W. DUAN ET AL.
Copyright © 2013 SciRes. CN
24
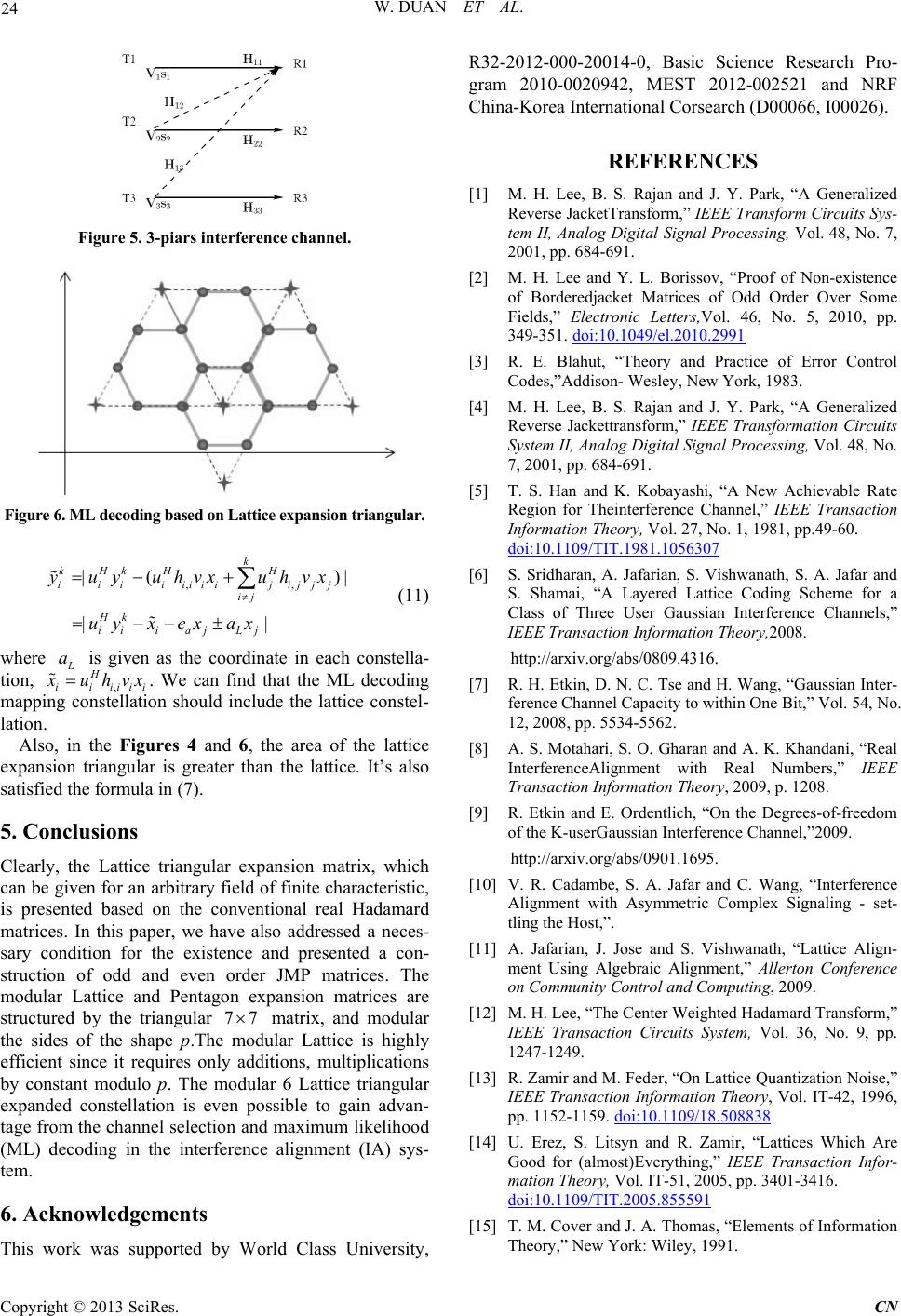
Figure 5. 3-piars interference channel.
Figure 6. ML decoding based on Lattice expansion triangular.
,,
|(
||
k
kHkH H
iiiiiiii jijjj
ij
Hk
iii ajLj
yuyuhvxuhvx
uyx exax
)|
(11)
where
a is given as the coordinate in each constella-
tion, ,i
H
iiiii
uhvx
. We can find that the ML decoding
mapping constellation should include the lattice constel-
lation.
Also, in the Figures 4 and 6, the area of the lattice
expansion triangular is greater than the lattice. It’s also
satisfied the formula in (7).
5. Conclusions
Clearly, the Lattice triangular expansion matrix, which
can be given for an arbitrary field of finite characteristic,
is presented based on the conventional real Hadamard
matrices. In this paper, we have also addressed a neces-
sary condition for the existence and presented a con-
struction of odd and even order JMP matrices. The
modular Lattice and Pentagon expansion matrices are
structured by the triangular 77
matrix, and modular
the sides of the shape p.The modular Lattice is highly
efficient since it requires only additions, multiplications
by constant modulo p. The modular 6 Lattice triangular
expanded constellation is even possible to gain advan-
tage from the channel selection and maximum likelihood
(ML) decoding in the interference alignment (IA) sys-
tem.
6. Acknowledgements
his work was supported by World Class University,
R32-2012-000-20014-0, Basic Science Research Pro-
gram 2010-0020942, MEST 2012-002521 and NRF
China-Korea International Corsearch (D00066, I00026).
REFERENCES
[1] M. H. Lee, B. S. Rajan and J. Y. Park, “A Generalized
Reverse JacketTransform,” IEEE Transform Circuits Sys-
tem II, Analog Digital Signal Processing, Vol. 48, No. 7,
2001, pp. 684-691.
[2] M. H. Lee and Y. L. Borissov, “Proof of Non-existence
of Borderedjacket Matrices of Odd Order Over Some
Fields,” Electronic Letters,Vol. 46, No. 5, 2010, pp.
349-351. doi:10.1049/el.2010.2991
[3] R. E. Blahut, “Theory and Practice of Error Control
Codes,”Addison- Wesley, New York, 1983.
[4] M. H. Lee, B. S. Rajan and J. Y. Park, “A Generalized
Reverse Jackettransform,” IEEE Transformation Circuits
System II, Analog Digital Signal Processing, Vol. 48, No.
7, 2001, pp. 684-691.
[5] T. S. Han and K. Kobayashi, “A New Achievable Rate
Region for Theinterference Channel,” IEEE Transaction
Information Theory, Vol. 27, No. 1, 1981, pp.49-60.
doi:10.1109/TIT.1981.1056307
[6] S. Sridharan, A. Jafarian, S. Vishwanath, S. A. Jafar and
S. Shamai, “A Layered Lattice Coding Scheme for a
Class of Three User Gaussian Interference Channels,”
IEEE Transaction Information Theory,2008.
http://arxiv.org/abs/0809.4316.
[7] R. H. Etkin, D. N. C. Tse and H. Wang, “Gaussian Inter-
ference Channel Capacity to within One Bit,” Vol. 54, No.
12, 2008, pp. 5534-5562.
[8] A. S. Motahari, S. O. Gharan and A. K. Khandani, “Real
InterferenceAlignment with Real Numbers,” IEEE
Transaction Information Theory, 2009, p. 1208.
[9] R. Etkin and E. Ordentlich, “On the Degrees-of-freedom
of the K-userGaussian Interference Channel,”2009.
http://arxiv.org/abs/0901.1695.
[10] V. R. Cadambe, S. A. Jafar and C. Wang, “Interference
Alignment with Asymmetric Complex Signaling - set-
tling the Host,”.
[11] A. Jafarian, J. Jose and S. Vishwanath, “Lattice Align-
ment Using Algebraic Alignment,” Allerton Conference
on Community Control and Computing, 2009.
[12] M. H. Lee, “The Center Weighted Hadamard Transform,”
IEEE Transaction Circuits System, Vol. 36, No. 9, pp.
1247-1249.
[13] R. Zamir and M. Feder, “On Lattice Quantization Noise,”
IEEE Transaction Information Theory, Vol. IT-42, 1996,
pp. 1152-1159. doi:10.1109/18.508838
[14] U. Erez, S. Litsyn and R. Zamir, “Lattices Which Are
Good for (almost)Everything,” IEEE Transaction Infor-
mation Theory, Vol. IT-51, 2005, pp. 3401-3416.
doi:10.1109/TIT.2005.855591
[15] T. M. Cover and J. A. T homas, “Elements of Information
Theory,” New York: Wiley, 1991.
T