Paper Menu >>
Journal Menu >>
 Int. J. Communications, Network and System Sciences, 2012, 5, 850-853 http://dx.doi.org/10.4236/ijcns.2012.512090 Published Online December 2012 (http://www.SciRP.org/journal/ijcns) Improvement of the Round Key Generation of AES Junshe Wang, Han Xu, Mingqiu Yao Department of Communication and Information System, Hebei University of Science and Technology, Shijiazhuang, China Email: kingkaiser@163.com Received August 13, 2012; revised September 27, 2012; accepted November 10, 2012 ABSTRACT The key generation algorithm of AES was introduced, the weaknesses of the key generation design of AES were inves- tigated. According to the key demand put forward a kind of new design idea, and this designing strategy was developed, which can be used to improve the key generation algorithm of AES. An analysis shows that such improvement can en- hance the safety of the original algorithm without reducing its efficiency. Keywords: A ES; Data E nc r yption Standard (DE S); Key Generation; Rijndeal 1. Introduction In modern society, computer network has already been covered. In people’s daily lives, the information technol- ogy industries have become ubiquitous. In the civil and military, commercial’s security which is playing an im- portant role is very prominent [1]. Therefore, the impor- tance of information security has been paid more and more attention. Encryption technology as an important field of information security technology, which is widely considered as the most effective means to ensure informa- tion security. Because of advances in computer technol- ogy and the needs of reality, the cryptology had the de- velopment which progresses by leaps and bounds. In the field of block ciphers, DES was already unable to satisfy requirements of the security, the United States had col- lected and selected the Rijndael algorithm as the new Advanced Encryption Standard (Advanced Encryption Standard = AES). Compared with 3DES, the security of the AES algorithm is better, AES Algorithm is more sim- ple and flexible. First, algorithm of AES is based on group encryption algorithm. Algorithm including massive shifting algo- rithm, and the shift operation belongs to the time instruc- tion. It cannot conduct simultaneously with other instruc- tions, and reduces the efficiency of the algorithm. Second, the rounds of encryption using a loop operation, cyclic operation may cause the instruction block, so the instruc- tion. Therefore, the paper made the improvement slightly in the AES algorithm foundation, and reduced shift op- eration and improved the round key, thereby reducing the encryption and decryption without the premise of im- proving the efficiency of its security. 2. Encryption Algorithm Round Transformation The AES encryption algorithm’s main body is the encryp- ti on round the transfo rmation round transformation includes mainly ByteSub, ShiftRow, MixColumn and AddRound- Key. A. ByteSub transformation It is each byte in the state which is transformed by ByteSub instead of s-boxes transformation. This trans- formation made up of two steps: 1) Multiplicative inverses of each byte in the State. 2) The results which is obtained by (2) to (1) do trans- formation y = f (x). 0 0 1 1 2 2 3 3 44 55 66 77 10001111 1 11000111 1 11100011 0 11110001 0 11111000 0 01111100 1 00111110 1 00011111 0 x y x y x y x y yx yx yx yx B. ShiftRow transformation ShiftRow transform the line of state which increasing the offset of circulation moves left, first line unchanged, sec- ond line loop le ft 1 by t e , t hi rd l i ne l oop l e ft 2 byt es, fourt h line loop left 3 by t e s. C. MixColumn transformation MixColumn transformation makes confuse transforms to columns in the state. In MixColumn transformation, the data of state column as 32-bit, and then carries on the C opyright © 2012 SciRes. IJCNS  J. S. WANG ET AL. 851 matrix multiplication transformation to it: Sjxc xSjx (1) 32 0.30.10.1 0.2cxx xx (2) D. AddRoundKey transformati on The AddRoundKey transformation let each byte in state and the round sub-key corresponding to the byte XOR, the value of the AddRoundKey transformation are the result of state. The round key transformation in pseu- do C code represent ed as fol l o ws: Round(State,Roundkey[i]){ ByteSub(State); ShiftRow(State); MixColumn(St at e); AddRoundKey (Stat e,R oundkey[i]); } 3. Key Analysis of the AES Encryption Algorithm The AES algorithm expands directly the seed key to get the keys. And each 32 bit word i and and k1i k4i k are related, in other words, if it obtained 4i and 1i kk can obtain i. Similarly, if it knew i and kk 1i k may obtain 4i, knew i and 4i kk k may obtain 1i k . Al- though, each round word which produces in a round key can be carried on by 4 integral multiples the complication, the correlation of key generation cannot be changed by this kind of the complication. Suppose, a round of the AES key i, 1i, , 3 is known now. Then, it may be through 1i, 2i obtain , through kkk2k i ki k 1i k1i k , 2i obtain , through , 1i obtain 3i k2i ki kk k , through 1i, i obtain 4i kk k again, the preceding round of the round keys of all sub-keys have been ob- tained. It also through i, 3i obtain 4i, through 1i, obtain 5i k, through 2i k, 5i obtain 6i k kk k k4i kk , through 3i, obtain k6i k7i k , and then get the last round keys. The above key generation process is analyzed to get the following pr op ert i e s: Nature 1: Direct expansion of the key enables itself to have highly effective; Nature 2: The preceding round key is only replied by the generation of the new key, the generation of the new key can participate encryption and decryption, immedi- ately [2]. Therefore, the generation algorithm of the key has timeliness; Nature 3: If one of the round keys is obtained by the aggressor then the complete seed key will be obtained by the aggressor. Namely: The sub-key and the seed key had the relevance. Security of the key generation algorithm is reduced by the nature 3. AES has the high efficiency of the nature 1, basis of the direct expansion. The latter round key is ob- tained by the preceding round key, through the first round of the key as the seed key. Generally speaking, since the latter round key can be promoted by preceding round key, preceding round key is obtained by the latter round key, this is the reason which the nature 3 appears [3]. the main reason is th e seed key which is condu cted on the 4. Algorithm Improvements ing A. 44 keys are generated by dis patc h The AES algorithm’s 128 seed key is produced by us- ing 44 sub-keys. First, the seed key was divided into four words: 0 k, 1 k, 2 k, 3 k, the remaining sub-keys are produce ung a scheduling algori t hm in Figure 1. d bysi And F is: 32 byte position rotate left one byte. Namely: RotByte(a,b,c,d) = (b,c,d,a). B. Cipher The function cipher is the real McCoy, doing the actual encryption of the 16 byte long input vector of plaintext into the outpu t ciphertext vecto r ai illustrated in Figure 2 . Further input parameters of the vipher, that have been created by the initialization function aes_init are the sub- stitution table s-box, the key schedule w, and theological matrix poly_mat. [4] The cipher rearranges the plaint ext vector into the state ma- trix and iteratively loops the state through add_round _key, sub_bytes, shif t_rows, and mix_coulum ns. C. The new algorithm’s advantage—Round Keys Ex- ch 0 round AES algorithm as the example, the ini- tia ange Take 1 l 4 words seed key expands to 44 word sub-key. Among them, Key dependent relationship for: i k de- pends on 1i k and 4i k 4,5, ,43i. First, it ner- ates the oral key.en-keys generated by the seed key and the gradual transformation as Figure 3. Taki ge igin Th, 40 words sub ng 2nd round and the 3rd round key as a group, Ex kes 4 wo 10 w. Tn change 7 k and 9 k;Taking 4th round and the 5th round key a group, Exchange 15 k and 17 k; Taking 6th round and the 7th round key as a groupxchange 23 k and 25 k; Taking 8th round and the 9th round key as oup, Exchange 31 k and 33 k; Taking 10th round and the 11th round key a groupxchange 39 k and 41 k; After exchanging 44 words sub-key, It still s as new round of all 11 round. Take 2nd round and 3rd round new sub-key as the example, it analyzes the corre- lations of each round key after the exchange. Before the exchange, it may derive the 3rd round key through the 2nd round key, it may also derive the 2nd round key ac- cording to the 3rd round key [5]. 2nd round of keys be- come 4 k, 5 k, 6 k, 9 k and 3rd round of keys becomes 8 k, 7 k10 kk af exchange the 8th word and the thordhere-use the relationship between them, it can only through the 2nd round key obtain the 3rd round as , , E a a gras ter , Et rd , 11 Copyright © 2012 SciRes. IJCNS 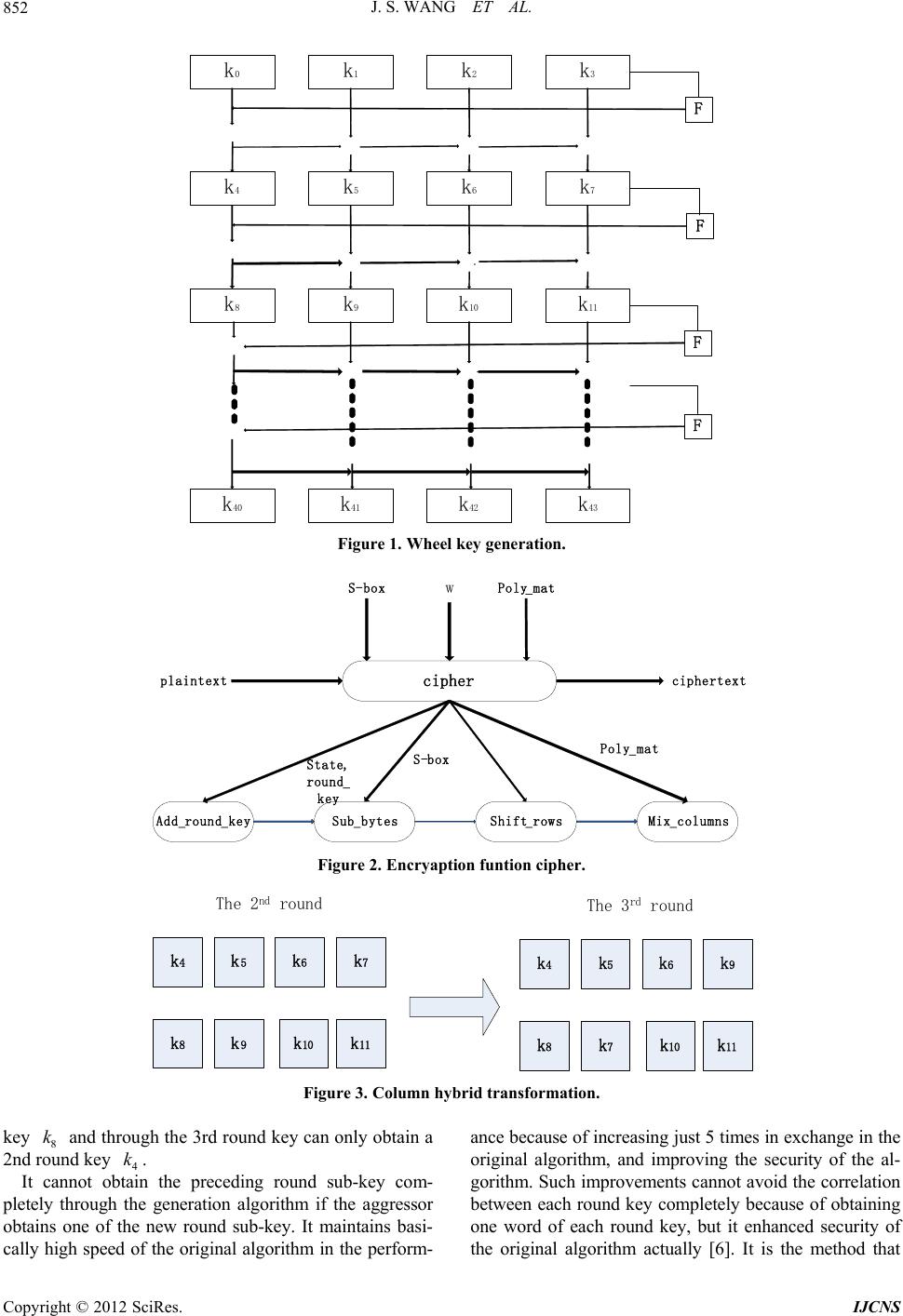 J. S. WANG ET AL. Copyright © 2012 SciRes. IJCNS 852 k0k1k2k3 k7 k10 k5k4 k11 k6 k9k8 k43k42k41k40 F F F F Figure 1. Wheel key gene ration. cipher Sub_bytesAdd_round_key Shift_rows Mix_columns plaintext ciphertext S-box wPoly_mat State, round_ key S-box Poly_mat Figure 2. Encryaption funtion cipher. k4 k8 k7k6k5 k11k10k9 k4 k8k7 k6k5 k10 k9 k11 The 2n d roun d The 3r d round Figure 3. Column hybrid transformation. key and through the 3rd round k ey can only obtain a 8 k 2nd rnd key 4 k. ou It cannot ob tain ance because of increasing just 5 times in exchange in the original algorithm, and improving the security of the al- gorithm. Such improvements cannot avoid the correlation between each round key completely because of obtaining one word of each round key, but it enhanced security of the original algorithm actually [6]. It is the method that the preceding round sub-key com- pletely through the generation algorithm if the aggressor obtains one of the new round sub-key. It maintains basi- cally high speed of the original algorithm in the perform-  J. S. WANG ET AL. 853 the sub-key for the key rotation when produces two new round sub-key every time, therefore, the nature 2 (real- time) of the original AES algorithm have not been de- stroyed by improving the algorithm, and it has not re- duced the efficiency to strengthen security of the original algorithm [7] . D. New algorithm encryption experiment The new improved algorithm is simulated by using mhich obtains atlab. Cipher the Figure 4 completely, w the encryption documents of Figure 4. In the Figure 5, it is a result of the cipher of the im- proved algorithm and the original algorithm. It can see directly, the improved algorithm is more complex than the original algorithm(the black spots are more crowded). Response time of the two algorithms program as the fol- lowing table (see Table 1). Figure 4. The picture of original. The origin gl al gorithm 50 100 150 200 250 50 100 150 200 250 The im proved algorit h m 50 100 150 200 250 50 100 150 200 250 Figure 5. The picture of cipher. Table 1. Response time. Time algorithmFirst (second)Second Third Fourth Original 62.79114 62.39147 62.2351162.46756 Improved 62.34567 62.36778 62.2346862.87953 The table can be seen, response time of the original algorithm is 62.23511 to 62.79114, response time of the improved algorithm is 62.87953 to 62.67890 (seco nd). 5. Summary and Outlook It improves sub-key of the original production algorithm through research of the key production algorithm and demand consideration, to strengthen the security of the original algorithm without reducing efficiency. Algorithm improvement extracts from many merits of improvement algorithm when found one method to strengthen the secu- rity of the origi nal al gori t hm without reducing effici ency . It is unidirectional strategy that th e previous round key has only been produced under the emphasis by the next round key. Although this kind of strategy which research in the AES algorithm is put forward, it also can be used with other groups of the production key as a design thought. This alg orithm will also be studied further in the future. REFERENCES [1] N. Ferguson, J. Kelsey, B. Schneier, et al., “Improved Cryptanalysis of Rijndael, Selected Areas in Cryptogra- phy 2008,” 2009. [2] E. Tittel, M. Chapple and James, “The Authentication In- formation System Security Experts Holographic Tutorial CISSP: Certified Informa,” Publishing House of Elec- tronics Industry, Beijing, 2008. [3] Z. H. Yang, “Testing Efficiency of Encryption Network Security: Theory and Practice,” 2008. [4] J. Daemen and V. Rijmen, “AES Proposal: Rijndael (Ver- sion 2),” 2005. [5] J. Daemen and V. Rijmen, “The Design of Rijndael: AES— The Advanced Encryption Stand,” Springer-Verlag, Ber- lin, 2002. [6] J.-S. Cui and H.-G. Zhang, “MARS Algorithm—Candi- date of Advanced Encryption Standard,” Communication Security, Vol. 22, No. 2, 2000, pp. 59-66. [7] B. Yang, “Modern Cryptology,” Publishing House of Tsing- hua University, Beijing, 2009. Copyright © 2012 SciRes. IJCNS |

