International Journal of Internet and Distributed Systems
Vol.1 No.3(2013), Article ID:31351,7 pages DOI:10.4236/ijids.2013.13004
The Internet-EDI Systems Adoption by Enterprises in Jordan: Descriptive Analysis of Adoption, Strategies and Benefits
![]()
Department of Management and Marketing, College of Business and Economics (CBE), Qatar University, Doha, Qatar
Email: anasbakri@qu.edu.qa
Copyright © 2013 Anas Al Bakri. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Received April 27, 2013; revised May 28, 2013; accepted June 8, 2013
Keywords: Internet-EDI; Technology Adoption; I-EDI Strategies
ABSTRACT
This paper reviewed and explored the current extent of the Internet Electronic Data Interchange systems adoption in Jordan particularly in the SME sector. Also the paper presented the benefits of IEDI adoption and showed the main obstacles facing the SME in Jordan to adopt. This paper used the descriptive and theoretical analysis approaches for collecting and analysis the historical and archived data. The literature showed that Jordan, as a developing country, has achieved forward steps in introducing the Internet to the different sectors of life. The adoption of the electronic tools in business became a governmental target in recent years to make it possible for SMEs to be able to continue to achieve success in their business [1]. Most of Jordanian SMEs have little or no competitive pressure to use I-EDI systems, since most suppliers, customers and other competitors do not seem to promote I-EDI systems. The study concluded that SMEs in Jordan could grow and become larger companies, and supporting national economy. Thus it is very important to develop and grow Jordanian SMEs by doing more research.
1. Introduction
Today, information sharing is critical to almost every enterprise. Also the open flow of information gives consumers real choice in conducting their daily affairs [2]. In addition, reference [3,4] asserted that information technology has also radically altered the management of supply chain operations, many business partners who are adjacent on the supply chain can gain from entering inter-organizational information sharing relationships and sharing information that was previously accessible to only one of them. Therefore, information sharing systems allow businesses to determine TPs needs accurately and meet those needs efficiently and permit TPs to be informed rapidly and at low cost of those opportunities in which they are most likely to be interested [5]. Hence, responsible sharing of personal information enhances the productivity of the enterprise’s economy and generates significant benefits for its TPs [6]. In addition, reference [6] mentioned that typically, the development of interorganizational information systems and the sharing of information are mainly targeted at increasing operational efficiency by reducing ordering costs, inventory costs and supply lead times. Many studies have been focusing on studying the information sharing technology issues and estimating the value generated from these arrangements using traditional models of inventory and ordering costs. For example, reference [5,7] mentioned that through information sharing, the ready availability of personal information facilitates a vibrant economy, improves efficiency, reduces costs, creates jobs and provides valuable products and services that people desire within an enterprise. The key goals of information security are to protect the confidentiality, integrity and availability of information. Information security is concerned with the confidentiality, integrity and availability of data regardless of the form the data may take [3]. Hence, all forms of information security in an enterprise are driven by “business” needs. This means that security must reflect the enterprise perspective and contribute to rather than hinder the enterprise goals and objectives [8]. All this makes information security a governance and management issue [9]. In addition, the primary business benefit of information security in enterprise is avoiding loss through security failures. These losses usually have an economic dimension, either directly or indirectly. However, good security management presents opportunities for other benefits such as improving operational and administrative efficiency and effectiveness [10]. Nevertheless, without information security, the fortunes of the new economy so dependent on information may be short lived. Furthermore, it is the role of information security to provide the basic requirements to successfully integrate security into IT in a manner that properly addresses real threats. While the goal of information security is to ensure the confidentiality, integrity, and availability of information, the role of information security is essential for the protection of consumers, businesses and governments from the threats caused by the natural advancement of IT [1]. Information security poses considerable risks to information sharing such as B2B systems that are connected through networks. Information security can also result in the systems and the networks running randomly cause loss of information, and information to be corrupted, with the associated loss of productivity and operation efficiency of the enterprise [9]. Cybercrime can be defined as all the criminal offences that are committed with the aid of communication devices in a network such as the Internet, the telephone line or the mobile network [11]. Such acts commonly include unauthorized access to computer files and/or theft of proprietary information, disruption of information housed in a remote computer with viruses, Trojans, worms, logic bombs and denial of service (DOS) attacks, selling illegal objects and substances over Internet, and the theft and forgery of identity [9]. Like retailers and service providers, most websites that produce income could stand to lose money in the event of downtime created by cyber criminals.
As Internet-businesses have increased economic importance to many countries, cybercrime has also become more political and therefore “terror” related [12]. Less common crimes are more institutionally targeted, such as organized assaults on a nation’s network infrastructure; the hacking of government, commercial, or non-profit websites; or attacks on critical infrastructure [11]. On the other hand, the costs that are affected by the cyber-attacks can be extremely high for an organization and the effects of cybercrime can also be felt far from the place where the crime is committed. It can also greatly weaken countries’ economy, thereby stripping it of its resources and to an extent making it more vulnerable to military attack. Cyber terror can also affect many Internet-based businesses.
2. Definition of Information Sharing and Security
Today, information sharing is critical to almost every organization. Also the open flow of information gives consumers real choice in conducting their daily affairs [2]. In addition, reference [3] asserted that information technology has also radically altered the management of supply chain operations, many business partners who are adjacent on the supply chain can gain from entering inter-organizational information sharing relationships and sharing information that was previously accessible to only one of them. Therefore, Information-sharing practically B2B systems allow businesses to determine trading partners needs accurately and meet those needs efficiently and permits trading partners and suppliers to be informed rapidly and at low cost of those opportunities in which they are most likely to be interested. Hence, responsible sharing of personal information enhances the productivity of the enterprise’s economy and generates significant benefits for its suppliers and partners. In addition, reference [6] said typically, the development of inter-organizational information systems and the sharing of information are mainly targeted at increasing operational efficiency by reducing ordering costs, inventory costs and supply lead times. Many studies have focused on studying the information sharing technology issues and estimating the value generated from these arrangements using traditional models of inventory and ordering costs. Further, reference [7] mentioned which, through information sharing the ready availability of personal information facilitates a vibrant economy, improves efficiency, reduces costs, creates jobs, and provides valuable products and services that people want within an organization. The key goals of information security are to protect the confidentiality, integrity and availability of information. Information security is concerned with the confidentiality, integrity and availability of data regardless of the form the data may take. All forms of information security in an enterprise are driven by ‘business’ needs. This means that security must reflect the ‘business’ perspective and contribute to and not hinder ‘business’ goals and objectives. All this makes information security a governance and management issue [9]. In addition, the primary business benefit of information security in enterprise is avoiding loss through security failures. These losses usually have an economic dimension, either directly or indirectly. However, good security management presents opportunities for other benefits such as improved operational and administrative efficiency and effectiveness [10]. Nevertheless, without information security, the fate of the new economy so dependent on information may be short lived. Furthermore, it is the role of Information Security to provide the basic requirements to successfully integrate security into IT in a manner that properly addresses real threats. While the goal of information security to ensure the confidentiality, integrity, and availability of information, the role of information security is essential for the protection of consumers, businesses and governments, from the threats caused by the natural advancement of IT. Information security poses considerable risks to information sharing such as B2B systems that are connected through networks. They can also result in the systems and the networks to run randomly, cause loss of information, and information to be become corrupted, with the significant loss of productivity and operation efficiency for the enterprise [9]. Cybercrime can be defined as the all the criminal offences that are committed with the aid of communication devices in a network such as Internet, the telephone line or the mobile network [11]. Such acts commonly include unauthorized access to computer files and/or theft of proprietary information, disruption of information housed in a remote computer with viruses, Trojans, worms, logic bombs and denial of service (DOS) attacks, selling illegal objects and substances over Internet, and the theft and forgery of identity [9] Like retailers and service providers, most websites that produce income could stand to lose money in the event of downtime created by cyber criminals. As internet-businesses have increasing economic importance to many countries, cybercrime has also become more political and therefore “terror” related [12]. Less common crimes are more institutionally targeted, such as organized assaults on a nation’s network infrastructure; the hacking of government, commercial, or non-profit web-sites; or attacks on critical infrastructure [11]. On the other hand, the costs that are affected by the cyber-attacks can be extremely high for an organization and the effects of cybercrime can also be felt far from the place where the crime is committed. It can also weaken countries’ economy greatly, thereby stripping it of its resources and to an extent where by making it more vulnerable to military attack. Cyber terror can also affect many internet-based businesses.
3. Internet Electronic Data Interchange (I-EDI) Systems
The Internet Electronic Data Interchange (I-EDI) systems are defined as a direct computer-to-computer communication between enterprises and their TPs. Exchange information of business documents, data and information and structured format that permit data to be processed by the receiver without re-keying [1]. I-EDI system is an illustration of an early adoption of computer networking [1]. I-EDI systems have become a key element of corporate strategies to create value by providing closer linkages among enterprises and TPs [13]. I-EDI systems allow enterprise’s computers to perform electronic transactions such as purchase orders and invoices without human intervention [1]. I-EDI systems were popular among large enterprises because it saved money that otherwise would be spent on processing paper and re-keying data. The continuously accelerated level of I-EDI system proliferation in recent years has prompted a growing number of researchers to examine some of the emerging issues surrounding the adoption, implementation, and diffusion of I-EDI systems. I-EDI systems have become a fundamental part of information management in many organizations over the world. I-EDI systems represent a new way of thinking about an old business function. It is the belief in the ability to modernize and streamline business practices [1]. The complexities of I-EDI systems are centered on the definition of the TPs relationships and the data integration with supporting business application systems. I-EDI systems also provide businesses with the ability to exchange business documents easily between trading partners without the laborious, time consuming, error prone movement and handling of paper [1].
3.1. Benefits of I-EDI Systems
The benefits are I-EDI systems both direct and indirect in nature. Direct benefits include operational cost savings and other internal efficiencies arising from, for example, reduced paperwork, reduced data re-entry, and reduced error rates. Likewise, indirect benefits are opportunities that emerge from the use of I-EDI systems, such as improved customer services and the potential for process reengineering [1]. At the same time, benefits are distinguished into operational benefits and strategic benefits. Operational benefits are related to the internal efficiency of an organization and include reduction of transaction errors, improvement in data accuracy, decreased transaction costs, and faster application processes. Strategic benefits should contribute to tactical and competitive advantages and are related to the impact of I-EDI systems on business processes and business relationships [1]. The following shows some of I-EDI systems benefits:
1) EDI systems improve operational performance in terms of operation efficiency, cost saving and inventory control [1].
2) EDI systems improve performance of Supply Chain Management (SCM): Shared and exchange information between supply chains partners can only be fully leveraged through process integration. The main objective of SCM is to integrate all key business activities through the improved relationships at all levels of the supply chain including internal operation, supplier’s networks and distribution channels [14].
3) EDI systems help to maintain a better relationship with TPs. This improves supplier-enterprise relationships and creates a competitive advantage.
3.2. Practice and Strategies of I-EDI Systems
In theory, I-EDI systems allow all vendors and their customers such as TP to link their computing infrastructures without worrying about the differences in their respective enterprises and systems. However, in practice, I-EDI systems have been difficult to use efficiently or inexpensively in developing countries particularly in SMEs [1]. The core purpose of I-EDI systems in B2B systems transactions is to transport business documents via electronic means in a format that is reusable throughout the entire organization and beyond [1]. The degree of effectiveness of the I-EDI systems operation itself, as well as the internal management information available from its use, will certainly be greater if application systems are up-to-date and efficient. Reverences [1,15,16] divided I-EDI system adoption strategies into three categories:
1) Strategies not requiring third party involvement using additional front-end software. In these strategies, data exchange is dependent on the front-end software used by TPs.
2) Strategies requiring third party involvement without using additional front-end software. The third party in this strategy may be a value added network (VAN) wanting to establish a web presence.
3) Strategies requiring third party involvement using additional front-end software. In this strategy, TPs also require additional front-end-formatting software provided by the third party (I-VANS).
4. SMEs in Jordan
Most of the SMEs in Jordan are run as family enterprises [17,18]. Jordanian SMEs are mainly directed to making small types of goods rather than having a strong industrial capacity in local, regional, and global markets. This eventually impedes these enterprises to expand the scope of their products and services to local and global markets. In Jordan, Department of Statistics (DOS) classifies an enterprise with less than five employees as a small enterprise, while those with 5 to 19 employees are classified as medium enterprises [18,19]. The following
Table 1 provides the economic sectors in Jordan and their contributions to GDP.
Table 2 shows the number of registered enterprises in Jordan by economic sectors.
There are many international consultative institutions such as European-Jordanian Action for the Development of Enterprises (EJADA) and the US Agency for International Development (USAID), which are familiar with
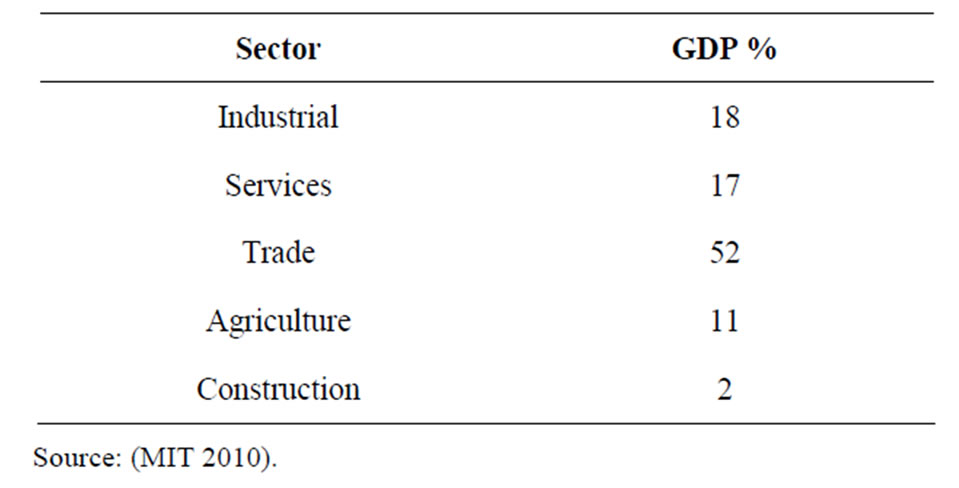
Table 1. The Economic sectors in Jordan and their contributions to GDP.
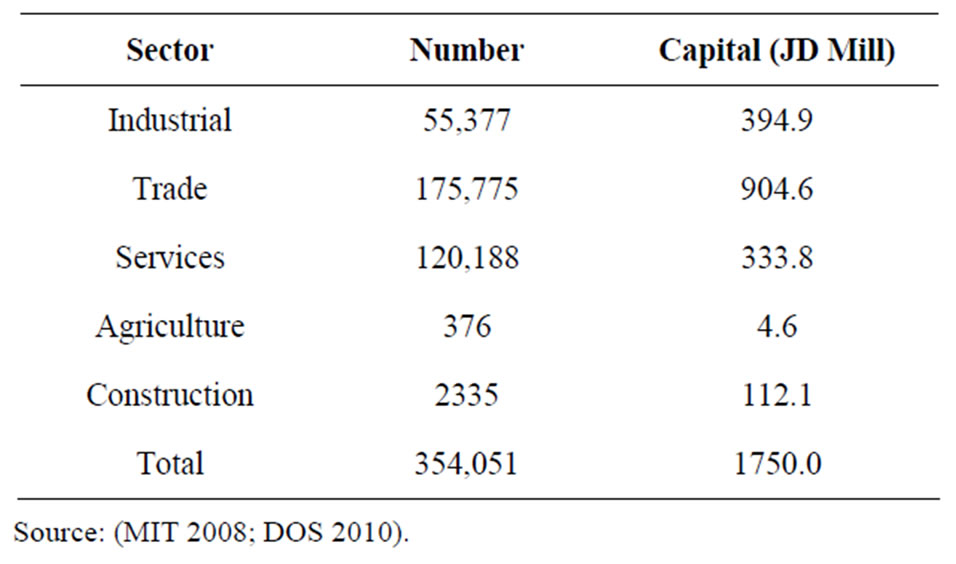
Table 2. Number of registered enterprises in Jordan according to economic sectors.
SMEs in Jordan and provide them with technical and financial support [18,19]. Jordan free trade agreements with Europe and United States would be the most challenging reasons for SMEs in Jordan. JADA’s main objective is to upgrade the capacity building of all SMEs in Jordan to make them more effective on the local scene [20]. Therefore, EJADA introduces better chances for the Jordanian SMEs to set their feet in the European markets and be at a competing level with their Europe markets. Also filter the existing SMEs in Jordan to identify those that are capable and efficient enough to stay in the fierce competition with Europe, when the free trade agreement goes effective in 2014 [20]. UN Industrial Development Organization (UNIDO) has recently launched a credit line for Jordanian SMEs, providing them with information on industrial opportunities, norms and effective regulations in Jordan [17,21]. Over the past few years, the Jordanian government provides the support to SMEs in Jordan including projects and programs that facilitate the access to required accurate information, consulting, and most importantly, access to credit and financial resources (DOS 2011). The main two projects conducted via World Bank to support Jordanian SMEs are United States Agency for International Development (USAID) and National Fund for Enterprise Support (NAFES).
4.1. US Agency for International Development (USAID)
USAID aims to increase the sustainable competitiveness, market out-reach, sales and earnings. It is also aim to provide enterprise level assistance and commercially oriented services to private and public business support enterprises in a cost-effective manner.
4.2. National Fund for Enterprise Support (NAFES)
NAFES aims to assist the Jordanian SMEs in becoming more efficient and competitive with local and global markets by providing financial assistance to management modernization projects aimed at improving their performance and capabilities. NAFES will strive to assure that its efforts are aligned with all other local efforts exerted towards enhancing the role of SMEs in the development of Jordanian economy and in elevating the standard of living of Jordanians. The initial capital of NAFES is obtained from a counterpart fund of a nonproject cash grant donated by the government of Japan. Consulting project and training programs provided by NAFES include:
• Business planning and management systems.
• Production management.
• Financial analysis/management.
• Marketing analysis/sales support.
• Feasibility studies.
• Productivity improvement.
• IT applications such as B2B systems.
Despite the evident benefits obtained from the adoption of IT and IS such as B2B systems, SMEs are slower to adopt the technology compared to their large business counterparts [1-3,6,7,9,16,18,20-42,45-47]. This is particularly the case in developing countries such as Jordan where factors such as the lack of telecommunication infrastructure reference [1-3,6,7,9-11,13,16,18,20-42,45-50] mentioned that further restrict the viability of using B2B systems [1]. Furthermore, reference [50] noted that SMEs have more difficulties in attracting IT specialists to their enterprises, and they also do not have sophisticated distribution systems in comparison to large enterprises. Therefore, SMEs are not adopting B2B systems with the same speed as their larger counterparts.
5. I-EDI System Adoption in SMEs
Reference [1,18,22-31] found that SMEs in general tend to resist adopting I-EDI systems because of a lack of understanding, lack of technical support and limited financial resources. Many researchers of I-EDI systems focused on the factors that make the Internet very attractive for I-EDI system adoption by SMEs:
1) The Internet’s global Internet work connections offer the potential to reach the largest possible number of trading partners.
2) EDI systems can complement or replace current EDI strategies.
3) Using the Internet to exchange EDI transactions is consistent with the growing interest of business in delivering a variety of products and services electronically using the Internet [1,18,21-35].
4) The Internet is a publicly accessible network with few geographical constraints [25].
5) New and powerful tools that make it feasible to interconnect traditional business applications to the Internet with a minimum of challenge are becoming widely available [1,22-26].
6) ISP provides many of the services formerly purchased at a greater cost from traditional VANs [16].
7) The Internet provides simple and widely understood new methods for information exchange [16,26].
Internet Electronic Data Interchange (I-EDI) in Jordan
IT is considered one of the greatest developments in the world of business. IT and IS applications such as EC, B2B, B2C, G2B systems and Internet electronic data interchange (I-EDI) systems are so exciting that many enterprises in the world could be affected. I-EDI systems are an important component of B2B e-commerce systems. Hence, the adoption of I-EDI systems is likely to allow enterprises to become more integrated into the world economy. The degree of effectiveness of the I-EDI systems operation itself, as well as the internal management information available from its use, will certainly be greater if application systems are up-to-date and efficient such as B2B systems. SMEs in Jordan are still facing many challenges in terms of using I-EDI systems in their businesses. Many of these challenges include the lack of experience to deal with such technology, or the fear of the security breaches were provided by I-EDI systems. Many previous studies suggest that I-EDI system adoption can lead to efficiency gains through reduced time to complete transactions and lower services costs [1]. Effective gains can accrue through better service quality and increased sales as a result of better and wider marketing of products. Therefore, if I-EDI systems are to play an integral part in the Jordanian sectors and development strategies, Jordanian enterprises need to understand access and use this technology so that benefits are maximised and disadvantages are minimized [33,34]. Hence, the emphasis must be on B2B trading where opportunities for involvement in the global supply chains via strategic alliances or partnerships with local and global enterprises in worldwide can be seized. The level of IS and IT sophistication and organizational readiness has often been identified as a predictor of successful I-EDI system adoption. Top management support, competitor’s pressure, knowledge and just-by-chance (JBC) factors are the main reason why most large enterprises in Jordan get acquainted with I-EDI systems. Knowledge about this type of new technology and business between TPs locally, or internationally, is still generally lacking [1]. In a prior study, reference [1] found that Jordanian SMEs embrace I-EDI systems mainly because of JustBy-Chance. This contrasts with findings from other studies in developed countries about the impact of I-EDI systems on enterprise in developed countries. The literature shows that Jordan, as a developing country, has achieved forward steps in introducing the Internet to the different sectors of life. The adoption of the electronic tools in business became a governmental target in recent years to make it possible for SMEs to be able to continue to achieve success in their business [1]. Most of Jordanian SMEs have little or no competitive pressure to use I-EDI systems, since most suppliers, customers and other competitors do not seem to promote I-EDI systems.
6. Conclusion
This paper identifies I-EDI as an alternative to traditional EDI. Collected data and literature review also showed a strong trend of businesses wanting to move to I-EDI in Jordan. The study concluded that SMEs in less advanced countries such as Jordan will have stronger Governmental and cultural influences in I-EDI adoption decisions than SMEs in more advanced countries. However, the recent paper asserted that in order to set Jordan on the right course to develop I-EDI system, the government, public and private sectors representatives are now preparing to wage a public information and awareness campaign to show the general public that I-EDI systems are of great benefits; time and cost savings, less paper work, increased effectiveness, streamline processes, less order process time, less transaction time and costs, empowerment of middle managers, clients (companies) services and more time for strategic initiatives. Also the study concluded that Electronic-government can assist Jordanian businesses (SME) by eliminating unnecessary paperwork and thus reducing operating costs when doing business with government agencies. The government can also use the Internet to post information online and offer services to the general public and private companies (SME). However, I-EDI has not grown up or been adopted as quickly as it was forecast among Jordanian SMEs. Furthermore, they encourage SMEs to introduce technologies permitting them to pay and get paid online and to enter Internet based credit and performance risk databases. The topic of I-EDI system adoption is very wide and the area especially in Jordan is just in its beginning of exploration. This study tries to provide some insight to the benefits, drivers, triggers, barriers and factors influences of I-EDI adoption in SME in Jordan. Hence the study concluded that SMEs in Jordan could grow and become larger companies, and supporting national economy. Thus it is very important to develop and grow Jordanian SMEs by doing more research.
REFERENCES
- A. Al-Bakri, “The Adoption of B2B by SME in Amman and the Perceptions of Its Influence on Their Performance and Efficiency,” PhD Thesis (Non-Published Thesis), University of Southern Queensland, Toowoomba, 2009.
- T. R. Peltier, “Information Security Risk Analysis,” CRC Press, Boca Raton, 2001.
- H. Rank and B. Schmitt, “The Challenge of Information Security,” Military Technology, Vol. 29, No. 11, 2005, pp. 8-50.
- T. Thanasankit, “E-Commerce and Cultural Values,” Idea Group Inc., New York, 2002. doi:10.4018/978-1-59140-056-1
- UNCTAD, “Building Confidence: E-Commerce and Development Report,” 2012. http://www.unece.org/trade/untdid/welcome.htm
- M. Gerber and R. Solms, “Information Security Requirements—Interpreting the Legal Aspects,” Computers & Security, Vol. 27, No. 5-6, 2008, pp. 124-135. doi:10.1016/j.cose.2008.07.009
- D. Kim, S. Cavusgil and R. Calantone, “Information System Innovations and Supply Chain Management: Channel Relationships and Firm Performance,” Journal of the Academy of Marketing Science, Vol. 34, No. 1, 2006, pp. 40-54.
- V. Zeithaml, A. Parasuraman and A. Malhotra, “Service Quality Delivery through Web Sites: A critical Review of Extant Knowledge,” Journal of the Academy of Marketing Science, Vol. 30, No.4, 2003, pp. 362-375.
- K. Hausken, “Information Sharing among Firms and Cyber-Attacks,” Journal of Accounting and Public Policy, Vol. 26, No. 6, 2007, pp. 639-688. doi:10.1016/j.jaccpubpol.2007.10.001
- W. Titi, “The Impact of Adoption Electronic Commerce in Small to Medium Enterprises Jordanian Companies,” The 1st International Conference on E-Business and ELearning, Jordan, 24-25 May 2005, pp.159-178.
- M. Stamp, “Information Security,” John Wiley & Sons, New York, 2005. doi:10.1002/0471744190
- M. Warren and W. Hutchinson, “Cyber-Attacks Against Supply Chain Management Systems: A Sort Note,” International Journal of Physical Distribution & Logistics Management, Vol. 30, No. 7-8, 2002, pp. 710-716. doi:10.1108/09600030010346521
- C. Steinfield and P. Whitter, “Community level SocioEconomic Impacts of Electronic commerce,” Journal of Computer Mediated Communication, Vol. 5, No. 2, 1999, pp. 714-719.
- J. Westby, “International Guide to Combating Cybercrime,” American Bar Association, USA, 2003.
- E. Abu Zaid, “Attracting e-Commerce. First GCC ECommerce Conference, UAE,” 2005. www.kenzay-traning.com
- V. Leopoulos, K. Kirytopoulos and D. Voulgaridou, “the benefits of e-commerce: a case study of the Greek Para-pharmaceutical industry,” National Technical University of Athens, Athens, 2006.
- Abu-Ghazaleh and C. Consulting, “Market Brief on Telecommunications Sector in Jordan,” 2009. http://www.commercecan.ic.gc.ca
- Department of Statistics in Jordan (DOS), Census of Enterprises, 2011. http://www.dos.gov.jo
- A. Abu-Samaha and Y. Abdel Samad, “Challenges to the Jordanian Electronic Government Initiative,” Journal of Business Systems, Governance and Ethics, Vol. 2, No. 3, 2007, pp. 101-109.
- Ministry of Trade and Industry in Jordan, 2010. http://www.mit.gov.jo
- Ministry of Industry and Trade in Jordan (MIT), 2012. http://www.mit.gov.jo
- M. Al-Ibraheem and H. Tahat, “Regulating Electronic Contracting in Jordan,” 21st BILETA Conference; Globalization and Harmonization in Technology Law, Malta, 6-7 April 2006, pp. 6-19.
- Arab Advisor Group, 2012.www.arabadvisors.com
- Arab Advisor Press Room, 2012. http://www.arabadvisors.com
- N. Black, A. Lockett, H. Winklhofer and C. Ennew, “The Adoption of Internet Financial Services: A Qualitative Study,” International Journal of Retail and Distribution Management, Vol. 29, No. 8, 2000, pp. 390-398. doi:10.1108/09590550110397033
- S. Blythe, “Digital Signature Law of the United Nation. European Union, United Kingdom and United state: Promotion of Growth in E-commerce with Enhanced Security,” Richmond Journal of Law and Technology, Vol. XI, No. 2, 2005, pp. 1-20.
- Business Integration Technology, Inc., “Why Supply Chain Executives Should Care about B2B Integration Technology,” 2012. http://businessintegrationtechnology.com/PDF/WhyB2BiMatters.pdf
- Business Integration Technology Inc., 2012. http://www.businessintegrationtechnology.com
- J. Caldow, “The Quest for Electronic Government: A Defining Vision,” Institute for Electronic Government, IBM Corporation, Washington DC, 1999.
- C. Easttom, “Computer Security Fundamentals,” Pearson Prentice Hall, Michigan, 2007.
- C. Iacovou, I. Benbasat and A. Dexter, “‘Electronic Data Interchange and Small Organizations: Adoption and Impact of Technology,” MIS Quarterly, Vol. 19, No. 4, 1995, pp. 465-481. doi:10.2307/249629
- M. El-Nawawy and M. Ismail, “Overcoming Deterrents and Impediments to Electronic Commerce in Light of Globalization,” Proceedings of the 9th Annual Conference of the Internet Society, INET 99, San Jose, 22-25 June 1999, pp. 9-18.
- ESCWA, “National profile of the Information Society in Jordan,” United Nation Report, 2007, pp. 1-16.
- ESCWA, “Development of E-Commerce Sectors in the Arab Region,” World Summit on the Information Society (WSIS), Beirut, 4-6 February 2003, pp. 53-65.
- J. Fraser, “The Strategic Challenge of Electronic Commerce,” Supply Chain Management, Vol. 5, No. 1, 2000, p. 7. doi:10.1108/13598540010312936
- M. Greenstein and T. Feinman, “Electronic Commerce; Security, Risk Management and Control,” McGraw-Hill, Boston, 2000.
- R. Gulati, “Business-to-Business E-Commerce: Past, Present, and Future,” 2012.
- E. M. Heffes, “Refining the Rules of Commerce,” Financial Executive, Vol. 17, No. 3, 2001, pp. 3-18.
- E. Kritzingera and E. Smith, “Information Security Management: A Previous Term Information Security Retrieval and Awareness Model for Industry,” Computers & Security, June 2008
- T. Layton, “Guide to Information Security,” CRC Press, Boca Raton, 2006.
- Ministry of Information and Communication Technologies in Jordan (MICT), “The E-Readiness Assessment of the Hashemite Kingdom of Jordan,” 2011. http://www.moit.gov.jo
- Organization for Economic Cooperation and Development OECD, “Economic Growth in the OECD Area,” OECD Working Paper, 2000.
- Organization for Economic Cooperation and Development OECD, “E-Commerce: Impacts and Policy Challenges,” Organization for Economic Cooperation and Development (OECD), Vol. 67, No. 193, 2000, pp. 193- 202.
- Organization for Economic Cooperation and Development OECD, “The Economic and Social Impacts of electronic Commerce,” Preliminary Finding and Research Agenda, 1999.
- Organization for Economic Cooperation and Development (OECD), “E-Commerce: Impacts and Policy Challenges,” 2002.
- Y. Rezgui and A. Marks, “Information Security Awareness in Higher Education: An Exploratory Study,” Computers and Security, Vol. 27, No. 7, 2007, pp. 241-253.
- M. Sahawneh, “E-Commerce and Its Effect on Labor Force” Socio-economic Impact of Persistent Organic Pollutants,” Royal Scientific Society, 2005.
- M. Sahawneh, “E-Commerce: The Jordanian Experience, Industrial Studies Department,” Royal Scientific Society, 2002.
- R. Schperberg and R. Kenneth, “Cybercrime,” ISACA, Rolling Meadows, 2005.
- P. Chanu, “Determinants of Small Business EDI Adoption: An Empirical Investigation,” Journal of Organisational Computing and Electronic Commerce, Vol. 11, No. 4, 2001, pp. 229-252. doi:10.1207/S15327744JOCE1104_02

