Paper Menu >>
Journal Menu >>
 J. Serv. Sci. & Management. 2008, 1: 1-9 Published Online June 2008 in SciRes (www.SRPublishing.org/journal/jssm) Copyright © 2008 SciRes JSSM BBA Decision Model for Information Systems Outsourcing: Using a Multicriteria Method Jian-Jun WangP 1 P, Zheng-Kui LinP 2 P and Hao HuangP 3 P 1 PSchool of Ma n agement, Dalian Univ ersity of Te chnology, Dalian 116024, P.R .China P 2 PSchool of Computer Science & Technology, Dalian Maritime University, Dalian 116026, P.R.China P 3 PSchool of Economic a n d Management, Beihang University, Beijing 100083, P.R.China ABSTRACT An ever-increasing trend in today’s firms is to exploit outsourcing for those information systems (IS) functions deemed to be outside the company’s core competence. Given the multi-attribute nature of IS outsourcing decision, this paper argues that five facto rs, including, strategy, economics, risk, environment an d quality, should be con sidered for IS out- sourcing decisions, and proposes the use of analytic hierarchy process (AHP) and improved ELECTREIII as aids in making IS outsourcing decisions. The AHP is used to analyze the structure of the outsourcing problem and determine weights of the criteria, and the improved ELECTREIII method is used for final ranking. It shows by means of an appli- cation that the hybrid method is very well suited as a decision-making tool fo r the IS outsourcing decision. Finally, po- tential issues for future research are presented. Keywords: Information systems outsourcing, Multiple criteria analysis, AHP, ELECTREIII 1. Introduction Information systems (IS) outsourcing can be defined as “a significant contribution by external vendors in the physi- cal and/or human resources associated with the entire or specific components of the IS infrastructure in the user organization”[1]. IS outsourcing is a growing phenome- non in a wide variety of industries. According to the Gartner Group, overall spending in information technol- ogy (IT) outsourcing reached$177 billion in 2003, and it is predicted to rise to$236 billion in 2007(Oh, 2005). Yet in many cases, outsourced IS projects have failed. For example, in one study, IS managers reported only a 33% satisfaction with outsourced IS services, as compared with a satisfaction rate of 70%-80% for outsourced non-IS services [2 ]. Wrong IS outsourcing decision is one of critical reasons which cause the high IS outsourcing failure [3]. Therefore, the scientific IS outsourcing deci- sion process is very important to increase the success rate of outsourcing. The problem of how to scientifically make the IS outsourcing decisions tends to be an impor- tant issue facing organizations in today’s rapidly chang- ing business environment [4]. Business practitioners recognize that IS outsourcing is one of the m any t ools in thei r toolki t to desi gn and m anage their business and potentially has a place in most strategic plans. Although there is a wealth of academic literature examining outsourcing, it generally addresses the decision whether or not to outsource: the go/no go choice. There is little academic literature that address the IS outsourcing decision in a quantitative way. This paper will apply a hybrid of analytic hierarchy process (AHP) and improved ELECTRE III methods to the “IS outs o urcing decision” in an effort to demonstrate one quantitative approach to this complex decision. The remainder of this paper is organized into five sec- tions. Section 2 presents a brief literature review of the existing decision models related to the IS outsourcing decision. Section 3 will briefly describe the two proposed methodologies. In section 4 we argue five factors pro- posed as the p rincipal criteria for outsourcing decision . In Section 5 a description of proposed methodology is fol- lowed by an application. In Section 6, we present our conclusions a nd future rese arch. 2. Literature Review A number of decision frameworks appear in academic literature to support the outsourcing decision-making process. Lacity, Willcocks and Feeny (1996) argued that deciding the outsourcing of IT activities just by strategic or commodities was fallacious and senior executives might mistakenly classify all IS activities as commodities. Therefore, they presented a 2x2 decision matrix guiding the selection of outsourcing candidates based on the business, economic, and technical factors[5]. Venkatraman (1997) viewed information technology as a portfolio of IS elements that were cost centers, service centers, investment centers and profit centers (which are collectively referred to as an IS “value centers”). His focus on “four i ndep endent source s of val ue from IS resource ” is useful for i dentifyi ng IS elem ents that might be conside red for outsourci n g [6] .  2 Jian-Jun Wang, Zheng-Kui Lin and Hao Huang Copyright © 2008 SciRes JSSM Yang and Huang (2000) argued that five factors, in- cluding m anagem en t, strat egy, econom ics, technolo gy a nd quality, should be considered for outsourcing decision, then they used the analytic hierarchy process (AHP) method to help users in structuring the outsourcing prob- lems[7]. Roy and Aubert (2002) presented an IT outsourcing decision model based on the resource theory[8]. Hsu et al (2004) analyzed the IS outsourcing decision problems by case-based reasoning (CBR) method[9]. Aubert et al [2004] proposed an IT outsourcing decision model relied on transaction costs and incomplete contracts theo- ries[10]. According to the above-mentioned literature, research- ers put so many outsourcing decision strategies and de- terminants to practitioners, but current practice remains in the stage of conceptual discussion as to how to outsource the IS activities. Furthermore, only the AHP method offers a quantitative magnitude for judgment among these strategies and determinants. But AHP approach has the disadvantage that the number of pairwise comparisons to be made, may become very large (more specifically: n(n-1)/2). Another critical disadvantage of the AHP method is that compensation betwee n good scores on som e criteria and bad scores on other criteria can occur. Other strategies or determinants, for instance, decision matrix, transaction cost or CBR method, are too narrow to help the practitioners determine if their systems could be out- sourced or to examine the priorities among ma ny pote ntial IS outsourcing projects. Ineffectiv e outsourcing activities, derived from improper strategy or method, would lead to loss core competencies and capabilities, exposure to un- expected risk and business failures. Facing the problem of how to decide the priority of those IS which have been decided to outsource, we pro- pose a hybrid multi-criteria decision method for the IS outsourcing decision making. We shall use the AHP method to anal yze the structure of the outso urcing problem and determine the weights of criteria, and use the improved ELECTRE III method for final ranking. The purpose of this work is to offer a quantitative d ecision mod el that can help practitioners set priority and reap the most benefits from outsourcing. 3. The AHP and Electre III Method 3.1. The AHP Method The AHP, developed by Saaty (1980)[11], is a technique for considering data or information about a decision in a systematic manner [12]. The AHP mainly addresses how to solve decision problems with uncertainty and with multiple criteria characteristics. It is based on three prin- ciples: first, constructing the hierarchy; second, priority setting, and third, logical con sistency. 3.1.1. Construction the hierarchy A complex decision problem, centered round measuring contributions to an over objective or focus, is structured and decomposed in to sub-problems (sub-objectives, crite- ria, alternatives, etc), within hierarchy. 3.1.2. Priori ty setting The relative “priority” given to each element in the hier- archy is determined by comparing pairwise the contribu- tion of each element at a lower level in terms of the crite- ria (or elements) with a causal relationship exists. In AHP multiple paired comparisons are based on a standardized comparison scale of nine levels (see Table 1, Saaty 1980). Table 1. Scale of Relative Importance Intensity of impor- tance Definition 1 Equal importance 2 Weak 3 Moderate importance 4 Moderate plus 5 Strong importance 6 Strong plus 7 Very strong or demon- strated importance 8 Very, very strong 9 Extreme importance Let 1, 2,,{} j j nCC==Lbe the set of criteria. The re- sult of the pairwise comparison on n criteria can be sum- marized in a ()nn × evaluation matrix A in which every element ij ais the quotient of weights of the criteria, as shown in (1). (),(, 1,,) ij A aijn = =L (1) The relative priorities are given by the right eigenvec- tor (w) corresponding to the largest eigenvector (max λ ), as shown in (2). max Aw w λ = (2) In case the pairwise comparisons are completely con- sistent, the matrix A has rank 1 andmax n λ =. In that case, weights can be obtained by normalizing any of the rows or columns of matrix A . The procedure described above is repeated for all sub- systems in the hierarchy. In order to synthesize the vari- ous priority vectors, these vectors are weighted with the global priority of the parent criteria and synthesized. This process starts at the top of the hierarchy. As a result, the overall relative priority to be given to the lowest level elements is obtained. These overall, relative priorities indicate the degree to which the alternatives contribute to the focus. These priorities represent a synthesis of the local priorities, and reflect an evaluation process that permits to integrate the perspectives of the various stake- holders involved [13].  A Decision Model for Information Systems Outsourcing: Using a Multicriteria Method 3 Copyright © 2008 SciRes JSSM 3.1.3. Consi s tency check A measure of consistency of the given pairwise compari- son is needed. The consistency is defined by the relation between the entries of A:ij jkik aa a ⋅ =. The “consis- tency index” (CI) is given by (3). max CI() / (1)nn λ =− − (3) The final consistency ratio (CR), on the basis of which one can conclude whether the evaluations are sufficiently consistent, is calculated as the ratio of the consistency index (CI) and the random consistency index (RI), as in- dicated in (4). The number 0.1 is the accepted upper limit for CR. If the final consistency ratio exceeds the number, the evaluation procedure has to be repeated to improve consistency. The measurement of consistency can be used to evaluate the consistency of decision makers as well as the consistency of all the hierarchy. CR=CI/RI (4) 3.2. The ELECTRE III Method 3.2.1. The normal ELECTRE III method ELECTREIII method is a non-compensatory, MCDM technique. It uses various mathematical functions to indi- cate the degree of dominance of one alternative or group of alternatives over the remaining ones. It also facilitates comparisons between alternative schemes by assigning weights to decision criteria. The outranking relationships between alternatives are constructed and exploited even- tually. A discrete multiple criteria decision making problem is usually formulated by a set of alternatives { } 12 ,,, n X xx x=L, a set of criteria { } 12 ,,, m Ccc c=Land a set of func- tions { } 12 ,,, m Ggg g=L. The real-valued functions de- fined on the setXso that() lj g xrepresents the perform- ance of the alternativej x on the criterionl c. Without loss of generality we assume that all the objective functions are to be maximized. A pseudo-criterion is a preference model including three different thresholds: a preference threshold (()) llj pgx , an indifference threshold (()) llj qgx and a veto threshold(( )) llj vgx for each criterion { } 12 ,,, m Ccc c=L. These thresholds may be constants, lin- ear or affine functions of() lj g x in the form [14]. ,, (()) () lljpl pllj pgx gx α β =+ and ,, (()) () lljql qllj qgx gx α β =+ For every criterionl c, the preference and indifference threshold model is as follows. i x is preferred toj x if ()()(()) lil jl l j g xgxpgx + f i x is weakly preferred toj x if () (())()()(()) lj lljliljllj g x qgxgx gxpgx + ≤+p, and i x is indifferent toj x if () (())() lj lljli g xqgx gx + ≥ and () (())() lil lil j g x qgxgx + ≥ Where (( )) llj pgx and (()) llj qgx are preference and indifference thresholds, respectively and (()) (())0 llj llj pgx qgxff . Weak preference is sup posed to describe the decision maker’s hesitation between indif- ference and preference. In ELECTRE III method, one considers an outranking degree (,) ij Sx xdescribing the outranking credibility of i x over j x taking its values between 0 and 1. The value of (,) ij Sx xis defined based on so-called concordance and discordance indices. A concordance index (, ) ij Cx xis computed for each pair of alterna- tives(, ) ij x xby 1 1 (, )(, ) m ij llij l Cx xwc x x w= =∑ (5) Where (1,,) l wl m = Lis the weight of each criterion, and 1 m l l ww = = ∑ (6) () ( )()() ( ) () ()() () ()()() () ()() ()() ⎪ ⎪ ⎩ ⎪ ⎪ ⎨ ⎧ − −+ ≤+ ≥+ = otherwis e 0 1 , illill jlilill jlillil jlillil jil xgqxgp xgxgxgp xgxgpxg xgxgqxg xxc (7) A discordance index(, ) lij dxxis defined for each crite- rion l cby () ( )()() () () ()() () () () ()() ()() ()() ⎪ ⎪ ⎩ ⎪ ⎪ ⎨ ⎧ − −− ≥+ ≤+ = otherwise 0 1 , illill illiljl jlillil jlillil jil xgpxgv xgpxgxg xgxgpxg xgxgvxg xxd (8) where(()) lli pgx is the preference threshold value and (()) lli vgx is the veto threshold value of each l c and (()) (()) llilli vgx pgxf.  4 Jian-Jun Wang, Zheng-Kui Lin and Hao Huang Copyright © 2008 SciRes JSSM Finally, the degree of outranking is defined by () ( ) ( ) ( ) () () ()() () ⎪ ⎩ ⎪ ⎨ ⎧ − − • ∀≤ =∏ ∈jixxJl ji ji jil ji jijilji ji xxJ xxC xxd xxC lxxCxxdxxC xxS , , ,1 ,1 , ,,, , (9) where (, ) ij J xx is the set of criteria for which (, )(, ) li ji j dxx Cxxf. The complete set of outranking degree is assembled as shown in the following credibility matrix S . 11 121 21 222 12 (,)(, )(, ) (,) (,)(,) (,) (,)(,) n n nn nn Sx xSx xSx x Sx xSx xSx x Sx xSx xSx x ⎡⎤ ⎢⎥ ⎢⎥ =⎢⎥ ⎢⎥ ⎣⎦ L L MMMM L S (10) The ranking of the decision alternatives in ELECTRE III is carried out by a distillation procedure, where the alternatives are ranked based on their qualification from the best to the worst (descending distillation process) and from the worst to the best (ascending distillation proc- ess).The final partial order of the alternatives is built based on these two complete orders. The descending dis- tillation process is as follows. Let , max( ,) ij ij xx X Sx x λ ∈ =. Determine a “credibility value” such that only values of (, ) ij Sx xthat are suffi- ciently close to λ are considered; that is, () s λ λ −. Thus if 1 λ =, let()0.15s λ =. Define the matrixTas: 1if (,)() (, )0otherwise ij ij Sx xs xx λ λ − ⎧ ⎪ =⎨ ⎪ ⎩ f T (11) Further, define the qualification of each alternative −− )(i xQ as the number of alternatives that are out- ranked byi x minus the number of alternatives which out- rank i x .() i Qx is simply the row minus the column sum of the matrixT. The set of alternatives having the largest qualification is the first distillate of1 D . If 1 D contains only one alternative, repeat the previous procedure with 1 \XD .Otherwise, apply the same procedure in- side 1 D . If distillate2 D contains only one alternative, the procedure is started in12 \ D D(unless the set is empty); otherwise it is applied within2 D , and so on until 1 D is used up. The procedure is then repeated starting with 1 \XD . The outcome is the first preorder. The ascending distillation is carried out in a similar fashion except that alternatives with the smallest (rather than the largest) qualification are retained first. 3.2.2. An improved ranking method for ELECTRE III The normal ranking of ELECTRE III requires an addi- tional threshold to be introduced. The weakness of this handing is that the ranking of the alternatives depends on the size of this threshold for which there exists no “cor- rect” value. Additionally, the final ranking is not com- plete. Aiming at the ranking problems in ELECTRE III, we present a new ranking method by introducing three defi- nitions — concordance credibility degree, discordance credibility degree and net credibility degree, into ELEC- TRE III method. Definitions The concordance credibility degree is defined by ()(, ), j iiji xX x Sx xxX Φ + ∈ = ∀∈ ∑ (12) The concordance credibility degree is the measure of the outranking character ofi x (how i x dominates all the other alternatives of X ) The discordance credibility degree is defined by () (,), j ijii xX x Sx xxX Φ − ∈ = ∀∈ ∑ (13) The discordance credibility degree gives the outranked character of i x (how i x is dominated by all the other al- ternatives ofX) The net credibility degree is defined by ()() (), iiii x xxxX ΦΦ Φ +− = −∀∈ (14) The net credibility degree represents a value function, where a higher value reflects a higher attractiveness of alternative i x . Final ranking All the alternatives can be completely ranked by the net credibility degree. An application This application is based on a real-life case study where the ELECTRE III method was use to help choose route for Dublin port motorway [15]. The first credibility matrix in [15] is as follows: 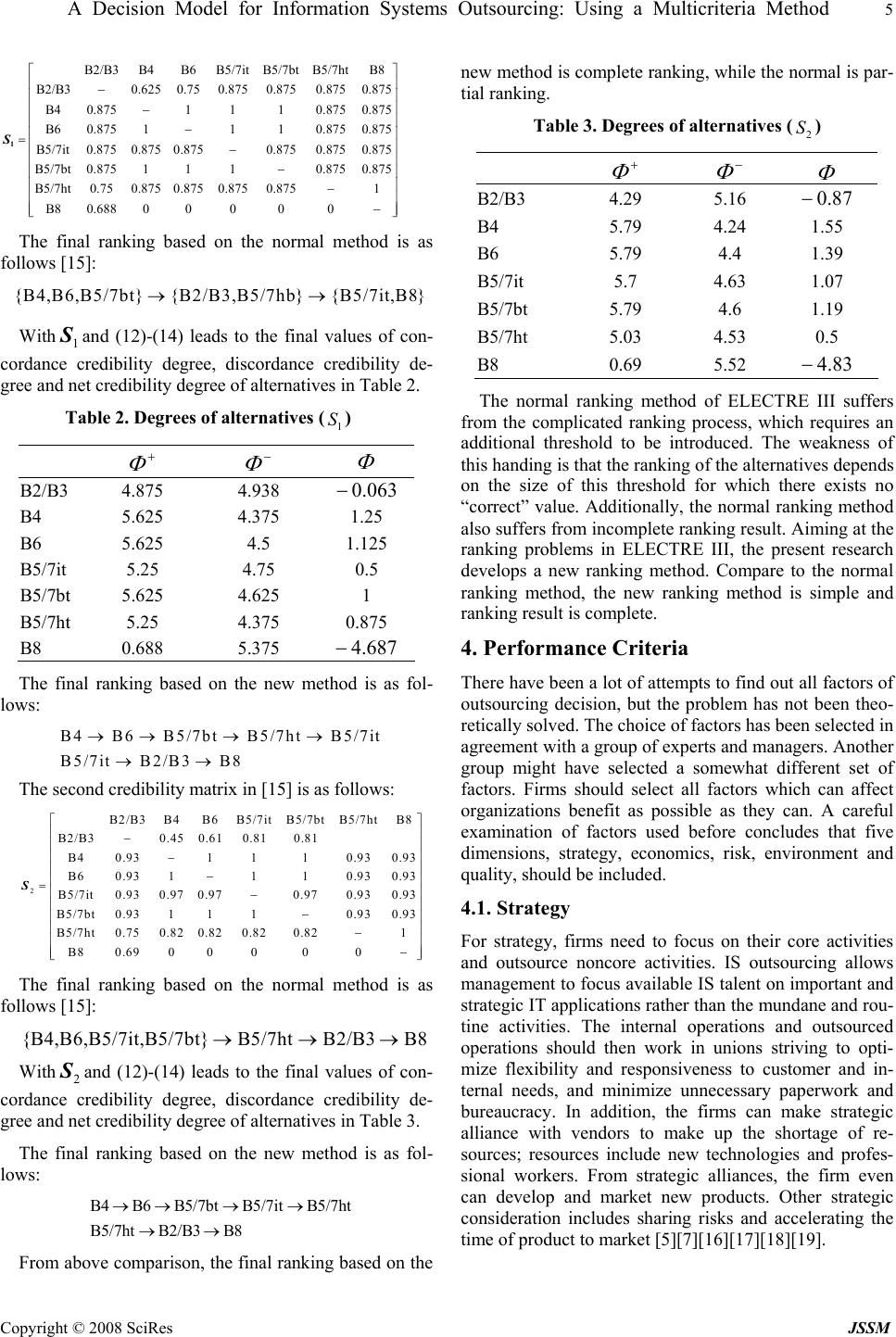 A Decision Model for Information Systems Outsourcing: Using a Multicriteria Method 5 Copyright © 2008 SciRes JSSM B2/B3B4B6B5/7itB5/7btB5/7htB8 B2/B30.625 0.750.8750.8750.875 0.875 B40.8751110.875 0.875 B60.8751110.875 0.875 B5/7it0.8750.875 0.8750.8750.8750.875 B5/7bt 0.8751110.875 0.875 B5/7ht0.750.875 0.8750.8750.87 − − − =− − 1 S 51 B80.688 00000 ⎡⎤ ⎢⎥ ⎢⎥ ⎢⎥ ⎢⎥ ⎢⎥ ⎢⎥ ⎢⎥ ⎢⎥ ⎢⎥ − ⎢⎥ − ⎢⎥ ⎣⎦ The final ranking based on the normal method is as follows [15]: {B4,B6,B5/7bt} {B2/B3,B5/7hb} {B5/7it,B8}→→ With 1 S and (12)-(14) leads to the final values of con- cordance credibility degree, discordance credibility de- gree and net credibility degree of alternatives in Table 2. Table 2. Degrees of alternatives (1 S) Φ + Φ − Φ B2/B3 4.875 4.938 063.0− B4 5.625 4.375 1.25 B6 5.625 4.5 1.125 B5/7it 5.25 4.75 0.5 B5/7bt 5.625 4.625 1 B5/7ht 5.25 4.375 0.875 B8 0.688 5.375 687.4− The final ranking based on the new method is as fol- lows: B4 B6B5/7bt B5/7htB5/7it B5/7itB2/B3 B8 →→ → → →→ The second credibility matrix in [15] is as follows: 2 B2/B3B4B6B5/7it B5/7bt B5/7htB8 B2/B30.45 0.610.810.81 B40.931110.93 0.93 B60.931110.93 0.93 B5/7it0.930.970.970.970.930.93 B5/7bt 0.931110.93 0.93 B5/7ht0.750.82 0.820.820.821 B80.69 00000 ⎡⎤ ⎢⎥ − ⎢⎥ ⎢− ⎢− ⎢ =⎢− ⎢− ⎢ ⎢− ⎢ − ⎢ ⎣⎦ S ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ The final ranking based on the normal method is as follows [15]: {B4,B6,B5/7it,B5/7bt} B5/7htB2/B3 B8→→→ With2 S and (12)-(14) leads to the final values of con- cordance credibility degree, discordance credibility de- gree and net credibility degree of alternatives in Table 3. The final ranking based on the new method is as fol- lows: B4B6B5/7bt B5/7it B5/7ht B5/7htB2/B3 B8 →→→ → →→ From above comparison, the final r anking based on the new method is complete ranking, while the normal is par- tial ranking. Table 3. Degrees of alternatives (2 S) Φ + Φ − Φ B2/B3 4.29 5.16 87.0− B4 5.79 4.24 1.55 B6 5.79 4.4 1.39 B5/7it 5.7 4.63 1.07 B5/7bt 5.79 4.6 1.19 B5/7ht 5.03 4.53 0.5 B8 0.69 5.52 83.4− The normal ranking method of ELECTRE III suffers from the complicated ranking process, which requires an additional threshold to be introduced. The weakness of this handing is that the ranking of the alternatives depends on the size of this threshold for which there exists no “correct” value. Additionally, the normal ranking method also suffers from incomplete ranking result. Aiming at the ranking problems in ELECTRE III, the present research develops a new ranking method. Compare to the normal ranking method, the new ranking method is simple and ranking result is complete. 4. Performance Criteria There have been a lot of attempts to find out all factors of outsourcing decision, but the problem has not been theo- retically solved. The choice of factors has be en selected in agreement with a group of experts and managers. Another group might have selected a somewhat different set of factors. Firms should select all factors which can affect organizations benefit as possible as they can. A careful examination of factors used before concludes that five dimensions, strategy, economics, risk, environment and quality, should be included. 4.1. Strategy TFor strategy, firms need to focus on their core activities and outsource noncore activities. IS outsourcing allows management to focus available IS talent on important and strategic IT applications rather than the mundane and rou- tine activities. The internal operations and outsourced operations should then work in unions striving to opti- mize flexibility and responsiveness to customer and in- ternal needs, and minimize unnecessary paperwork and bureaucracy. In addition, the firms can make strategic alliance with vendors to make up the shortage of re- sources; resources include new technologies and profes- sional workers. From strategic alliances, the firm even can develop and market new products. Other strategic consideration includes sharing risks and accelerating the time of product to market [5][7][16][17][18][ 19]T.  6 Jian-Jun Wang, Zheng-Kui Lin and Hao Huang Copyright © 2008 SciRes JSSM 4.2. Economics For economics, the major consideration of a firm is to reduce costs of information systems. Because the vendors have a better management skill as well as higher produc- tivity per employee, the costs can be reduced. Meanwhile, Because of the scale of economics vendors have invested in the hardware, software and human resources, the cost can be reduced. Another consideration of economics is financial flexibility. Because of outsourcing, the facilities and employee would be transferred to the vendor side, which transform fixed costs into variable costs, resulting in increasing financial flexibility [7][9][20][21]. 4.3. Risk For risk, it is rare to experience opportunities in organiza- tional life where the managerial actions taken to produce benefits are not associated with potential risks either. This is most certainly the case with IS outsourcing. The most prominent risks in outsourcing are information security concerns an d loss of management co ntrol. Khalfan [2004] noted theses two factors were coupled with hidden costs in outsourcing [22]. If a labor union exists, a firm should first explore its negative effect before deciding to outsource, since out- sourcing is accompanied with some possibility of layoffs. Companies often have to deal with low employee morale as a result of outsourcing, and low employee morale in turn affects productivity. It has been noted that often a large proportion of IT staff are laid off as a consequence of an outsourcing contract. This can cause a lot of distur- bance in the client company. Other risks that have to be dealt with include: loss of core competence, loss of internal technical knowledge, loss of flexibility, damaging the firm’s innovative capa- bility, increasing information services management com- plexity, etc [23][24]. As being the factors with benefits, these risks factors should not be ignored in outsourcing activities [25] [26]. 4.4. Environment Quinn and Hilmer [1994] indicated that environment fac- tors such as market maturity, market depth, and the num- ber of suppliers influences the level of outsourcing [16]. There are times when contestability explains market ma- turity; a contestable market means that while only a few firms can immediately provide the service now, many other firms are intending to provide the service if the price paid by the firm exceeds the average cost of vendors. In addition, the decision to outsource may be induced by imitative behavior among firms [27]. For example, Ko- dak’s outsourcing decision made many other firms begin to consider IS outs o urci n g as a viable alternative [28]. 4.5. Quality TFor quality, because vendors may have access to more technological environments, have more qualified or more motivated personnel, provide a greater breadth of services, and simply be more committed than internal staff to mak- ing the alliance with the customer work well, outsourcing can improve the quality and services of the internal IS department. Therefore, good quality of service and good relationship are the significant success factors of out- sourcing [7] [25[29]. 5. An Application Based on IS outsourcing decision problem presented in Section 1, an example is used to illustrate how the com- bined AHP and improved ELECTREIII model support decision maker on the IS outsourcing decision making. 5.1. The Problem Faced A bookstore wants to outsource parts of IT functions, they think about the management and cost issues and want to know how to decide which systems should be outsourced first. The candidate systems for outsourcing are facilities management (P1), development of internet homepage (P2), maintenance of the customer relationship manage- ment information system (P3), development of the sup- plier relationship management information system (P4), development and maintenance of the online transaction processing system (P5). The leader of the task force is the vice president, while members include IS department manager, a senior engi- neer, business department manager, finance department manager, planning department manager and five profes- sional consultants. The vice president convened a meeting to discuss this problem. After some discussion, they em- ploy the hybrid of AHP and ELECTRE III methods in the decision process. 5.2. Structure of the Problem After some debate, according to the AHP method, the Figure 1. The Hierarchy Structure of the Problem … Outsourcing candidate 1Outsourcing candidate 2 Outsourcing candidate 5 Select the outsourcing system Qual- it y Strategy Environment Economics Risk 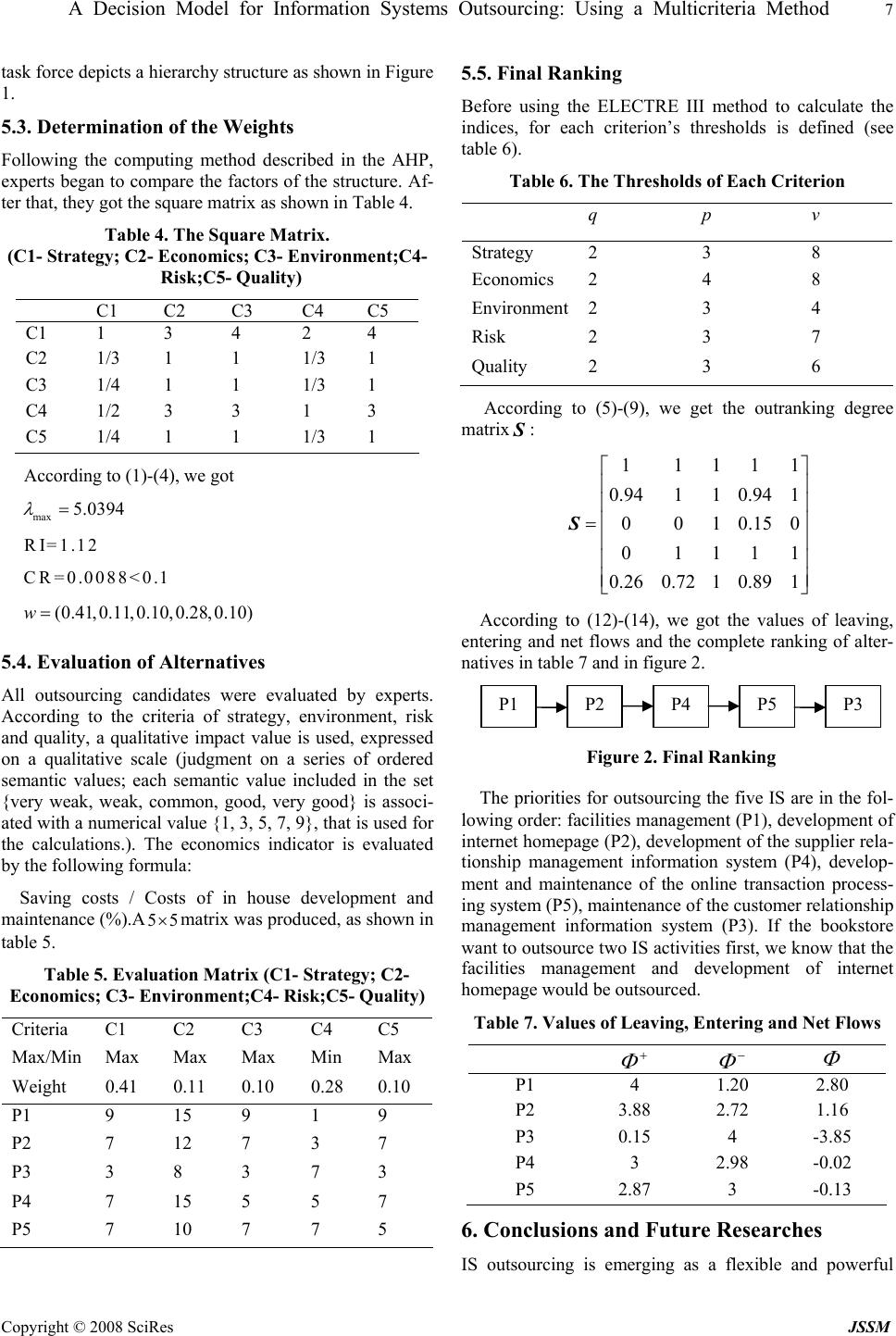 A Decision Model for Information Systems Outsourcing: Using a Multicriteria Method 7 Copyright © 2008 SciRes JSSM task force depicts a hierarchy structure as shown in Figure 1. 5.3. Determination of the Weights Following the computing method described in the AHP, experts began to compare the factors of the structure. Af- ter that, they got the square matrix as shown in Table 4. Table 4. The Square Matrix. (C1- Strategy; C2- Economics; C3- Environment;C4- Risk;C5- Qu a lity) C1 C2 C3 C4 C5 C1 1 3 4 2 4 C2 1/3 1 1 1/3 1 C3 1/4 1 1 1/3 1 C4 1/2 3 3 1 3 C5 1/4 1 1 1/3 1 According to (1)-(4), we got max 5.0394 λ = RI=1.12 CR=0.0088<0.1 (0.41,0.11,0.10,0.28,0.10)w= 5.4. Evaluation of Alternatives All outsourcing candidates were evaluated by experts. According to the criteria of strategy, environment, risk and quality, a qualitative impact value is used, expressed on a qualitative scale (judgment on a series of ordered semantic values; each semantic value included in the set {very weak, weak, common, good, very good} is associ- ated with a numerical value {1, 3, 5, 7, 9}, that is used for the calculations.). The economics indicator is evaluated by the following formula: Saving costs / Costs of in house development and maintenance (%).A55×matrix was produced, as shown in table 5. Table 5. Evaluation Matrix (C1- Strategy; C2- Economics; C 3- Environment;C 4- Ri sk ;C 5- Quality) Criteria C1 C2 C3 C4 C5 Max/Min Max Max Max Min Max Weight 0.41 0.11 0.10 0.28 0.10 P1 9 15 9 1 9 P2 7 12 7 3 7 P3 3 8 3 7 3 P4 7 15 5 5 7 P5 7 10 7 7 5 5.5. Final Ranking Before using the ELECTRE III method to calculate the indices, for each criterion’s thresholds is defined (see table 6). Table 6. The Thresholds of Each Criterion q p v Strategy 2 3 8 Economics 2 4 8 Environment 2 3 4 Risk 2 3 7 Quality 2 3 6 According to (5)-(9), we get the outranking degree matrix S : 11111 0.9411 0.941 0010.150 01111 0.260.7210.891 ⎡ ⎤ ⎢ ⎥ ⎢ ⎥ ⎢ ⎥ = ⎢ ⎥ ⎢ ⎥ ⎢ ⎥ ⎣ ⎦ S According to (12)-(14), we got the values of leaving, entering and net flows and the complete ranking of alter- natives in table 7 and in figure 2. The priorities for outsourcing the five IS are in the fol- lowing order: facilities management (P1), development of internet homepage (P2), development of the supplier rela- tionship management information system (P4), develop- ment and maintenance of the online transaction process- ing system (P5), maintenance of the customer relationship management information system (P3). If the bookstore want to outsource two IS activities first, we know that the facilities management and development of internet homepage would be outsourced. Table 7. Values of Leaving, Entering and Net Flows Φ + Φ − Φ P1 4 1.20 2.80 P2 3.88 2.72 1.16 P3 0.15 4 -3.85 P4 3 2.98 -0.02 P5 2.87 3 -0.13 6. Conclusions and Future Researches IS outsourcing is emerging as a flexible and powerful P1 P2 P4 P5 P3 Figure 2. Final Ranking  8 Jian-Jun Wang, Zheng-Kui Lin and Hao Huang Copyright © 2008 SciRes JSSM management approach chosen by managers to achieve a wide range of tactical and strategic goals. Outsourcing firms benefit from cost savings, strategic fitness, im- proved management effectiveness, technology upgrade, and the service quality of IS. Moreover, one needs an operational decision model that can offer systematic steps and quantitative results to increase the precision of deci- sion-making. This study suggests a decision model for IS outsourc- ing adoption for management, and shows how it may be applied in a real decision process for IS outsourcing. This research also argues that firms need to consider more di- mensions, including economics, strategy, risk, environ- ment and quality factors. Meanwhile, we offer a decision model, which developed by AHP and improved ELEC- TRE III methods, to help the practitioners make better decisions. Our approach allows to deal with IS outsourc- ing project selection involving several conflicting per- formance criteria (qualitative as well quantitative). The proposed decision model can help practitioners analyze factors and attributes easily. Because it is a quantitative process, the practitioners can make better decisions and obtain better results from outsourcing. While it has successfully developed the decision model for IS outsourcing, and with most research efforts, this study is not without limitations. First, the case study just based on a small firm. Second, the AHP and ELECTRE III methods also have their own limitations; such as, in order to get more professional results, the use of more advance form of AHP method would be desirable. In ad- dition, the determinants in the decision model are not complete. Further studies need to include additional pos- sible factors through a more extensive literature review and empirically investigation. 7. Acknowledgements This work is partially supported by a grant from National Science Fund for Distinguishe d Young Scholars of Ch ina (No. 70725004). The authors also thank the anonymous referees for im- proving the quality of the paper with their precious and careful remarks. REFERENCES [1] Loh, L., & Venkatraman, N, “Determinants of in- formation technology outsourcing: a cross-sectional analysis”, Journal of Management Information Sys- tems, 1992, 9(1), 7-24. [2] King, W.R, “Developing a sourcing strategy for IS: A behavioral decision process and framework”, IEEE Transaction Engineering Management, 2001, 48(1), 15-24 [3] Wu, F., & Li, H.Z, “The effect of knowledge man- agement on the successful outsourcing of IT/IS”, Science Research M a na gement, 2004, 25(2), 82-87. [4] Lee, Jae-N, “The impact of knowledge sharing, or- ganizational capability and partnership quality on IS outsourcing success”, Information & Management, 2001, 38, 323-335. [5] Lacity, M.C., Willcocks, L.P., & Feeny, D.F, “The value of IT sourcing”, Sloan Management Review, 1996, 37(3), 13-25. [6] Venkatraman, N, “Beyond outsourcing: Manage- ment IT resources as a value center”, Sloan Man- agement Review, 1997, 38(3), 51-64. [7] Yang, C., & Huang, J, “A decision model for IS outsourcing”, International Journal of Information Management, 2000, 20(3), 225-239. [8] Roy, V., & Aubert, B, “A resources-based analysis of IT sourcing”, ACM SIGMIS Database, 2002, 33(2), 29-40. [9] Hsu, C.I., Chiu. C., & Hsu, P.L, “Predicting infor- mation systems outsourcing success using a hierar- chical design of case-based reasoning”, Expert Sys- tems with Application, 2004, 26(3), 435-441. [10] Aubert, B.A., River d, S., & Patry, M, “A transaction cost model of IT outsourcing”, Information & Man- agement, 2004, 41, 921-932. [11] Saaty, T. L, The analytic hierarchy process. New York: McGraw Hill, 1980. [12] Schniederjans M J, Garvin T. “Using the analytic hierarchy process and multi-objective programming for the selection of cost drivers in activity-based costing,” European Journal of Operational Re- search, 1997, 100: 72 - 80 . [13] Macharis C, Springael J, De Brucher K, Verbeke A. “PROMETHEE and AHP: the design of operational synergies in multicriteria analysis. Strengthening PROMETHEE with ideas of AHP,” European Journal of Operational Research, 2004, 153(2): 307-317. [14] K. Miettinen, P. Salminen, “Decision-aid for dis- crete multiple criteria decision making problems with imprecise data”, European Journal of Opera- tional Research, 1999, 119: 50-60. [15] M. Rogers, M. Bruen, “Using ELECTRE III to choose route for Dublin fort motorway”, Journal of Transportation Engineering, 2000, 126(4): 313-326. [16] Quinn, J.B., & Hilmer, F.B, „Strategic outsourcing”, Sloan Management Review 1994, 35(4), 43-55. [17] Quinn, J.B, “Strategic outsourcing”, Sloan Man- agement Review, 1999, 40(4), 23-26. [18] Gilley, K.M., & Rasheed, A, “Making more by do- ing less: Analysis of outsourcing and its effects on firm performance”, Journal of Management, 2000, 26, 763-790. [19] Avgerou, C., & Cornford, T, Developing Informa- tion Systems: Concepts, Issues and Practice (2nd edn). Basingstoke: Macmillan; 1998.  A Decision Model for Information Systems Outsourcing: Using a Multicriteria Method 9 Copyright © 2008 SciRes JSSM [20] McFarlan, F.W., & Nolan, R.L, “H ow to manage an IT outsourcing alliance”, Sloan Management Review, 1995, 36(2), 9-23. [21] Collins, J., Millen. R., & Beamish, P, “Information systems outsourcing by large American industrial firms: Choice and impact”, Information Resources Management Journal, 199 5, 8( 1) , 5-13. [22] Khalfan, A.M, “Information security considerations in IS/IT outsourcing projects: a descriptive case study of two sectors” International Journal of In- formation Management, 2004, 24, 29-42. [23] Bahli, B., Rivard, S, “Validating measures of infor- mation technology outsourcing risk factors”, Omega, 2005, 33(2): 175-187. [24] Osei-Bryson, K. Muata., Ngwenyama, O. K, “Man- aging risks in information systems outsourcing: An approach to analyzing outsourcing risks and struc- turing incentive contracts”, European Journal of Operational Research, 2006, 174(1): 245-264. [25] Clark, T., Zmud, R., & McCray, G, “The outsourc- ing of information services: transforming the nature of business in the information industry”, Journal of Information Technology, 1995, 10(4), 221-237. [26] Earl, M.J, “The risks of outsourcing IT”, Sloan Management Review, 1996, 37(3), 26-32. [27] Lacity, M.C., Herschheim,R., & Willcocks, L, “Re- alizing outsourcing expectations”, Information Sys- tems Management, 1994, 4, 7-18. [28] Smith, M., Mitra, S., & Narasimhan, S, “Information systems outsourcing: a study of pre-event firm char- acteristics”, Journal of Management Information Systems, 1998, 15, 61-93. [29] Grover, V., Joong, M., Cheon., & Teng, J.T, “The effect of service qualify and partnership on the outsourcing of information systems functions”, Journal of Management Information Systems, 1996, 12(4), 89-116. AUTHORS’ BIOGRAP HIES Jian-Jun Wang completed his Ph.D. in Information Systems from Dalian University of Technology, P.R.China. He has been Assistant Professor at Dalian University of Technology. His main research fields are IS/IT outsourcing, ser- vice management and e-commerce. He is involved in many national research projects and he has published many re- search papers in refereed academic journals such as Computers & Operations Research, Chaos, Solitons and Fractals, International Journal of Pure and Applied Mathematics, International Journal of Knowledge and Systems Sciences, etc. He served as a reviewer for a number of international refereed academic journals and refereed conferences. Email: drwangjj@dlut.edu.cn Zheng-Kui Lin completed his Ph.D. in Management Science and Engineering from Dalian University of Technol- ogy, P.R.China. He has been Associate Professor at Dalian Maritime University. His main research fields are informa- tion systems and e-commerce. He is author of more than 10 articles published on national and international refereed journals. Email: dalianjx@163.com Hao Huang is a Ph.D. candidate in School of Economic and Management at Beihang University, P.R.China. He works in the field of information management. Email: huang_hao98@yahoo.com.cn  10 Jian-Jun Wang, Zheng-Kui Lin and Hao Huang Copyright © 2008 SciRes JSSM |

