 Journal of Information Security, 2012, 3, 326-334 http://dx.doi.org/10.4236/jis.2012.34040 Published Online October 2012 (http://www.SciRP.org/journal/jis) Dynamic Identity Based Authentication Protocol for Two-Server Architecture Sandeep K. Sood Department of Computer Science & Engineering, Regional Campus Gurdaspur, Gurdaspur, India Email: san1198@gmail.com Received July 17, 2012; revised August 23, 2012; accepted September 3, 2012 ABSTRACT Most of the password based authentication protocols make use of the single authentication server for user’s authentica- tion. User’s verifier information stored on the single server is a main point of susceptibility and remains an attractive target for the attacker. On the other hand, multi-server architecture based authentication protocols make it difficult for the attacker to find out any significant authentication information related to the legitimate users. In 2009, Liao and Wang proposed a dynamic identity based remote user authentication protocol for multi-server environment. However, we found that Liao and Wang’s protocol is susceptib le to malicious server attack and malicious user attack. This paper presents a novel dynamic identity based authentication protocol for multi-server architecture using smart cards that re- solves the aforementioned flaws, while keeping the merits of Liao and Wang’s protocol. It uses two-server paradigm by imposing different levels of trust upon the two servers and the user’s verifier information is distributed between these two servers known as the service provider server and the control server. The proposed protocol is practical and compu- tational efficient because only nonce, one-way hash function and XOR operations are used in its implementation. It provides a secure method to change the user’s password without the server’s help. In e-commerce, the number of serv- ers providing the services to the user is usually more than one and hence secure authentication protocols for multi-server environment are required. Keywords: Authentication Protocol; Smart Card; Dynamic Identity; Multi-Server Architectur e; Password 1. Introduction Most of the existing password authentication protocols are based on single-server model in which the server stores the user’s password verifier information in its da- tabase. Password verifier information stored on the single server is mainly susceptible to stolen verifier attack. The concept of multi-server model removes this common poin t of susceptibility. The proposed protocol uses multi-server model consisting of two servers at the server side that work together to authenticate the users. Different levels of trust are assigned to the servers and the service pro- vider server is more exposed to the clients than that of the control server. The back-end control server is not directly accessible to the clients and thus it is less likely to be attacked. Two-server mo del provides the flexibility to distribute user passwords and the authentication func- tionality into two servers to eliminate the main point of vulnerability of the single-server model. Therefore, two- server model appears to be a genuine choice for practical applications. In a single server environment, the issue of remote login authentication with smart cards has already been solved by a variety of schemes. These conventional sin- gle-server password authentication protocols can not be directly applied to multi-server environment because each user needs to remember different sets of identities and passwords. Different protocols have been suggested to access the resources of multi-server environment. A se- cure and efficient remote user authentication protocol for multi-server environment should provide mutual authen- tication, key agreement, secure password update, low computation requirements and resistance to different fea- sible attacks. A number of static identity based remote user authen- tication protocols have been proposed to improve secu- rity, efficiency and cost. The user may change his pass- word but can no t chang e his iden tity in password au then- tication protocols. During communication, the static iden- tity leaks out partial information abou t the user’s authen- tication messages to the attacker. Most of the password authentication protocols for multi-server environment are based on static identity and the attacker can use this in- formation to trace and identify the different requests be- longing to the same user. On the other hand, the dynamic identity based authentication protocols provide two-factor authentication based on the identity and password and C opyright © 2012 SciRes. JIS  S. K. SOOD 327 hence more suitable to e-commerce applications. The aim of this paper is to provide a dynamic identity based secure and computational efficient authentication proto- col with user’s anonymity for multi-server environment using smart cards. It protects the user’s identity in inse- cure communication channel and hence can be applied directly to e-economic applications. This paper is organized as follows. In Section 2, we explore the literature on ex isting authentication protocols for multi-server environment. Section 3 reviews the dy- namic identity based remote user authentication protocol for multi-server environment proposed by Liao and Wa ng . Section 4 describ es the su sceptib ility o f Liao an d W ang’s protocol to malicious server attack and malicious user attack. In Section 5, we present dynamic identity based authentication protocol for multi-server architecture us- ing smart cards. Section 6 discusses the security analysis of the proposed protocol. The comparison of the cost and functionality of the proposed protocol with other related protocols is shown in Section 7. Section 8 concludes the paper. 2. Related Work A number of smart card based remote user authentication protocols have been proposed due to the convenience and secure computation provided by the smart cards. How- ever, most of these protocols do not protect the user’s identities in authentication process. User’s anonymity is an important issue in many e-commerce applications. In 2000, Ford and Kaliski [1] propo sed the first multi- server password based authentication protocol that splits a password among multiple servers. This protocol gene- rates a strong secret using password based on the com- munications exchanges with two or more independent servers. The attacker can not compute the strong secret unless all the servers are compromised. This protocol is highly computation intensive due to the use of public keys by the servers. Moreover, the user requires a prior secure authentication channel with the server. Therefore in 2001, Jablon [2] improved this protocol and proposed multi-server password authentication protocol in which the servers do not use public keys and the user does not require prior secure communication channels with the servers. In 2003, Lin et al. [3] proposed a multi-server authen- tication protocol based on the ElGamal digital signature scheme that uses simple geometric properties of the Euclidean and discrete logarithm problem concept. The server does not require keeping any verification table but the use of public keys makes this protocol computation intensive. In 2004, Juang [4] proposed a smart card based multi-server authentication protocol using symmetric en- cryption algorithm without maintaining any verification table on the server. In 2004, Ch ang and Lee [5] impro ved Juang’s protocol and proposed a smart card based multi- server authentication protocol using symmetric encryp- tion algorithm without any verification table. Their pro- tocol is more efficient than the multi-server authentica- tion protocol of Juang [4]. In 2007, Hu et al. [6] pro- posed an efficient password authentication key agree- ment protocol for multi-server architecture in which user can access multiple servers using smart card and one weak password. The client and the server authenticate each other and agree on a common secret session key. The proposed protocol is more efficient and more user friendly than that of Chang and Lee [5] protocol. In 2006, Yang et al. [7] proposed a password based user authentication and key exchange protocol using two- server architecture in which only a front-end server com- municates directly with the users and a control server does not interact with the users directly. The concept of distributing the password verification information and authentication functionality into two servers requires addi - tional efforts from an attacker to co mp r o mise tw o s e rv e r s to launch successful offline dictionary attack. In 2008, Tsai [8] proposed a multi-server authentication protocol using smart cards based on the nonce and one-way hash function that does not require storing any verification table on the server and the registration center. The pro- posed authentication protocol is efficient as compared to other such related protocols because it does not use any symmetric and asymmetric encryption algorithm for its implementation. In 2009, Liao and Wang [9] proposed a dynamic identity based remote user authentication pro- tocol using smart cards to achieve user’s anonymity. This protocol uses only hash function to implement a strong authentication for the multi-server environment. It pro- vides a secure method to update the user’s password without the help of trusted third party. In their paper, they claimed that suggested protocol can resist various known attacks. However, we show in Section 4 that their protocol is insecure in the presence of an active attacker. In 2009, Hsiang and Shih [10] also found that Liao and Wang’s protocol is susceptible to insider attack, mas- querade attack, server spoofing attack, registration center spoofing attack and is no t reparable. Furthermore, it fails to provide mutual authentication. To remedy these flaws, Hsiang and Shih proposed an improvement over Liao and Wang’s pro tocol. In 2010, Sood et al. [11] found that Hsiang and Shih protocol is also found to be flawed for replay attack, impersonation attack and stolen smart card attack. 3. Review of Liao and Wang’s Protocol In this section, we describe the dynamic identity based remote user authentication protocol for multi-server en- vironm ent proposed by Liao a nd Wang [9]. The nota t i ons used in this sectio n are listed in Table 1 and the protocol Copyright © 2012 SciRes. JIS  S. K. SOOD Copyright © 2012 SciRes. JIS 328 is shown in Figure 1. 3.1. Registration Phase The user Ui has to submit his identity IDi and password Pi to registration center RC so that he can access the re- sources of the service provider server SJ. The RC computes iiiiiiii THIDx,VTHIDP,BHP Hx and i . Then RC issues the smart card with secret parameters (Vi, Bi, Di, H ( ), y) to the user Ui through a secure communication channel. i DHT 3.2. Login Phase The user Ui submits his identity , password and the server identity SIDJ to smart card in order to login on to the service provider server SThe smart card com- putes * i ID J. * i P ** H i ** * TVHIDP,D T i iiii and then veri- fies the equality of calculated value of with the sto r ed value of Di in its memory. If both values of Di match, the legitimacy of the user is assured and smart card proceeds to the next step. Otherwise the login request from the user Ui is rejected. Then smart card generates nonce value Ni and computes * i D ii iiiJii CIDHPHTyN, PTHyNSID J and ii QHByN i . Afterwards, smart card sends the login request message (CIDi, PiJ, Qi, Ni) to the server SJ. 3.3. Mutual Verification and Session Key Agreement Phase The server SJ computes iiJi Jiiii ii TP HyNSID,HPCIDHTyN, BHP Hx and i *ii QHByN, and then compares the computed Table 1. Notations. Ui i th User SJ J th Server RC Registration Center IDi Unique Identification of User Ui Pi Password of User Ui SIDJ Unique Identification of Server SJ CIDi Dynamic Identity of User Ui H ( ) One-Way Hash Function x Master Secret of Registr ation Center y Shared Secret Key of Registration Center & All Servers XOR Operation | Concatenation Figure 1. Liao and Wang’s dynamic identity based on multi-server authentication protocol.  S. K. SOOD 329 value of i with the received value of Qi. If they are not equal, the server SJ rejects the login request and ter- minates this session. Otherwise, the server SJ generates nonce value NJ and computes * Q iJ ii J and sends the message (MiJ1, NJ) back to smart card of the user Ui. On receiving the message (MiJ1, NJ), the user Ui’s smart card com pute s M1 HBNySID iJ ii J and compares the computed value of MiJ1* with the received value of MiJ1. This equivalency authenticates the legiti- macy of the service provider server SJ else the connec- tion is interrupted. Then the user Ui’s smart card com- putes * M1 HBNySID HBNySID iJ iJ J and sends MiJ2 back to the service provider server SJ. On receiving the message MiJ2, the service provider server SJ computes M2 iJ *iJ J M2 HBNySID and compares the computed value of MiJ2* with the received value of MiJ2. This equivalency assures the legitimacy of the user Ui. After finishing mutual authentication, the user Ui and the ser- vice provider server S computes J iiJ J SKHBNNySID as the session key. 4. Cryptanalysis of Liao and Wang’s Protocol Liao and Wang [9] claimed that their protocol provides identity privacy and can resist various known attacks. However, we found that this protocol is flawed for mali- cious server attack and malicious user attack. 4.1. Malicious Server Attack The malicious legitimate server SJ can compute th e value of Ti, H(Pi) and Bi corresponding to the user Ui during mutual verification and session key agreement phase. This malicious server SJ also knows H ( ) function, y and H(x) because Liao and Wang mentioned that y is the shared key among the users, the servers and the registra- tion center and H (x) is used by the legitimate server SJ to compute . The malicious server SJ can record ii BHP Hx Mik2, the service provider server Sk computes * iki kk M2 HBNySID and compares it with the received value of Mik2. This equivalency assures the le- gitimacy of the user Ui. After the completion of mutual authentication phase, the malicious server masquerading as the user Ui and the service provider Sk computes iik k SKHBNNy SID as the session key. 4.2. Malicious User Attack The malicious privileged user Um can extract information like y and mm BHP Hx from his own smart card. He can also intercept the login request message (CIDi, PiJ, Qi, Ni) of the user Ui to the service provider SJ. This malicious user Um can compute mmiiJ iJ iiii HxBHP,TPHyNSID , HPCID HTyN and im BHP Hx. Now this malicious user Um can choose random nonce value Nm and computes ii imiJim CID=H PH T yN,PTHyNSID J and iim and masquerade as the legiti- mate user Ui by sending the login request message (CIDi, PiJ, Qi, Nm) to the service provider server SJ. The service provider server SJ computes QHByN i iiJm Jiiim * ii im TP HyNSID,HPCIDHTyN, BHPHx,QHByN yN,Q = HByN ii CIDH PH T iii ii , Ni during login request message from the user Ui and computes ik iik PTHyNSID and compares the equality o f calculated value of Qi* with the received value of Qi to verify the legitimacy of the user Ui. Afterwards, the server SJ generates nonce value NJ, computes iJi mJ M1 HBN ySID and sends the message (MiJ1, NJ) back to the malicious user Um who is masquerading as the user Ui. On receiving the message (MiJ1, NJ), the malicious user Um computes iJi JJ M2 HBNySID and sends MiJ2 back to the service provider server SJ. On receiving the message MiJ2, the service provider server SJ computes * iJi JJ M2 HBNySID and compares the computed value of MiJ2* with the received value of MiJ2 to verify the legitimacy of the user Ui. After finishing mutual au- thentication phase, the malicious user Um masquerading as the user Ui and the service provider server SJ computes imJ J SKHBNNy SID as the session key. corresponding to the user Ui. Afterwards, the malicious server SJ sends the login request message (CIDi, Pik, Qi, Ni) to the service provider server Sk by masquerading as the user Ui. The service provider server Sk authenticates the received messages by calculating Qi* from the received messages and checks its equivalency with the received value of Qi. After that, the server Sk generates a nonce value Nk and computes iki ik M1 HBNySID5. Proposed Protocol and sends the mes- sage (Mik1, Nk) back to the malicious server SJ who is masquerading as the user Ui. On receiving the message (Mik1, Nk), the malicious server SJ computes In this section, we propose a dynamic identity based au- thentication protocol for multi-server architecture using smart cards that is free from all the attacks considered above. The notations used in this section are listed in Table 2 and the protocol is summarized in Figure 2. M2 HBNySID ikikk and sends Mik2 back to the service provider server Sk. On receiving the message Copyright © 2012 SciRes. JIS  S. K. SOOD 330 Table 2. Notations. Ui i th User Sk K th Service Provider Server RC Control Server IDi Unique Identity of User Ui Pi Password of User Ui H ( ) One-Way Hash Function SIDK Unique Identity of kth Service Provider Server yi Random Value chosen by CS for User Ui x Master Secret Parameter of Server CS N1 R an d om Nonce Value Generated by User’s Smart Card N2 Random Nonce Value Generated by Server Sk N3 Random Nonce Value Generated by Server CS XOR Operation | Concatenation Figure 2. Dynamic identity based multi-server authentication protocol. 5.1. Registration Phase The user Ui has to submit his identity IDi and password Pi to the control server CS for its registration over a se- cure communication channel. Step 1: Ui CS: IDi, Pi The control server CS computes the security parame- ters 2 iii iii iiiii ZH IDPHx ,VyIDH x , BHIDPPy and iii CHy IDx x , where x is the secret key of the CS and yi is the random value chosen by the CS for the user Ui. The server CS chooses the value of yi corre- sponding to the user Ui in such a way so that the value of Ci must be unique for each user. The server CS stores i y corresponding to Ci in its client’s database. Then the server CS issues smart card containing security pa- rameters (Zi, Vi, Bi, H ( )) to the user Ui through a secure communication channel. Step 2: CS Ui: Smart card All service provider servers register themselves with Copyright © 2012 SciRes. JIS  S. K. SOOD 331 CS and CS agrees on a unique secret key SKk with each service provider server Sk. The server Sk remembers the secret key SKk and CS stores the secret key SKk as k SKHx SIDk corresponding to service provider server identity SIDk in its service provider server’s data- base. Step 3: CS Sk: IDi, H (yi) The CS sends IDi and H (yi) corresponding to newly registered user Ui to all service provider servers. Each service provider server stores IDi and H (yi) in its data- base. 5.2. Login Phase The user Ui inserts his smart card into a card reader and submits his identity , password and the server identity SIDk to smart card in order to login on to the service provider server Sk. Then smart card computes * i ID * i P ** ** iiiiii ii ***2 iii y=BH IDPP,HxVyID, ZHIDP Hx and compares the computed value of Zi* with the stored value of Zi in its memory to verifies the legitimacy of the user Ui. Step 1: Smart card checks ?= Zi * i Z After verification, smart card generates random nonce value N1 and computes 2 iii1i CID=VyHyN, M=HxN 1 and ii 1i EHyHxNIDSIDk . Then smart card sends the login request message (SIDk, CIDi, Mi, Ei) to the service provider server Sk. Step 2: Smart card Sk: SIDk, CIDi, Mi, Ei 5.3. Authentication and Session Key Agreement Phase After receiving the login request from the user Ui, the server Sk generates random nonce value N2, computes Gi = N2 SKk and sends the login request message (SIDk, CIDi, Mi, Ei, Gi) to the control server CS. Step 1: Sk CS: SIDk, CIDi, Mi, Ei, Gi The control server CS computes 2 1i2ik * ii1 NMHx,NGSK CCIDNHxx , and finds the matching value of Ci corresponding to Ci* from its client database. Step 2: Server CS checks Ci* ?= Ci If the value of Ci* does not match with any value of Ci in its client database, the CS rejects the login request and terminates this session. Otherwise, the CS extracts yi from yi x corresponding to Ci* from its client database. Then the CS comp utes * ii ii i1i IDCHyx, E HyHx NIDSID k and compares Ei* with the received value of Ei to verifies the legitimacy of the user Ui and the service provider server Sk. Step 3: Server CS checks Ei* ?= Ei If they are not equal, the CS rejects the login request and terminates this session. Otherwise, the CS extracts SKk from kk corresponding to SIDk in its service provider server’s database. Then the CS gen- erates random nonce value N3, computes SKHx SID i13kii123 i123ii i23 ii1 ANNHSK,DIDHNN N FHHNNN IDHy, TNN HyIDHxN , and sends the message (Ai, Di, Fi, Ti) back to the service provider server Sk. The server Sk computes 13ik NNAHSK from Ai and ii 123 IDDH NNN from Di. Then the server Sk extracts H(yi) corresponding to IDi from its database. Afterwards, the server Sk computes i *123i i FHHNN NIDHy and compares Fi* with the received value of F i to verifies the legitimacy of the control server CS. Step 4: Server Sk checks Fi* ?= Fi Then the server Sk sends (Fi, Ti) to smart card of the user Ui. Then smart card computes i 23i ii1 *123i i N=THy IDHxN, FHHNN NIDHy and compares the computed value of Fi* with the re- ceived value of Fi. Step 5: Smart card checks Fi* ?= Fi This equivalency authenticates the legitimacy of the control server CS, the server Sk and the login request is accepted else the connection is interrupted. Finally, the user Ui’s smart card, the server Sk and the control server CS agree on the common session key as i1 23i SKH IDNNNH y. 5.4. Password Change Phase The user Ui can change his password without the help of control server CS. The user Ui inserts his smart card into a card reader and enters his identity IDi* and password Pi* corresponding to his smart card. Smart card computes Copyright © 2012 SciRes. JIS  S. K. SOOD 332 ii ii iii ** ** ii ii ***2 yBHIDPP, HxVyID, ZHIDPHx and compares the computed value of Zi* with the stored value of Zi in its memory to verifies the legitimacy of the user Ui. Once the authenticity of card holder is verified, the smart card asks the card holder to resubmit a new password Pinew. Finally, the value of 2 iii iiii ZHIDPHx and BHIDPPy i stored in the smart card is updated with i new new iiii ZZHIDPHIDP i and i newnew new iiiii BBHIDPPHIDP P ii 1 . 6. Security Analysis Smart card is a memory card that uses an embedded mi- cro-processor from smart card reader machine to perform required operations specified in the protocol. Kocher et al. [12] and Messerges et al. [13] pointed out that all ex- isting smart cards can not prevent the information stored in them from being extracted like by monitoring their power consumption. Some other reverse engineering techniques are also available for extracting information from smart cards. That means once a smart card is stolen by the attacker, he can extract the information stored in it. A good password authentication scheme should provide protection from different possible attacks relevant to that protocol. 1) Malicious server attack: A malicious privileged server Sk can monitor the authentication process of the user Ui and can gather information related to the user Ui. The malicious server Sk can gather information 2 iiii 1i CIDVyHyN, MHxN and ii 1i EHyHxNIDSIDk during login phase corresponding to the legitimate user Ui. This malicious server Sk can not compute IDi, yi and x from this infor- mation. This malicious server Sk can compute the iden- tity IDi from Di and can extract H(yi) corresponding to IDi from its database corresponding to the user Ui during authentication and session key agreement phase. To masquerade as the legitimate user Ui, this malicious server Sk who knows the identity IDi has to guess yi and H(x) correctly at the same time. It is not possib le to guess out two parameters correctly at the same time in real polynomial time. In another option, this malicious server Sk has to get smart card of the user Ui and has to guess the correct password Pi in order to login on to the server Sm. It is not possible to guess the password Pi correctly in real polynomial time even after getting the smart card of legitimate user Ui and after knowing the identity IDi of the user Ui. Therefore, the proposed protocol is secure against malicious server attack. 2) Malicious user attack: A malicious privileged user Ui having his own smart card can gather information like 2 iii iii ZHIDPHx, VyIDHx and iiiii BHIDPPy from the memory of smart card. The malicious user Ui can compute the value of H(x) from this information. The value of CIDm, Mm and Em is smart card specific and the malicious user Ui requires to know the values of H(x), ym and IDm to masquerade as the legitimate user Um. Therefore, this malicious user Ui has to guess ym and IDm correctly at the same time. It is not possible to guess out two parameters correctly at the same time in real polynomial time. Therefore, the pro- posed protocol is secure against malicious user attack. 3) Stolen smart card attack: In case a user Ui’s smart card is stolen by an attacker, he can extract the informa- tion stored in the smart card. An attacker can extract 2 iii iii ZHIDPHx, VyIDHx and iiiii BHIDPPy from the memory of smart card. Even after gathering this information, an attacker has to guess minimum two parameters out of IDi, H(x), yi and Pi correctly at the same time. It is not possible to guess out two parameters correctly at the same time in real polynomial time. Therefore, the proposed protocol is secure against stolen smart card attack. 4) Identity protection: Our approach provides iden- tity protection in the sen se that instead of sen ding th e real identity IDi of the user Ui in authentication, the pseudo identification 1 is generated by smart card corresponding to the legitimate user Ui fo r its authentication to the serv ice prov ider serv er Sk an d th e control server CS. There is no real identity information about the user during the log in and authentication & ses- sion key agreement phase. This approach provides the privacy and unlinkability among different login requests belonging to the same user. The attacker can not link different sessions belonging to the same user. iii i CIDVyHyN 5) Offline dictionary attack: In offline dictionary at- tack, the attacker can record messages and attempts to guess user’s identity IDi and password Pi from recorded messages. An attacker first tries to obtains identity and password verification information such as 2 iii iiii ZHIDPHx, BHIDPPyi and then try to guess the identity IDi and password Pi by offline guessing. Here an attacker has to guess the iden- tity IDi and password Pi correctly at the same time. It is not possible to guess two parameters co rrectly at the s am e time in real polynomial time. Therefore, the proposed Copyright © 2012 SciRes. JIS  S. K. SOOD Copyright © 2012 SciRes. JIS 333 protocol is secure against offline dictionary attack. 6) Replay attack: In this type of attack, the attacker first listens to communication between the user and the server and then tries to imitate the user to login on to the server by resending the captured messages transmitted between the user and the server. Replaying a message of one session into another session is useless because the user’s smart card, the server Sk and the control server CS choose different nonce values (N1, N2, N3) in each new session, which make all messages dynamic and valid for that session only. Therefor e, replaying old dynamic iden- tity and user’s verifier information is useless. Moreover, the attacker can not compute the session key i1 23i SKH IDNNNH y because the user Ui’s smart card, the server Sk and the control server CS contributes different nonce values (N1, N2, N3) in each new session and the attacker does not know the value of IDi, N1, N2, N3 and H(yi). Therefore, the proposed protocol is secure against replay attack. 7) Mutual authentication: The goal of mutual au- thentication is to establish an agreed session key among the user Ui, the service provider server Sk and the control server CS. All three parties contribute their random nonce values as N, Nand N for the derivation of session key 12 3 i1 23i SKH IDNNNH y . The control s er v er CS authenticates the user Ui using verifier information as * EH yHxNIDSID ii1 ik , the service provider server Sk authenticates the server CS using i *123i i FHHNNNIDHy and the user Ui authenticates the server Sk and the server CS using i123i i . The proposed protocol satisfies strong mutual authentication. * FHHNN NIDHy 7. Cost and Functionality Analysis An efficient authentication protocol must take commu- nication and computation cost into consideration during user’s authentication. The cost comparison of the pro- posed protocol with the relevant smart card based au- thentication protocols is su mmarized in Tabl e 3. A ssume that the identity IDi, password Pi, x, yi, nonce values (N1, N2, N3) are all 128 bit long and prime modular operation is 1024 bits long as in most of practical implementations. Moreover, we assume that the output of secure one-way hash function and the block size of secure symmetric cryptosystem are 128 bits. Let TH, TSYM and TEXP are defined as the time complexity for hash function, sym- metric encryption/decryption and exponential operation respectively. Typically, time complexity associated with these operations can be roughly expressed as TEXP TSYM > TH. In the proposed protocol, the parameters stored in the smart card are Zi, Vi, Bi and the memory needed (E1) in the smart card is ) bits. The communication cost of authentication (E2) includes the number of communication parameters involved in the authentication protocol. The number of communication parameters is {SIDk, CIDi, Mi, Ei, Gi, Ai, Di, Fi, Ti} and hence the communication cost of authentication (E2) is 384 3128 1152 9128 bits. The computation cost of registra- tion (E3) is the total time of all operations executed by the user Ui in the registration phase. The computation cost of registration (E3) is 4TH. The computation cost of the user (E4) is the time spent by the user during the process of authentication. Therefore, the computation cost of the user (E4) is 8TH. The computation cost of the service provider server and the control server (E5) is the time spent by the service provider server and the control server during the process of authentication. Therefore, the computation cost of the service provider server and the control server (E5) is 12TH. The proposed protocol uses the control server CS and the service provider server Sk for the user’s authentica- tion that is why the computation cost of the servers (E5) is high as compared to Liao and Wang protocol [9]. On the other hand, the protocol proposed by Liao and Wang in 2009 totally relies on the service provid er server Sk for the user’s authentication and hence susceptible to mali- cious server attack and malicious user attack. The pro- posed protocol maintains the user’s anonymity by gener- ating dynamic identity and free from different attacks. The proposed protocol requires very less computation as compared to other related protocols and also highly se- cure as compared to these related protocols. The func- tionality comparison of the proposed protocol with the relevant smart card based authentication protocols is sum- marized in Table 4. Table 3. Cost comparison among related smart card based authentication protocols. Proposed Protocol Liao & Wang [9] Hsiang & Shih [10]Chang & Lee [5] Juang [4] Lin et al. [3] E1 384 bits (0.375 |n|) 512 bits (0.5 |n|) 640 bits (0.625 |n|) 256 bits (0.25 |n|) 256 bits (0.25 |n| ) (4t + 1) |n| bits E2 9*128 bits (1.125 |n| ) 7*128 bits (0.875 |n|) 14 *128 bits (1.75 |n|)5*12 8 bits (0.625 |n|)9*128 bits (1.125 |n|) 7*1024 bits (7 |n| ) E3 4TH T 5TH T 6TH T 2TH < T TH << T 5tT E4 8TH T 9TH T 10TH T 4TH + 3TSYM T3T H + 3TSYM T 2T E5 12TH T 6TH T 13TH T 4TH + 3TSYM T4T H + 8TSYM T 7T t: Number of servers; T: T i me complexity of a modular exponential communication i n : | n | = 1024 bits. * n Z 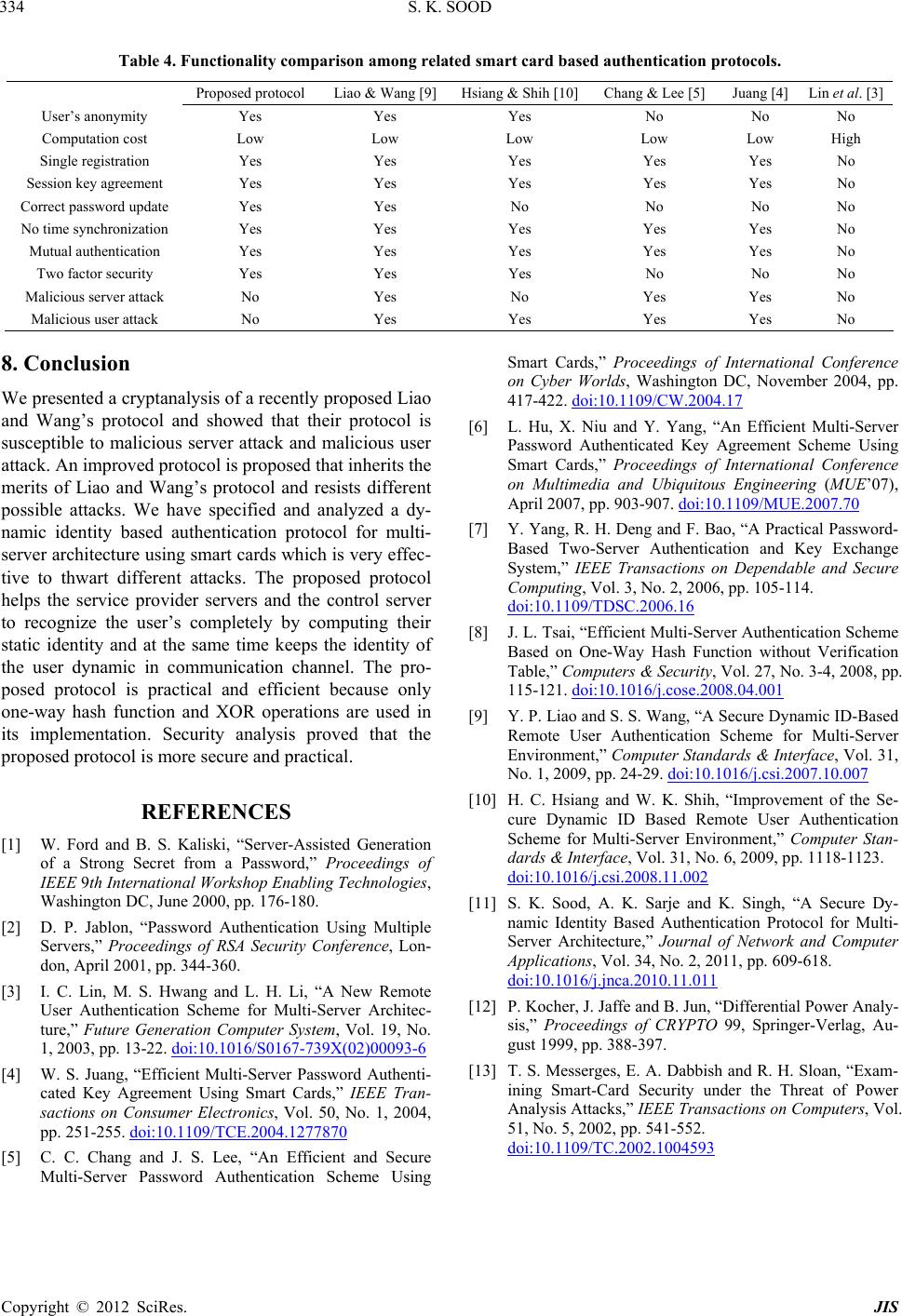 S. K. SOOD 334 Table 4. Functionality comparison among related smart card based authentication protocols. Proposed protocol Liao & Wang [9] Hsiang & Shih [10]Chang & Lee [5] Juang [4] Lin et al. [3] User’s anonymity Yes Yes Yes No No No Computation cost Low Low Low Low Low High Single registration Yes Yes Yes Yes Yes No Session key agreement Yes Yes Yes Yes Y es No Correct password update Yes Yes No No No No No time synchronization Yes Yes Yes Yes Yes No Mutual authentication Yes Yes Yes Yes Yes No Two factor security Yes Yes Yes No No No Malicious server attack No Yes No Yes Yes No Malicious user attack No Yes Yes Yes Yes N o 8. Conclusion We presented a cryptanalysis of a recently proposed Liao and Wang’s protocol and showed that their protocol is susceptible to malicious server attack and malicious user attack. An improved protocol is proposed that inherits the merits of Liao and Wang’s protocol and resists different possible attacks. We have specified and analyzed a dy- namic identity based authentication protocol for multi- server architecture using smart cards which is very effec- tive to thwart different attacks. The proposed protocol helps the service provider servers and the control server to recognize the user’s completely by computing their static identity and at the same time keeps the identity of the user dynamic in communication channel. The pro- posed protocol is practical and efficient because only one-way hash function and XOR operations are used in its implementation. Security analysis proved that the proposed protocol is more secure and practical. REFERENCES [1] W. Ford and B. S. Kaliski, “Server-Assisted Generation of a Strong Secret from a Password,” Proceedings of IEEE 9th International Workshop Enabling Technologies, Washington DC, June 2000, pp. 176-180. [2] D. P. Jablon, “Password Authentication Using Multiple Servers,” Proceedings of RSA Security Conference, Lon- don, April 2001, pp. 344-360. [3] I. C. Lin, M. S. Hwang and L. H. Li, “A New Remote User Authentication Scheme for Multi-Server Architec- ture,” Future Generation Computer System, Vol. 19, No. 1, 2003, pp. 13-22. doi:10.1016/S0167-739X(02)00093-6 [4] W. S. Juang, “Efficient Multi-Server Password Authenti- cated Key Agreement Using Smart Cards,” IEEE Tran- sactions on Consumer Electronics, Vol. 50, No. 1, 2004, pp. 251-255. doi:10.1109/TCE.2004.1277870 [5] C. C. Chang and J. S. Lee, “An Efficient and Secure Multi-Server Password Authentication Scheme Using Smart Cards,” Proceedings of International Conference on Cyber Worlds, Washington DC, November 2004, pp. 417-422. doi:10.1109/CW.2004.17 [6] L. Hu, X. Niu and Y. Yang, “An Efficient Multi-Server Password Authenticated Key Agreement Scheme Using Smart Cards,” Proceedings of International Conference on Multimedia and Ubiquitous Engineering (MUE’07), April 2007, pp. 903-907. doi:10.1109/MUE.2007.70 [7] Y. Yang, R. H. Deng and F. Bao, “A Practical Password- Based Two-Server Authentication and Key Exchange System,” IEEE Transactions on Dependable and Secure Computing, Vol. 3, No. 2, 2006, pp. 105-114. doi:10.1109/TDSC.2006.16 [8] J. L. Tsai, “Efficient Multi-Server Authentication Scheme Based on One-Way Hash Function without Verification Table,” Computers & Security, Vol. 27, No. 3-4, 2008, pp. 115-121. doi:10.1016/j.cose.2008.04.001 [9] Y. P. Liao and S. S. Wang, “A Secure Dynamic ID-Based Remote User Authentication Scheme for Multi-Server Environment,” Computer Standards & Interface, Vol. 31, No. 1, 2009, pp. 24-29. doi:10.1016/j.csi.2007.10.007 [10] H. C. Hsiang and W. K. Shih, “Improvement of the Se- cure Dynamic ID Based Remote User Authentication Scheme for Multi-Server Environment,” Computer Stan- dards & Interface, Vol. 31, No. 6, 2009, pp. 1118-1123. doi:10.1016/j.csi.2008.11.002 [11] S. K. Sood, A. K. Sarje and K. Singh, “A Secure Dy- namic Identity Based Authentication Protocol for Multi- Server Architecture,” Journal of Network and Computer Applications, Vol. 34, No. 2, 2011, pp. 609-618. doi:10.1016/j.jnca.2010.11.011 [12] P. Kocher, J. Jaffe and B. Jun, “Differential Power Analy- sis,” Proceedings of CRYPTO 99, Springer-Verlag, Au- gust 1999, pp. 388-397. [13] T. S. Messerges, E. A. Da bbish and R. H. Sloan, “Exam- ining Smart-Card Security under the Threat of Power Analysis Attacks,” IEEE Transactions on Computers, Vol. 51, No. 5, 2002, pp. 541-552. doi:10.1109/TC.2002.1004593 Copyright © 2012 SciRes. JIS
|