lower bound and the upper bound of Benders algorithm here at the 281st iteration is very close. But for node F failure, the gap is enough small until the algorithm iterate constantly to get optimal solution.
6. Concluding Remarks
Our models are to obtain a minimum cost network with some flow constraints, capacity constraints and especially hop constraints under uncertain node failure scenario. This is in fact a network design problem in telecommunication background which can be formulated as mixed integer programming models and can also be transformed to other mathematical models. Many other practical applications such as logistics, power systems, and transportations can be abstracted as similar network design problems. The idea of reliability or survivability is applied to the network design problem which is mainly embodied in considering the node failure scenarios here. We propose three methods including BBMIP, GNLP and BDMIP with a worst-case idea behind robust op- timization. And mainly study the Benders Decomposition for our model. Our computational experiments have indicated that Benders decomposition is an efficient method for solving network design problems, and can be controlled more easily than traditional techniques such as Branch-and-Bound, Lagrangian relaxation or global non-linear algorithms.
There are several variations and extensions of this work that could be considered for future research. In addition to the two extensions of our model in Remark 1 in Section 2.2, we can find some extensions of our problem. First, we study the network reliability under certain demands, but uncertain demands need to be considered. Se- cond, in the context of emergency service deployment, disasters such as earthquakes may damage several com- municational device nodes or links. Multi-link failures or failures of both links and nodes are difficult to handle in modeling and computing. For these difficult and practical problems, effective and efficient algorithms like Benders decomposition or combining Benders decomposition with other techniques are urgently needed.
Acknowledgements
We would like to thank Jiye Han very much for his constructive remarks and suggestions. This work is sup-
Figure 6. Time performance of BDMIP with node E failure in Case 2―Running time, (s).
Figure 7. Convergence of Benders algorithm with node E failure in Case 2.
Figure 8. Convergence of Benders algorithm with node F failure in Case 2.
Table 4. Results with different gap for BDMIP.
ported by National Natural Science Foundation of China (No:71171189, No:71271204, No:11101420) and Knowledge Innovation Program (No:KGCX2-RW-329) of the Chinese Academy of Sciences.
References
- M. Minoux, “Network Synthesis and Optimum Network Design Problems: Models, Solution Methods and Applications,” Network, Vol. 19, No. 3, 1989, pp. 313-360.
- S. Alumur and Bahar Y. Kara, “Network Hub Location Problems: The State of the Art,” European Journal of Operational Research, Vol. 190, No. 1, 2008, pp. 1-21.
- M. Abd-El-Barr, “Topological Network Design: A Survey,” Journal of Network and Computer Applications, Vol. 32, No. 3, 2009, pp. 501-509. http://dx.doi.org/10.1016/j.jnca.2008.12.001
- S. Soni, H. Pirkul and R. Gupta, “Survivable Network Design: The State of the Art,” Information Systems Frontiers, Vol. 1, No. 3, 1999, pp. 303-315. http://dx.doi.org/10.1023/A:1010058513558
- H. Kerivin and A. R. Mahjoub, “Design of Survivable Networks: A Survey,” Research Report LIMOS/RR-05-04, 2005, pp. 1-21.
- M. Garg and J. C. Smith, “Models and Algorithms for the Design of Survivable Multi-Commodity Flow Networks with Gener- al Failure Scenarios,” Omega, Vol. 36, No. 6, 2008, pp. 1057-1071. http://dx.doi.org/10.1016/j.omega.2006.05.006
- S. Orlowski, “Local and Global Restoration of Node and Link Failures in Telecommunication Networks,” Master’s Thesis, Fachbereich Mathematik der TU, Berlin, 2003.
- J. Desai and S. Sen, “A Global Optimization Algorithm for Reliable Network Design,” European Journal of Operational Re- search, Vol. 200, No. 1, 2010, pp. 1-8. http://dx.doi.org/10.1016/j.ejor.2008.12.016
- T. Liu, W. G. Yang, J. X. Liao and J. Huang, “Robust Optimization for Designing Reliable Telecommunication Networks with Node Failure Scenarios,” 2010 IEEE International Conference on Emergency Management and Management Sciences (ICEMMS 2010), pp. 218-221.
- C. G. Gruber, et al., “A New Model and a Computational Study for Demand-Wise Shared Protection,” Berlin-Dahlem, ZIB- Report, 2005, p. 55.
- R. Hulsermann, et al., “Availability and Cost Based Evaluation of Demand-Wise Shared Protection,” Berlin-Dahlem, ZIB- Report, 2006, p. 15.
- E. Rosenberg, “Hierarchical Topological Network Design,” IEEE/ACM Transactions on Networking, 2005, pp. 1402-1409. http://dx.doi.org/10.1109/TNET.2005.860100
- S. Soni, “Hop Constrained Network Design Problem with Partial Survivability,” Annals of Operations Research, Vol. 106, No. 1-4, 2001, pp. 181-198. http://dx.doi.org/10.1023/A:1014513809519
- A. Balakrishnan and K. Altinkemer, “Using a Hop-Constrained Model to Generate Alternative Communication Network De- sign,” ORSA Journal on Computing, Vol. 4, No. 2, 1992, pp. 192-205. http://dx.doi.org/10.1287/ijoc.4.2.192
- R. Andrade, A. Lisser, N. Maculan and G. Platfau, “Telecommunication Network Capacity Design for Uncertain Demand,” Computational Optimization and Applications, Vol. 29, No. 2, 2004, pp. 127-146. http://dx.doi.org/10.1023/B:COAP.0000042027.65400.b3
- O. E. Flippo, A. W. J. Kolen, et al., “A Dynamic Programming Algorithm for the Local Access Telecommunication Network Expansion Problem,” European Journal of Operational Research, Vol. 127, No. 1, 2000, pp. 189-202. http://dx.doi.org/10.1016/S0377-2217(99)00340-9
- M. Riis and K. A. Andersen, “Multi-Period Capacity Expansion of a Telecommunications Connection with Uncertain Demand,” Computers & Operations Research, Vol. 31, No. 9, 2004, pp. 1427-1436. http://dx.doi.org/10.1016/S0305-0548(03)00098-4
- A. Atamtürk and M. Zhang, “Two-Stage Robust Network Flow and Design under Demand Uncertainty,” Operations Research, Vol. 55, No. 4, 2007, pp. 662-673. http://dx.doi.org/10.1287/opre.1070.0428
- Y. F. Yin, S. M. Madanat and X.-Y. Lu, “Robust Improvement Schemes for Road Networks under Demand Uncertainty,” Eu- ropean Journal of Operational Research, Vol. 198, No. 2, 2009, pp. 470-479. http://dx.doi.org/10.1016/j.ejor.2008.09.008
- S. E. Terblanche, R. Wessäly and J. M. Hattingh, “Survivable Network Design with Demand Uncertainty,” European Journal of Operational Research, Vol. 210, No. 1, 2011, pp. 10-26. http://dx.doi.org/10.1016/j.ejor.2010.09.041
- A. L. Soyster, “Convex Programming with Set-Inclusive Constraints and Applications to Inexact Linear Programming,” Oper- ations Research, Vol. 21, No. 5, 1973, pp. 1154-1157. http://dx.doi.org/10.1287/opre.21.5.1154
- E. A. Cabral, E. Erkut, G. Laporte and R. A. Patterson, “The Network Design Problem with Relays,” European Journal of Ope- rational Research, Vol. 180, No. 2, 2007, pp. 834-844. http://dx.doi.org/10.1016/j.ejor.2006.04.030
- I. Rodríguez-Martín and J. J. Salazar-González, “Solving a Capacitated Hub Location Problem,” European Journal of Opera- tional Research, Vol. 184, No. 2, 2008, pp. 468-479. http://dx.doi.org/10.1016/j.ejor.2006.11.026
- I. Contreras, J. A. Díaz and E. Fernández, “Lagrangean Relaxation for the Capacitated Hub Location Problem with Single As- signment,” OR Spectrum, Vol. 31, No. 3, 2009, pp. 483-505. http://dx.doi.org/10.1007/s00291-008-0159-y
- I. Contreras, J. F. Cordeau and G. Laporte, “Benders Decomposition for Large-Scale Uncapacitated Hub Location,” Cirrelt, Cirrelt-2010-26, 2010, pp. 1-43.
- E. Rosenberg, “Hierarchical Topological Network Design,” IEEE/ACM Transactions on Networking, Vol. 13, No. 6, 2005, pp. 1402-1409. http://dx.doi.org/10.1109/TNET.2005.860100
- I. Gódor and G. Magyar, “Cost-Optimal Topology Planning of Hierarchical Access Networks,” Computers & Operations Re- search, Vol. 32, No. 1, 2005, pp. 59-86. http://dx.doi.org/10.1016/S0305-0548(03)00202-8
- T. Thomadsen and T. Stidsen, “The Generalized Fixed-Charge Network Design Problem,” Computers & Operations Research, Vol. 34, No. 4, 2007, pp. 997-1007. http://dx.doi.org/10.1016/j.cor.2005.05.021
- J. F. Benders, “Partitioning Procedures for Solving Mixed Variables Programming Problems,” Numerrische Mathematik, Vol. 4, No. 1, 1962, pp. 238-252. http://dx.doi.org/10.1007/BF01386316
- R. M. Freund, “Benders’ Decomposition Methods for Structured Optimization, including Stochastic Optimization,” Massachusetts Institute of Technology, 2004.
- A. M. Costa, “A Survey on Benders Decomposition Applied to Fixed-Charge Network Design Problems,” Computers & Operations Research, Vol. 32, No. 6, 2005, pp. 1429-1450. http://dx.doi.org/10.1016/j.cor.2003.11.012
- Y. Colombani and S. Heipcke, “Multiple Models and Parallel Solving with Mosel,” Xpress Team, FICO, Leam House, Leamington Spa CV32 5YN, 2008. http://www.fico.com/xpress
- O. Çakır, “Benders Decomposition Applied to Multi-Commodity, Multi-Mode Distribution Planning,” Expert Systems with Applications, Vol. 36, No. 4, 2009, pp. 8212-8217. http://dx.doi.org/10.1016/j.eswa.2008.10.037
NOTES
*Corresponding author.



















