Journal of Quantum Information Science
Vol.06 No.04(2016), Article ID:72889,8 pages
10.4236/jqis.2016.64018
A Simple Security Proof for Entanglement-Based Quantum Key Distribution
Mhlambululi Mafu
Department of Physics and Astronomy, Botswana International University of Science and Technology, Palapye, Botswana

Copyright © 2016 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY 4.0).
http://creativecommons.org/licenses/by/4.0/



Received: September 27, 2016; Accepted: December 18, 2016; Published: December 21, 2016
ABSTRACT
Quantum cryptography exploits the quantum mechanical properties of communication lines to enhance the security of the so-called key distribution. In this work, we explain the role played by quantum mechanics in cryptographic tasks and also investigate how secure is quantum cryptography. More importantly, we show by a simple security proof that for any state sent by the sender, the eavesdropper can only guess the output state with a probability that will allow her not to learn more than half of the classical Shannon information shared between the legitimate parties. This implies that with high probability, the shared key is secure.
Keywords:
Quantum Key Distribution, Simple Security Proof, Entanglement-Based, Quantum Cryptography, Polarisation

1. Introduction
Quantum key distribution (QKD), one aspect of quantum cryptography, provides a secure method for distributing cryptographic keys between two parties conventionally known as Alice (sender) and Bob (receiver), who are connected by a quantum channel and an authenticated classical channel in the presence of an extremely competent malicious party, an eavesdropper, Eve [1] . The security of a QKD protocol is mainly based on the laws of quantum mechanics, which state that (1) one cannot make a measurement without perturbing the system unless the quantum state is compatible with the measurement. If there is no disturbance in the system, then no measurement was made, which implies that there was no eavesdropping. Therefore, Eve cannot intercept the information being transmitted in the communication channel without introducing disturbances that would reveal her presence; this is also known as quantum indeterminacy; (2) it is impossible to duplicate an unknown quantum state with perfect fidelity. This means that Eve cannot intercept the channel and get hold of the quantum system, make a copy of the system and send the copy to Bob without being detected. Therefore, quantum mechanics guarantees that two parties can exchange a secret key securely because the key always remains uncompromised. However, the security of QKD is guaranteed providing that the implementation is perfect i.e. all parties perform as expected or provided; all the imperfections of the implementation have been correctly characterised.
Based on Wiesner’s idea of conjugate coding [2] , Bennett and Brassard in 1984 proposed a first established and operable QKD protocol now commonly known as the BB84 protocol [3] . In 1991, Ekert [4] extended the idea by introducing quantum entanglement and the violation of Bell’s theorem [5] . Since then, several protocols have been proposed by both theorists and experimentalists. These include: Bennett 1992 (B92) [6] , six state [7] ; Phoenix, Barnett and Chefles 2000 (PBC00) [8] , the Scarani, Acn, Ribordy, Gisin 2004 (SARG04) protocol [9] . These protocols belong to a family called Discrete- Variable (DV) protocols. However, there exists another family of protocols called continuous-variable protocols and Distributed-Phase-Reference (DPR) protocols [10] .
The aim of this work is to present a simple security proof for a quantum protocol based on measurements performed on a maximally entangled state. In particular, we demonstrate how the laws of quantum mechanics afford security especially which properties are important in providing security for QKD protocols. This article is organized as follows. In Section 2 we briefly describe the quantum communication procedure. In Section 3, we provide a short review of QKD security. In Section 4, we give a description of the operation principle for our proposed entanglement-based protocol, which we are going to study. In this section we also outline the security requirements for QKD. Our main result is that the success guessing probability, p for the eavesdropper to guess the state sent by Alice or received by Bob will always result in Eve gaining less than half of the information being transmitted i.e., 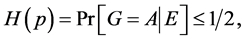 where
where 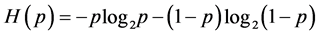 is the classical Shannon information and G is the guess for output A (Alice) when given E (Eve). This means that the eavesdropper can only learn less of the transmitted information and this forbids her from trying to reconstruct the original message shared by the legitimate parties with high accuracy. This implies that the exchanged secret key is always secure. Lastly, Section 5 is the conclusion.
is the classical Shannon information and G is the guess for output A (Alice) when given E (Eve). This means that the eavesdropper can only learn less of the transmitted information and this forbids her from trying to reconstruct the original message shared by the legitimate parties with high accuracy. This implies that the exchanged secret key is always secure. Lastly, Section 5 is the conclusion.
2. Quantum Communication Procedure
Alice and Bob first use the quantum channel to distribute quantum states and then apply a quantum key distillation scheme to generate a common string of secret correlated data which are later transformed into a secret key. The eavesdropper can freely interact with the transmitted states while the two parties communicate and try to extract information. However, Eve can only perform the most general attack allowed by the laws of quantum mechanics. The quantum channel is used to transmit quantum signals while the classical channel is used to transmit classical information. The classical channel is authenticated so that Eve cannot learn the information that is being transmitted.
In a real world, at the end of the protocol, Alice outputs the key SA while Bob outputs the key SB. The output keys must be identical, but because of the presence of an eavesdropper and errors in the channel, the keys are almost identical. However, in the ideal world, Eve’s access of the key is detected and also there are no errors in the communication channel, therefore Alice and Bob generate a perfect secret key S which is of length l. This is shown in Figure 1. This perfect secret key is then used for sending private messages by means of the one-time pad.
3. Review of QKD Security
In the last two decades, a lot of progress has been realized in the study of QKD security. Today, the unconditional security i.e., security guaranteed in an information-theoretical sense has been established for many protocols. The first unconditional security proof of QKD was proposed by Mayers in 1996 [11] . Since then, various techniques for proving the security of QKD protocols have been developed [10] . The security proofs generally depend on the construction of the protocol and also on its practical implementation. For example, the unconditional security proofs for the BB84 based protocols have long since been realized [12] . This is mainly because they share a common property of being symmetrical. On the side, the security proofs for the class of DPR protocols still remain unrealized [10] [13] , mainly because their construction and encoding deviates from the usual symmetry that exist in BB84-type based protocols. Moreover, the previous security proofs could provide bounds only in the asymptotic limit of infinitely long keys, which is not realistic. But recently, the tools for studying QKD security in the finite-size limit have now become available [14] . This has been followed by various studies on security in the finite-size limit [14] - [21] . In these papers, it was shown that the bits which are processed in QKD are indeed of finite length.
However, one of the greatest challenges that still remain in QKD implementations is a mismatch between the theoretical security proofs to real devices. This is because
Figure 1. Comparison between what happens in a real and ideal quantum cryptographic world. Alice and Bob use the quantum and classical authenticated channel in the presence of Eve. At the end of communication; in the real world, Alice and Bob share two correlated secret keys SA and SB, respectively. In an ideal world, the access of Eve is broken; therefore Alice and Bob share a perfect secret key S.
several assumptions are usually made when proving the security of QKD protocols. These assumptions are; devices do what they are supposed to do (according to a specified model) and not more, there should be access to perfect or almost perfect randomness (locally), there should be no side-channels and quantum theory is correct.
In order for a QKD protocol to be secure, it has to satisfy a number of security requirements. These requirements are [22] ;
a) correctness―a QKD protocol is called εcor-correct if, for any strategy by the eavesdropper , where SA and SB are Alice’s and Bob’s output classical keys, respectively.
, where SA and SB are Alice’s and Bob’s output classical keys, respectively.
b) secrecy―if , then S is uniform
, then S is uniform  and independent of Eve.
and independent of Eve.
c) Robustness―a QKD protocol is said to be “robust” if it’s guaranteed that it does not abort as long as the eavesdropper is inactive. When an eavesdropper is inactive, the protocol would continue to generate a secret key, otherwise if an adversary tampers with the quantum channel, the protocol recognises the attack and aborts the computation of the key.
d) Finally, a QKD is secure if it is correct and secret, that a protocol is ε-secure, if it is εcor-correct and εsec with .
.
4. Operation of Our Proposed QKD Protocol
A source prepares and distributes a maximally entangled quantum state where one system is sent to Alice and another to Bob. This is shown in Figure 2. Alice and Bob then perform measurements in two mutually unbiased bases on their system respectively. In the absence of an eavesdropper, if they measure in the same basis they obtain perfectly correlated outcomes, which are completely random. The three parties will then share a quantum state . An example of this protocol is the E91 protocol [4] .
. An example of this protocol is the E91 protocol [4] .
If the authorized parties notice some errors in Bob’s measurements, this implies that Eve has measured some of the photon polarizations. Therefore, QKD is secure because either of the following happens; if the error rate observed by Alice and Bob is lower
Figure 2. The operation principle of the proposed QKD protocol. An entanglement source produces a pair of entangled signals, which are randomly measured in certain bases chosen by Alice and Bob separately. Alice and Bob generate outcomes A and B respectively.
than a critical value usually referred to as quantum-bit-error rate (QBER), in which case a secret key can be extracted by using techniques of classical information theory. However, if the error rate is larger than QBER, Alice and Bob throw their data away and never use them to encode any message. Therefore, the eavesdropper is prevented from learning any messages being communicated from Alice to Bob.
Our proposed protocol is executed by the following steps:
a) Alice chooses to measure photons in a certain basis and also the measurement direction of the polarisation e.g., Alice chooses  and Bob chooses
and Bob chooses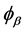 .
.
b) Repeat this experiment many times and check whether the statistics are compati-
ble with the law of physics , where the angle
, where the angle 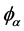 and
and 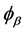 denotes
denotes
the measurement direction of the polarisation [23] .
c) If the statistics are compatible, then they may choose a particular basis 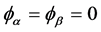 and take
and take  and
and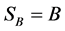 , if not then
, if not then 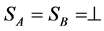 i.e., they abort the protocol.
i.e., they abort the protocol.
Theorem: Let G: guess for output A or B (on input



Proof: In the protocol, Alice and Bob test the presence of an eavesdropper by publicly comparing polarizations of a random subset of the photons on which they think they should agree. The probability that a photon sent by Alice is detected by Bob is


Table 1, if 









As mentioned above, let α, β and є be the classical random variables obtained by Alice, Bob and Eve, respectively, when they perform measurements on their quantum
Table 1. Example of transmission of qubits between Alice and Bob showing some various possibilities and the result of the inferred bits. The probability that the eavesdropper makes a correct guess on the output held by Alice and Bob is written as 


systems. The joint probability of the distribution for all the parties is expressed as


or

where 

For such a source, the preparation quality [18] is given by

where 




where 



Therefore, one can deduce that the secret key rate is obtained when


which gives us the sufficient condition

on the error rate p. Because a key can only be extracted if

5. Conclusion
We have demonstrated the principle of operation of QKD. We have shown how one can use the properties of the laws of quantum mechanics to allow the legitimate parties to share a secret key. In particular, we have shown that the eavesdropper cannot guess the output or outcome from the legitimate parties and gain more than half of the information being transmitted. This means that the key generated by quantum cryptography is always secure, thus showing the power of quantum mechanics in securing information.
Acknowledgements
This work is based on research supported by the Research Initiation Grant of the Botswana International University of Science and Technology.
Cite this paper
Mafu, M. (2016) A Simple Security Proof for Entanglement- Based Quantum Key Distribution. Journal of Quantum Information Science, 6, 296- 303. http://dx.doi.org/10.4236/jqis.2016.64018
References
- 1. Gisin, N., Ribordy, G., Tittel, W. and Zbinden, H. (2002) Quantum Cryptography. Reviews of Modern Physics, 74, 1-45.
https://doi.org/10.1103/RevModPhys.74.145 - 2. Weisner, S. (1983) Conjugate Coding. ACM SIGACT News, 15, 78-88.
https://doi.org/10.1145/1008908.1008920 - 3. Bennett, C.H. (1984) Quantum Cryptography: Public Key Distribution and Coin Tossing. Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, 175, 7-11.
- 4. Ekert, A. (1991) Quantum Cryptography Based on Bell’s Theorem. Physical Review Letters, 67, 661-663.
https://doi.org/10.1103/PhysRevLett.67.661 - 5. Bell, J. (1964) On the Einstein-Podolsky-Rosen Paradox. Physics, 1, 195-200.
- 6. Bennett, C.H. (1992) Quantum Cryptography Using Any Two Nonorthogonal States. Physical Review Letters, 68, 3121-3124.
https://doi.org/10.1103/PhysRevLett.68.3121 - 7. Bruß, D. (1998) Optimal Eavesdropping in Quantum Cryptography with Six States. Physical Review Letters, 81, 3018-3021.
https://doi.org/10.1103/PhysRevLett.81.3018 - 8. Phoenix, S.J., Barnett, S.M. and Chefles, A. (2000) Three-State Quantum Cryptography. Journal of Modern Optics, 47, 507-516.
https://doi.org/10.1080/09500340008244056 - 9. Scarani, V., Acn, A., Ribordy, G. and Gisin, N. (2004) Quantum Cryptography Protocols Robust against Photon Number Splitting Attacks for Weak Laser Pulse Implementations. Physical Review Letters, 92, Article ID: 057901.
https://doi.org/10.1103/PhysRevLett.92.057901 - 10. Scarani, V., Bechmann-Pasquinucci, H., Cerf, N., Dusek, M., Lütkenhaus, N. and Peev, M. (2009) The Security of Practical Quantum Key Distribution. Reviews of Modern Physics, 81, 1301-1350.
https://doi.org/10.1103/RevModPhys.81.1301 - 11. Mayers, D. (1996) Unconditional Security in Quantum Cryptography. Journal of the ACM, 48, 351-406.
https://doi.org/10.1145/382780.382781 - 12. Shor, P. and Preskill, J. (2000) Simple Proof of Security of the BB84 Quantum Key Distribution Protocol. Physical Review Letters, 85, 441-444.
https://doi.org/10.1103/PhysRevLett.85.441 - 13. Mafu, M., Marais, A. and Petruccione, F. (2014) A Necessary Condition for the Security of Coherent-One-Way Quantum Key Distribution Protocol. Applied Mathematics & Information Sciences, 8, 2769-2773.
https://doi.org/10.12785/amis/080612 - 14. Scarani, V. and Renner, R. (2008) Quantum Cryptography with Finite Resources: Unconditional Security Bound for Discrete-Variable Protocols with One-Way Postprocessing. Physical Review Letters, 100, Article ID: 200501.
https://doi.org/10.1103/PhysRevLett.100.200501 - 15. Cai, R. and Scarani, V. (2009) Finite-Key Analysis for Practical Implementations of Quantum Key Distribution. New Journal of Physics, 11, Article ID: 045024.
https://doi.org/10.1088/1367-2630/11/4/045024 - 16. Sheridan, L., Le, T.P. and Scarani, V. (2010) Finite-Key Security against Coherent Attacks in Quantum Key Distribution. New Journal of Physics, 12, Article ID: 123019.
https://doi.org/10.1088/1367-2630/12/12/123019 - 17. Abruzzo, S., Kampermann, H., Mertz, M. and Bruß, D. (2011) Quantum Key Distribution with Finite Resources: Secret Key Rates via Rényi Entropies. Physical Review A, 84, Article ID: 032321.
https://doi.org/10.1103/PhysRevA.84.032321 - 18. Tomamichel, M., Lim, C.C.W., Gisin, N. and Renner, R. (2012) Tight Finite-Key Analysis for Quantum Cryptography. Nature Communications, 3, Article Number: 634.
https://doi.org/10.1038/ncomms1631 - 19. Mafu, M., Garapo, K. and Petruccione, F. (2013) Finite-Size Key in the Bennett 1992 Quantum-Key-Distribution Protocol for Rényi Entropies. Physical Review A, 88, Article ID: 062306.
https://doi.org/10.1103/PhysRevA.88.062306 - 20. Mafu, M., Garapo, K. and Petruccione, F. (2014) Finite-Key-Size Security of the Phoenix-Barnett-Chefles 2000 Quantum-Key-Distribution Protocol. Physical Review A, 90, Article ID: 032308.
https://doi.org/10.1103/PhysRevA.90.032308 - 21. Zhou, C., Bao, W.S., Zhang, H.I., Li, H.W., Wang, Y., Li, Y. and Wang, X. (2015) Biased Decoy-State Measurement-Device-Independent Quantum Key Distribution with Finite Resources. Physical Review A, 91, Article ID: 022313.
https://doi.org/10.1103/PhysRevA.91.022313 - 22. Renner, R. (2008) Security of Quantum Key Distribution. International Journal of Quantum Information, 6, 1-127.
https://doi.org/10.1142/S0219749908003256 - 23. Hughes, R.J., Buttler, W.T., Kwiat, P.G., Luther, G.G., Morgan, G.L., Nordholt, J.E., Peterson, C.G. and Simmons, C.M. (1997) AeroSense’97. International Society for Optics and Photonics, 2-11.
- 24. Bennett, C., Bessette, F., Brassard, G., Salvail, L. and Smolin, J. (1992) Experimental Quantum Cryptography. Journal of Cryptology 5, 3-28.
https://doi.org/10.1007/BF00191318




