International Journal of Communications, Network and System Sciences
Vol.08 No.09(2015), Article ID:59828,15 pages
10.4236/ijcns.2015.89033
Implementation and Evaluation of Dual-Purpose Normal and Disaster Situations System Based on Delay and Disruption Tolerant Bluetooth MANETs
Yuya Minami*, Yuya Kitaura, Yuri Tsutsui, Eitaro Kohno, Shinji Inoue, Tomoyuki Ohta, Yoshiaki Kakuda*
Graduate School of Information Sciences, Hiroshima City University, Hiroshima, Japan
Email: *minami@nsw.info.hiroshima-cu.ac.jp, *kakuda@hiroshima-cu.ac.jp
Copyright © 2015 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 2 July 2015; accepted 20 September 2015; published 23 September 2015
ABSTRACT
Dual-purpose systems for both normal and disaster situations are necessary for providing continuous services from normal situations to disaster situations. We have been developing the dual- purposed systems based on the assurance network design principle. The assurance network design principle makes the dual-purpose systems work stably in both normal and disaster situations. This paper proposes a connectivity-dependent data propagation scheme, in which each terminal transfers data adaptively by wireless multi-hop data transfer or store-and-forward data transfer depending on whether the terminal has connections to its neighboring terminals. To verify the resilience against disconnection among neighboring terminals, we show field experimental results on data propagation time. Also we propose the dual-purpose system, in which there are two types of graphical user interface (GUI) for both situations. Whenever each terminal receives a special packet in disaster situations, the GUI automatically switches from one type for normal situations to another type for disaster situations. We have unified these two types of GUI so that users can understand how to use them even when GUI is automatically switched. To validate feasibility of the dual-purpose normal and disaster situations system, we show experimental results on dissemination of assessment information and automatical switching of GUIs.
Keywords:
Android, Bluetooth MANET, GUI, Dual-Purpose System, Data Propagation, Wireless Multi-Hop Data Transfer, Epidemic Routing

1. Introduction
A new concept called “assurance networks” has been proposed in [1] . In design principle of assurance networks, failure is regarded as dynamic variation and network structure is reconfigured by network elements for adapting it. Assurance networks are thus resilient to unpredictable failure. Service applications to be executed in assurance networks must be available for both normal and disaster situations. It is because if victims cannot use the service applications well in normal situations, they cannot make substantial use of them in disaster situations. Therefore, we have been studying and developing dual-purpose systems, which are available in both normal and disaster situations. In these systems, service applications in normal situations must be smoothly switched to the corresponding service applications in disaster situations. As the service applications in normal situations, we have developed the assessment information acquisition and dissemination system based on delay and disruption tolerant MANETs for the Hiroshima national confectionery exposition [2] . Applying this system to the service application in disaster situations, short information such as safety and inquiry can be propagated through the delay and disruption tolerant MANETs. To illustrate feasibility of the service application in normal situations, which can be applied to disaster applications, demonstration on this system has been done in the MASS 2013 international symposium and the Japanese domestic technical meeting, AN, USN, and MoNA [3] .
We will show the related works as follows. In [4] , to connect multiple terminals by Bluetooth, a ring network configuration has been proposed and developed. In [5] , to communicate between wireless base station and terminals in disaster situations, an instant autonomous reborn network has been proposed and developed. This network is characterized by MANET with wireless LAN and delay and disruption tolerance. In [6] [7] , a wireless mesh network with wireless LAN access points and dual-purpose service applications on the network has been proposed and developed. Different from the above related works, we have been developing the dual-pur- pose systems, which are available in both normal and disastrous situations, and which are based on the assurance network design principle.
In this paper, we will propose a connectivity-dependent data propagation scheme, in which each terminal transfers data adaptively by wireless multi-hop data transfer or store-and-forward data transfer depending on whether the terminal has connections to its neighboring terminals. We also propose the dual-purpose system for both normal and disaster situations, and present design and implementation of its graphical user interface (GUI).
In the presented GUI, information in normal situations can be switched into information in disaster situations because their information corresponds with each other. Finally, we show two kinds of experimental results. To verify the resilience against disconnection among neighboring terminals, we show field experimental results on data propagation time. To validate feasibility of the dual-purpose normal and disaster situations system, we show experimental results on dissemination of assessment information and automatical switching of GUIs.
2. Bluetooth MANET
In the dual-purpose system in both normal and disaster situations, MANET is realized by Bluetooth [8] . We call such MANET as Bluetooth MANET [9] . Since Bluetooth is a connection oriented communication, terminals should establish their connection using the following procedures. As shown in Figure 1, each terminal detects the other terminals within the communication range, sends connection requests to the detected terminals, and the detected terminals accept the connection requests. Discovery state is a state where a terminal is currently detecting its neighboring state. Discoverable state is a state where a terminal is able to be detected. Discovery state is followed by discoverable state and these states are cyclically repeated.
Since each terminal moves around in MANET, terminals within the communication range vary. Therefore, in Bluetooth MANET each terminal periodically detects the other terminals within the communication range.
3. Connectivity-Dependent Data Propagation Scheme
3.1. Outline of Proposed Scheme
In MANET, due to movement of terminals, connectivity between terminals frequently varies. Since in real sys-
Figure 1. Sequence of connection establishment among terminals.
tems deployment of terminals are biased and places where terminals can move are restricted, density of terminals varies in places. In such situations, if Bluetooth for short distance communication is used for MANET, due to unbalanced density of terminals described above, disconnection between terminals through Bluetooth tends to occur more frequently than that through wireless LAN. In this paper, we propose a connectivity-dependent data propagation scheme as follows. When each terminal receives data packets from its neighboring terminal, if there is an established connection between the terminal and its neighboring terminal, the terminal sends the data packets through the connection using wireless multi-hop data transfer for MANET, and otherwise, the terminal stores the data in it and will send them in the future using the delay- and disruption-tolerant Epidemic Routing. In the Epidemic Routing, SV (Summary Vector) is periodically exchanged between neighboring terminals [10] .
In the proposed scheme, each terminal independently performs the following two procedures: the procedure for connection establishment between the terminal and its neighboring one and the procedure for transmission of data packets through established connections. These independent two procedures enable that even when the terminal has not established all connections between the terminal and its neighboring one, the terminal can send data packets to its neighboring terminals through some established connections. However, due to instability and interference of radio wave in real situations, there are some possibilities that established connections are suddenly disconnected even when neighboring terminals are within their mutual communication ranges. In such case, connections should be reestablished. In order to reestablish connections between neighboring terminals, even when each terminal receives data packets and does not have any connections to its neighboring terminals, in the proposed scheme, the terminal waits for a predetermined time and if the terminal can reestablish some connections to its neighboring terminals during the predetermined time, the terminal sends the data packets to its neighboring terminals.
Figure 2 represents the proposed scheme, which consists of independent two procedures: the procedure for connection establishment and the procedure for transmission of data packets. The list of neighboring terminals is updated by the former procedure and referred by the latter procedure. In the latter procedure, the buffer for data transfer, the content list and SV are used. Received data packets are stored in the buffer for a predetermined time and transmitted to neighboring terminals if connections to them are established or reestablished. Received data packets are registered to the content list. SVs are obtained by the content list and they are periodically transmitted to neighboring terminals to receive data packets from the neighboring terminals.
3.2. Algorithm of Proposed Scheme
1) Procedure for connection establishment: In order to discover neighboring terminals and establish connections to them, each terminal independently and periodically performs the following discover and establishment procedures.
i) Each terminal determines the period for discovery of neighboring terminals.
ii) The terminal initiates the discovery.
iii) When detecting neighboring terminals, the terminal adds them to the list of discovered neighboring terminals.
iv) After terminating the discovery, the terminal sends requests for connection to the neighboring terminals based on the list of discovered neighboring terminals.
v) The terminal waits until the next discovery. During the waiting time, the terminal can receive requests for connection from the neighboring terminals. If the requests for connection which the terminal sent are accepted by the neighboring terminals, terminals to which the connections are established are added to the list of neigh-
Figure 2. Overview of the proposed system.
boring terminals.
2) Procedure for transmission of data packets: When receiving data packets from neighboring terminals or generating data packets in the terminal, the terminal stores the data packets to the buffer for data transfer. After that, the terminal reads the TTL (Time To Live) fields in the data packets. TTL is decremented each time data packets are transferred as IP datagram. If the value of TTL is more than or equal to 1, the terminal transfers the data packets to the neighboring terminals through established connections according to the list of the neighboring terminals. At the same time, data packets are registered to the content list to be used for screen display of information in service applications such as word-of-mouth propagation [2] . In addition, data generation terminal ID and time stamp are derived from the data packets and registered to the stored data list called SV. If the same pair of such ID and time stamp was registered to SV, they are not registered to avoid their duplication.
When each terminal receives data packets, if there are the neighboring terminals in the list for data transfer, the terminal sends them to the neighboring terminals using wireless multi-hop data transfer. At the same time, the terminal registers the transferred data packets to the content list and SV. Based on them, the terminal transfers the stored data packets to neighboring terminals which are newly added to the list of neighboring terminals using the Epidemic Routing, which is a typical store-and-forward data transfer scheme. The stored data are maintained for a predetermined time.
3.3. Transfer of Stored Data Using Epidemic Routing
1) Epidemic routing with SV: SV is registered from the content list. Each terminal keeps SV for Epidemic Routing. Each terminal independently and periodically exchanges SV with neighboring terminals. Since IDs of data packets are only stored in SV, the overhead for exchanging SV is much smaller than that for exchanging data packets themselves.
Figure 3(a) denotes a time sequence chart representing that after exchange of SVS, data packets are transmitted. In the figure, we suppose that terminals S and A are neighboring terminals and have connections with each other and terminals S and B are also neighboring and have connections with each other. Terminal S broadcasts its own SV denoted by SVS to terminals A and B. Terminal A generates difference between IDs in SVA which terminal A keeps and IDs in SVS terminal A received. Based on the IDs, terminal A makes data packets, denoted by Data (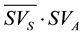 ), to which the IDs corresponds and unicasts them to terminal S. Similarly, terminal B makes data packets, denoted by Data (
), to which the IDs corresponds and unicasts them to terminal S. Similarly, terminal B makes data packets, denoted by Data (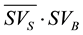 ), to which the IDs corresponds and unicasts them to terminal S. As described above, data packets are gradually propagated by periodically exchanging SVS and transmitting different data packets in Epidemic Routing.
), to which the IDs corresponds and unicasts them to terminal S. As described above, data packets are gradually propagated by periodically exchanging SVS and transmitting different data packets in Epidemic Routing.
2) Data transfer after epidemic routing: After Epidemic Routing is initiated, there are the following two schemes. (Scheme 1) After a terminal initiates Epidemic Routing, the terminal gives up the wireless multi-hop data transfer and continues Epidemic Routing. (Scheme 2) Even after a terminal initiates Epidemic Routing, the terminal takes precedence of wireless multi-hop data transfer over Epidemic Routing. In Scheme 2, if there are neighboring terminals to which the terminal has connections, the terminal transfers the data packets to the neighboring terminals until exchanging SV with the neighboring terminals. As shown in Figure 3(b), data packets Data (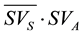 ) transmitted from terminal A is transferred to terminal B if connection between terminals S and B is established. Scheme 2 can reduce data propagation time because each terminal needs not wait for exchanging SVS between the terminal and its neighboring one. Scheme 1 is applied if TTL = 1 and Scheme 2 is
) transmitted from terminal A is transferred to terminal B if connection between terminals S and B is established. Scheme 2 can reduce data propagation time because each terminal needs not wait for exchanging SVS between the terminal and its neighboring one. Scheme 1 is applied if TTL = 1 and Scheme 2 is
Figure 3. Data transfer schemes using SV.
applied if TTL is greater than 1.
3.4. Wireless Multi-Hop Data Transfer by Reestablishment of Connections
This paper proposes the connectivity-dependent data propagation scheme called Scheme 2, in which Epidemic Routing and wireless multi-hop data transfer are switched depending on whether there are neighboring terminals between which connections are established. In MANET over Bluetooth, it takes some time to establish connection and the established connection is disconnected due to instability and interference of radio wave. To cope with this problem, Scheme 2 is extended as follows. In the extend scheme called Scheme 3, when each terminal receives data packets, if there are neighboring terminals between which connections are established, the terminal sends the data packets to the neighboring terminals using wireless multi-hop data transfer. As shown in Figure 3(c), even if there are not neighboring terminals, the terminal waits for a predetermined time which is shorter than the periodic time for exchanging SVS. If, during the predetermined time, the connections between the neighboring terminals are reestablished, the terminal sends the data packets to the neighboring ones using wireless multi-hop data transfer.
Figure 4 represents an example of Scheme 3. In the figure, when terminal 1 transfers data packets, we suppose that connection between terminals 2 and 4 is temporally disconnected. During the predetermined time for which terminal 2 waits, if connection between terminals 2 and 4 is reestablished, terminal 2 sends data packets to terminal 4. Otherwise, terminal 2 performs Epidemic Routing and tries to exchange SVS with terminal 4. Let the time for waiting for reestablishment of connections be TM, let the remaining time for exchanging SVs be TSV, let the time from disconnection to reestablishment of connection be TD, and let the time for propagation of data packets be TF. Using these symbols, we can say that in the case that TD ≤ TM, TF = TD because, after reestablishment, data packets can be immediately propagated through the reestablished connection, and in the case that TM < TD ≤ TSV, TF = TSV because data propagation must wait until exchange of SVs.
In the field experiments described later, the time for reestablishment, TM is set to 5 seconds, which is shorter than the periodic time for exchanging SVs, denoted by TSV, which is set to 6 seconds. In Section 3.3.2, Scheme 2 is introduced. Scheme 2 is regarded as Scheme 3 in which the time for reestablishment is set to be 0.
4. Dual-Purpose System in Normal and Disaster Situations
In this section, we propose the dual-purpose system for both normal and disaster situations. Service applications are installed in the application layer of the network architecture [11] based on Bluetooth MANET. The application layer consists of two modes for normal and disaster situations. We call them normal mode and disaster mode. The network architecture is depicted in Figure 5. This is a hierarchical structure composed with device, routing and application layers based on Android OS. The application layer consists of two modes for normal and disaster situations, however, the device and routing layers are common for both situations. Therefore, the mode in the application layer, to which packets should be delivered from the routing layer, is determined by mode information stored in the packets received in the routing layer.
Since service applications are designed based on the common network architecture, the schemes for propagating information in the network in two modes of the application layer are the same. Users can thus propagate information even in disasters situations as the same way as in normal situations. Since information which identify whether packets are propagated in normal situations or disaster situations is included in the packets, we design the dual-purpose systems so that, when user terminals receive packets identifying disaster situations, ser-
Figure 4. Prioritized use of wireless multi-hop data transfer in the proposed scheme.
Figure 5. Network architecture.
vices applications for normal mode are automatically switched into those for disaster mode. In order to avoid not to use the service application in disaster situations, the information structure for GUI and how to operate it in both normal and disaster situations are unified.
In the following, the details of each mode in the application layer, information propagation scheme and switching from normal mode to disaster mode will be explained.
4.1. Normal Mode
The normal mode in the dual-purpose system includes functions for word-of-mouth information propagation and children tracking. The function for word-of-mouth information propagation is to propagate word-of-mouth information using Bluetooth MANET and Epidemic Routing [10] as a routing technique for delay and disruption tolerance. The function for children tracking is to check safety of children by tracking location information and group information of terminals that children bring through Bluetooth MANET, wireless mesh network and mobile telephone network. Hereinafter, the details of functions for word-of-mouth information propagation and children tracking are described.
1) Word-of-mouth information propagation: The image of word-of-mouth information propagation is depicted in Figure 6. In Figure 6, suppose that a user evaluates a product in shop A. The user inputs his/her evaluation result to an Android terminal and starts to propagate it as word-of-mouth information. We say that two terminals are neighboring if they are within their communication range each other. The information is directly delivered to neighboring terminals and indirectly delivered to terminals along a sequence of neighboring terminals by multi-hop data transfer in a real-time way. Simultaneously, word-of-mouth information is stored in the memory of terminals. Even when there do not exist any sequence of neighboring terminals, if a terminal would move to another terminal and they would be within their communication range each other, the stored information could be delivered to the terminal. In this way, the word-of-mouth information is gradually propagated to the broad areas.
2) Children tracking: The intended persons of word-of-mouth information propagation are the general public, while those of children tracking are children who are registered in advance. The image of children tracking is represented in [12] . Each terminal, which a child has, obtains group information by broadcasting messages at constant intervals to nearby terminals through multi-hop data transfer in Bluetooth MANET. The group information obtained by Bluetooth MANET and the location information obtained by GPS are delivered to a server placed in, for example, schools. Parents of the children can access to the server through Internet and to check safety of the children by the information on group and location.
The property of group information and location information for children tracking is different from that of word-of-mouth information. The more the group and location information is fresh, the more its reliability for safety increases. The information which has passed for a given constant time from its generation is unnecessary and such old information stored in terminals is discarded.
4.2. Disaster Mode
The disaster mode in the dual-purpose system includes functions for safety information propagation and prioritized information on relatives in disaster situations. We expect public communication infrastructure such as mo-
Figure 6. Image of word-of-mouth information propagation.
bile telephone networks and wireless mesh networks would be damaged and become unavailable in serious disaster situations. In such situations, we should make use of delay and disruption tolerant MANET. In the presented network architecture, we use Bluetooth MANET and Epidemic Routing for propagation of safety information and information on relatives. After recovery of the damaged public communication infrastructure, safety information can be delivered to distant places by connecting MANET and the recovered infrastructure. Hereinafter, the details of the functions for propagation of safety information and the prioritized information on relatives in disaster situations are described.
1) Safety information propagation: Figure 7 models the network configuration in disaster situations, to which the dual-purpose system should be applied. In Figure 7, when disasters happen, victims are sparsely distributed in areas which are far from the predetermined emergency evacuation areas and they move to the emergency evacuation areas where access points exist. As a result, many victims stay in the emergency evacuation areas. In these areas, the density of victims becomes large and mobility of victims becomes small. On the other hand, the density of areas which are far from emergency evacuation areas becomes small and the mobility of victims becomes large.
In this way, the density and mobility of victims in the overall areas are dynamically changed. The dual-pur- pose system in normal and disaster situations must cope with the dynamical change of density and mobility. During movement of victims, Epidemic routing should be utilized because the density of areas where victims move is small. In the emergency evacuation areas, information is delivered by multi-hop data transfer in Bluetooth MANET. Safety information is therefore propagated by the delay and disruption tolerant Bluetooth MANET in the dual-purpose system.
After recovery of the damaged network infrastructure such as the public telephone network and the wireless mesh network, safety information is propagated to these networks through recovered access points.
2) Prioritized information on relatives: As same as children tracking, the intended persons are relatives who are registered in advance to terminals. The volume of safety information delivered and stored in terminals becomes very large in disaster situations. Safety information on relatives is prioritized on its display and storage in terminals. Concretely speaking, whenever safety information on relatives is received in terminals, it is displayed
Figure 7. Disaster situations for dual-purpose system.
in priority to the other information and always stored in terminals. In case that the storage capacity is full, the other information except for information on relatives is discarded from the storage in terminals.
4.3. Switching of Modes
The switching from normal mode to disaster mode has the following two policies.
・ Manual switching by operation of users;
・ Automatic switching by receiving packets of the disaster mode.
Manual switching from normal mode to disaster mode is performed by pushing the button on the screen of terminals in normal mode. As explained before, packets include an identity of normal mode or disaster mode. Automatic switching is performed by recognizing an identity of disaster mode in receiving packets. Along with propagation of safety information, terminals with disaster mode increase. Automatic switching against users' intention can be prevented by adding users' acceptance before automatic switching. Switching from disaster mode to normal mode is manually performed.
5. Design and Implementation of GUI
In this section, we describe GUI design and implementation of Android applications for the dual-purpose system in both normal and disaster situations. In general, it is difficult to use applications for disaster situations because we do not use them in normal situations. To cope with this problem, we have developed applications for both normal and disaster situations such that, when disasters happen, applications for normal disasters are switched to those for disaster applications and that victims can use applications for disaster situations as those for normal situations. In the developed applications, as described in Section 4, information propagation schemes in both normal and disaster situations are unified in the common network architecture and information structure in GUI for disaster situations is the same as that for normal situations. In other words, information elements for disaster situations have one-to-one correspondence to those for normal situations. In the following subsections, we will explain the details of fundamental screen for normal and disaster modes and correspondence of information in the screen between both modes.
5.1. Fundamental Screen
The correspondence between applications in both modes is represented in [12] . In the fundamental screen of applications in normal mode, entries for four applications are depicted. The first application is to propagate word- of-mouth information in a field, which is recognized as time sequence of word-of-mouth information. The second application is to notify participants in the event site of event information generated by event organizers and shops. The third application is to inquire about lost things. The fourth application is to track children in school districts. On the other hand, in the fundamental screen of applications in disaster mode, entries for four applications, which correspond to four applications in normal mode, are also depicted. The first application is to propagate safety information in disaster areas, which is recognized as time sequence of safety information. The second application is to notify victims in disaster areas of emergency information generated by local governments and manager of emergency evacuation areas. The third application is to inquire about emergency problems.
The fourth application is to collect safety information on relatives. These applications in normal mode and disaster mode are selected by tabs. In the following, correspondence between information on the screen displayed by the above applications for normal and disaster modes.
1) Word-of-mouth and safety information: Figure 8(a) represents image capture of word-of-mouth information on the screen. Information sent by the user is displayed in the left and information received by the user is displayed in the right. Figure 8(b) and Figure 8(c) represent two screens transferred from the screen in Figure 8(a). Figure 8(b) is transferred by pushing the button which shows entry for generating word-of-mouth information. Figure 8(c) is transferred by pushing the button which shows entry for selecting an avatar representing the user. In the screen of Figure 8(b), word-of-mouth information is made by selecting an item from the preset items and freely describing comments in the box. Pictures taken by the terminal’s camera can be attached as word-of-mouth information. In the screen of Figure 8(c), avatars prepared in advance are displayed and the user can select one of them as his/her agency. The avatar selected in this screen appears in Figure 8(a) as his/her
Figure 8. Design of screen and interface.
agency of the user who sends word-of-mouth information. The source user of word-of-mouth information is identified by the avatar. Figure 8(d) represents image capture of safety information on the screen. The information structure in Figure 8(d) is the same as that in Figure 8(a). In the screen transferred from Figure 8(d) by pushing the button which shows entry for generating safety information, safety information is made in the same way as word-of-mouth information.
2) Notification information: The information structure for notification of event information in normal mode is the same as that for notification of emergency information in disaster mode. Information displayed on the screens in both modes is corresponding with each other. However, the object persons who notify such information are different. Event organizers and shops notify participants in the event site of event information, while local governments and manager of emergency evacuation areas notify victims in disaster areas of emergency information. The notification information in both modes is described in a free format. In order to prevent spoofing when the user enters the notification screen from the fundamental screen, authentication by password is imposed.
3) Inquiry information: The information structure for inquiry about lost things in normal mode is the same as that for inquiry about emergency problems in disaster mode. Information displayed on the screens in both modes is corresponding with each other. By pushing a button in the bottom of the fundamental screen, the user can transfer to the inquiry screen. In the inquiry screen, the user selects the category for inquiry and makes the inquiry with the user name in a free format. The user name is omitted if the user name is inputted when inquiry application is triggered.
4) Children tracking and prioritized information on relatives: The information structure for children tracking in normal mode is the same as that for collection of safety information on relatives in disaster mode. Information displayed on the screens in both modes is corresponding with each other. In children tracking, information on children tracking is periodically transmitted and propagated among the terminals registered for children tracking. In collection of safety information on relatives, information on relatives received by registered terminals is prioritized to be displayed on the screen and stored in the memory. In both applications, it is unnecessary to make information in any terminals. The function of children tracking is activated by pushing the button for children tracking in the screen and information for children tracking is automatically transmitted by the activated terminals. Terminals of relatives are selected by pushing the button in the screen where terminals are displayed.
5.2. Correspondence between Inputted and Registered Items for Making Information
Propagated messages are made by inputting information to each item in the screen. Information on users and prioritized information on relatives are registered to applications. The screens for inputting and registering information are represented in Figure 8(f). By registering information on users and relatives, source users can be added to messages and information on relatives can be identified from the received messages. Table 1 repre- sents correspondence between inputted and registered items for information of word-of-mouth, children tracking and safety. To smoothly transfer from normal mode to disaster mode, we have correspondence between each item for input and registration in normal mode and disaster mode. The details are described in the following.
1) Assessment Information: Assessment information is manually made by selecting items and performing free description for word-of-mouth and safety information propagation, while assessment information is automati-
Table 1. Correspondence between inputted and registrated items.
cally generated by the system for children tracking. The screen for making assessment information in disaster mode is represented in Figure 8(e), which corresponds to that in normal mode represented in Figure 8(b). In word-of-mouth information, overall evaluation on products is given by five-star scale. For products which are specified by area, shop and name, comments are described. In safety information, health evaluation on the user is also given by five-star scale as corresponds to overall evaluation on products. Subsequently, disaster area, emergency evacuation area and injury status are selected from items and comments on relatives are described. In children tracking, location information corresponding to area information the user makes is automatically obtained by GPS and it is propagated to the other terminals which is reachable by delay and disruption tolerant MANET.
2) System detection information: Input of information is classified into input by the user and input by the dual-purpose system in normal and disaster situations. Input of information by the system is to derive information for propagation from information detected by the system. Information detected by the system is time instances for generation and transmission of information and group information obtained by MANET. Since propagation of word-of-mouth information needs not real time property, time instances for generation and transmission of information are recorded as log information. Since children tracking needs real time property, time instances for transmission of children information is used as the criteria for discarding old and unuseful information. Group information detected by the system is recognized as a group of the current terminals which is reachable from the user terminal. Since propagation of safety information needs real time property and a group of nearby terminals is the same as in children tracking, time instances for transmission of safety information are used as the criteria for discarding old and unuseful information and group information is used for recognizing a group of victims.
3) User information: In the dual-purpose system, user information and its identity can be registered to applications. They are commonly used for both normal and disaster situations. Accordingly, user information can be added to assessment information for word-of-mouth propagation in normal mode and children who are registered as user information can be recognized when terminals of children forms delay and disruption tolerant MANET. In disaster mode, addition of user information to safety information becomes possible in the same way as word-of-mouth information and safety information with user information is recognized as prioritized information on relatives, which is propagated through delay and disruption tolerant MANET.
4) Information on relatives: By registering user information and its identity in terminals as information on relatives, information on relatives transmitted can be received as information on relatives. The registered information on relatives are commonly used for both normal and disaster situations. In normal mode, information which is transmitted by children's terminals can be received. In disaster mode, safety information on relatives can be prioritized when receiving it.
6. Experiments on Resilience against Disconnection
This section shows experimental results on resilience against disconnection. The data propagation time including connection establishment or reestablishment time for the following three data transfer schemes is measured in the experiments. Scheme 1 is as follows. After Epidemic Routing is initiated, each terminal periodically exchanges SV with the neighboring terminals. The neighboring terminals which received the SVs return difference of data packets to the terminal which sent the SVs. This is explained in Section 3.3.1. Scheme 2 is as follows. Each terminal independently and periodically switches wireless multi-hop data transfer or Epidemic Routing depending on connectivity to the neighboring terminals. This scheme is explained in Section3.3.2. Scheme 3 is as follows. In addition to Scheme 2, even when there are no connections to the neighboring terminals, each terminal waits for a predetermined time and during that time if the terminal reestablishes connections to the neighboring ones, the terminal sends the data packets to the neighboring terminals using wireless multi-hop data transfer. The propagation time of the above three schemes are compared.
Table 2 shows the parameters used for system implementation. The time for discovery is the time period during which each terminal discovers its neighboring terminals, and the periodic time for discovery is the periodic time during which each terminal discovers its neighboring terminals. In the table, the time for discovery is 3 seconds, and after a random time selected from 7 to 10 seconds, discovery is initiated. The waiting time for re- establishment of connection is 5 seconds. During that waiting time, each terminal stores data packets in the buffer for data transfer. During that waiting time, as soon as each terminal reestablishes connections to its neighboring terminals, the terminal sends the stored data packets using wireless multi-hop data transfer.
6.1. Environments for Field Experiments
Two kinds of terminals are used for experiments. The specifications for these terminals are shown in Table 3. The place for the field experiments are Hiroshima City University. In this place, there exist the same radio frequencies 2.4 GHz for Bluetooth, IEEE 802.11 g/n, and so on.
6.2. Procedures for Field Experiments
As shown in Figure 9, five terminals A to E are deployed on a straight line and each terminal has two terminals in the communication range except for two end terminals A and E. Terminal B discovers two terminals A and C as its neighboring terminals and establishes connections to them. In a similar way, terminal D discovers two terminals C and E as its neighboring terminals and establishes connections to them. After establishment of these connections, they are randomly disconnected. These procedures are repeated. These disconnections simulate either disconnections by node movement or disconnections by instability and interference of radio waves.
In the above dynamical environments caused by periodic establishment of connections and random disconnections, terminal A transmits data packets to terminal E through terminals B, C, and D. Let the size of data packets be 50 bytes and the content of data packets be simple text data. The propagation times from terminal A to terminal E are measured for the following schemes, Scheme 1, Scheme 2 and Scheme 3.
Table 2. Parameter values for implementation.
Table 3. The specifications of implemented terminals.
Figure 9. Example of the topology changing.
i) Scheme 1) Since the Epidemic Routing is initiated, SVs are periodically exchanged and only after that, data packets are transmitted.
ii) Scheme 2) In addition to Scheme 1, even when receiving data packets, if each terminal establishes connections to its neighboring terminal, the terminal sends the data packets to its neighboring ones by wireless multi-hop data transfer.
iii) Scheme 3) In addition to Scheme 2, even when receiving data packets, if each terminal does not establish any connections to its neighboring terminal, the terminal stores the data packets and waits for a predetermined time. During the predetermined time, if the terminal can reestablish some connections to its neighboring terminals, it sends the data packets to its neighboring ones by wireless multi-hop data transfer.
6.3. Experimental Results
The data propagation time for three schemes is measured 200 times. The average and 95% confidence interval are calculated from the measured data. Figure 10 shows the experimental results. The propagation time of Scheme 2 is 10 seconds shorter than that of Scheme 1 and the propagation time of Scheme 3 is 18 seconds shorter than that of Scheme 1. It is because, to transfer data packets, Scheme 2 and Scheme 3 need not to wait until the time for exchanging SVS.
The maximum propagation time was 200 seconds and the minimum propagation time was less than 1 minute. The route on which data packets are transferred is single in the experimental environment. The case of the maximum propagation time indicates the worst timing by which disconnection occurs between neighboring terminals and reestablishment of connections frequently occurs. The case of the minimum propagation time indicates the best timing by which data packets are transferred only using wireless multi-hop data transfer.
7. Experiments for Validation of Feasibility
In this section, we show experiments on feasibility of automatically switching from normal mode to disaster mode. In the experiments, after mode switching of a terminal by the user, safety information is propagated and the mode of nearby terminals which received the propagated information is automatically switched.
7.1. Experimental Environments
As shown in Table 4, two kinds of Android terminals are used in the experiments. The experiments places are inside the building of Hiroshima City University, in which there are the same radio frequencies as Bluetooth such as 2.4 GHz IEEE802.11 g/n in the experimental environments.
7.2. Experiments
Automatic mode transfer can be performed by receiving safety information through multi-hop data transfer and store-and-forward data transfer. To do that in experiments, terminals which are within their communication range are placed in advance and one of them is triggered later for store-and-forward data transfer. The image of the experiments is represented in Figure 11. In the figure, terminals A and B are triggered as normal mode, which are connected with each other over Bluetooth. The mode of terminal A is switched to disaster mode and safety information is transmitted by terminal A. After the safety information is propagated to terminal B, terminal A is stopped and terminal C is triggered.
7.3. Experimental Results
Figure 12 represents captures of screens of terminals. The mode of terminal A is manually switched by operation of the user. After switching, safety information is transmitted by terminal A. Since terminals A and B are
Figure 10. The result of data propagation time in each scheme.
Figure 11. Experiments for mode switching.
Figure 12. Display on screen of terminals.
Table 4. The specifications of Android terminals.
within the communication range with each other, safety information is propagated in real-time. As shown in Figure 12, in the screen of terminal B which received safety information from terminal A, dialog which shows reception of safety information is displayed and transfer to disaster mode is required to switch to disaster mode. Terminal C is triggered later. After completing connection between terminals B and C, safety information stored in terminal B is forwarded to terminal C. The mode of terminal C is switched when receiving the forwarded safety information. Requirement for switching to disaster mode is displayed on the screen of terminal C as the same as in terminal B.
8. Conclusions
This paper has proposed a connectivity-dependent data propagation scheme. In the proposed scheme, depending on whether, when receiving data packets, each terminal establishes connections to its neighboring terminals, the terminal switches either wireless multi-hop data transfer or epidemic routing. This scheme is extended so that even when each terminal does not establish any connections to its neighboring terminals, if the terminal can reestablish some connections to its neighboring ones for a predetermined time, the terminal sends the data packets using wireless multi-hop data transfer. The proposed and extended schemes make effective use of wireless multi-hop data transfer than epidemic routing. The proposed and extended schemes are evaluated by field experiments in which disconnections among neighboring terminals randomly occur. The experimental results show that data packets by the proposed and extended schemes can be propagated in a shorter time. We can say that the proposed and extended schemes are resilient against disconnections.
This paper has also proposed the dual-purpose system for both normal and disaster situations and presented design and implementation of its graphical user interface (GUI). Two modes for normal and disaster situations are installed in the presented system. Service applications for normal situations can be smoothly switched to those for disaster situations because of the common data transfer scheme in the network architecture and the correspondence of information structure in normal and disaster modes for GUI. Through experiments for validation of feasibility of the presented system, we have confirmed propagation of safety information and manual and automatical mode switching by both multi-hop data transfer and store-and-forward data transfer. In the future, we will evaluate performance of the presented system by extensive field experiments and increase usability of the graphical user interface.
Acknowledgements
This research is supported by JSPS KAKENHI (Grant-in-Aid for Scientific Research (B), No. 24300028, (C), No. 25330109)) and MIC Strategic Information and Communications R&D Promotion Programme (ICT Innovation Creation R&D, No. 131408006).
Cite this paper
YuyaMinami,YuyaKitaura,YuriTsutsui,EitaroKohno,ShinjiInoue,TomoyukiOhta,YoshiakiKakuda, (2015) Implementation and Evaluation of Dual-Purpose Normal and Disaster Situations System Based on Delay and Disruption Tolerant Bluetooth MANETs. International Journal of Communications, Network and System Sciences,08,342-357. doi: 10.4236/ijcns.2015.89033
References
- 1. Kakuda, Y., Ohta, T. and Malek, M. (2013) Self-Organizing Real-Time Services in Mobile Ad Hoc Networks. Self- Organization in Embedded Real-Time Systems, Springer, Berlin, 55-54.
http://dx.doi.org/10.1007/978-1-4614-1969-3_3 - 2. Kitaura, Y., Tsutsui, Y., Taketa, K., Kohno, E., Inoue, S., Ohta, T. and Kakuda, Y. (2013) The Assessment Information Acquisition and Dissemination System Based on Delay and Disruption Tolerant MANETs for the Hiroshima National Confectionery Exposition. Proceedings of First Inter-national Symposium on Computing and Networking (CANDAR’13), 6th International Workshop on Autonomous Self-Organizing Network (ASON’13), Ehime, December 2013, 476-479.
http://dx.doi.org/10.1109/CANDAR.2013.84 - 3. Morii, K., Taketa, K., Taoda, Y., Kenji, Y., Tsutsui, Y., Kitaura, Y., Kohno, E., Inoue, S., Ohta, T. and Kakuda, Y. (2013) [Technology Exhibit] The Assessment Information Acquisition and Dissemination System Based on Delay and Disruption Tolerant Mobile Ad Hoc Networks for the Hiroshima National Confectionary Exposition. Technical Report of IEICE MoNA 2012-59, AN2012-61, USN2012-70, 89-93.
- 4. Hasegawa, S., Date, M., Ueno, H., Nakae, T., Abe, T. and Miyashita, N. (2013) Multi-Cluster Based Mobile ad Hoc Networks over Bluetooth. Proc. IEICE Society Conf. '13, Fukuoka, September 2013, 447.
- 5. Nishiyama, H. and Kato, N. (2013) Mobile Device-Driven Self-Directive Network for Message Delivery in Disaster Area. Proc. IEICE Gen. Conf. '13, Gifu, March 2013, 28-29.
- 6. Miura, R., Inoue, M., Hamaguchi, K., Owada, Y., Takizawa, K., Ono, F. and Suzuki, M. (2013) Disaster-Resilient Wireless Mesh Network Test-Bed. Technical Report of IEICE, 69-74.
- 7. Owada, Y., Inoue, M., Miura, R., Hamaguchi, K. and Harai, H. (2013) [Technology Exhibit] A Demonstration of Applications Using In-Network Information Caching and Distributing Platform of NerveNet in Case of Ordinary/Disaster Situation. Technical Report of IEICE, 91-93.
- 8. Bluetooth SIG (2007) Specifications of the Bluetooth System v2.1 EDR.
https://www.bluetooth.org/docman/handlers/downloaddoc.ashx?doc_id=241363 - 9. Taketa, K. and Kakuda, Y. (2013) A Method for Effective Discovery and Connection in Bluetooth MANET Consisting of Android Terminals. Proceedings of 8th International Conference on Broadband Communications and Biomedical Applications (IB2COM 2013), Guilin, December 2013, 78-83.
- 10. Vahdat, A., Becker, D., et al. (2000) Epidemic Routing for Partially Connected Ad Hoc Networks. Technical Report CS-200006, Duke University.
- 11. Morii, K., Taketa, K. and Kakuda, Y. (2012) Construction of Network Architecture Based on Bluetooth MANET and Its Applications. The 14th IEEE Hiroshima Section Student Symposium, Okayama, Nov-ember 2012, 179-182.
- 12. Minami, Y., Kitaura, Y., Tsutsui, Y., Kohno, E., Inoue, S., Ohta, T. and Kakuda, Y. (2014) Design and Implementation of Dual-Purpose Normal and Disaster Situations Systems Based on Delay and Dis-ruption Tolerant Bluetooth MANETs. Proceedings of 20th IEEE Asia-Pacific Conference on Commun-ications (APCC2014), Pattaya, 2014, 9-14.
NOTES
*Corresponding authors.















