American Journal of Operations Research
Vol. 3 No. 1A (2013) , Article ID: 27533 , 7 pages DOI:10.4236/ajor.2013.31A008
Stochastic Design of Enhanced Network Management Architecture and Algorithmic Implementations
W. CySip Graduate School of Business, Asian Institute of Management, Makati, Philippines
Email: SKim@aim.edu
Received October 2, 2012; revised November 5, 2012; accepted November 16, 2012
Keywords: Stochastic Network Management; N-Policy; Closed Queue; Algorithmic Implementation; Stochastic Optimization
ABSTRACT
The paper is focused on available server management in Internet connected network environments. The local backup servers are hooked up by LAN and replace broken main server immediately and several different types of backup servers are also considered. The remote backup servers are hooked up by VPN (Virtual Private Network) with high-speed optical network. A Virtual Private Network (VPN) is a way to use a public network infrastructure and hooks up long-distance servers within a single network infrastructure. The remote backup servers also replace broken main severs immediately under the different conditions with local backups. When the system performs a mandatory routine maintenance of main and local backup servers, auxiliary servers from other location are being used for backups during idle periods. Analytically tractable results are obtained by using several mathematical techniques and the results are demonstrated in the framework of optimized networked server allocation problems. The operational workflow give the guidelines for the actual implementations.
1. Introduction
In light of the recent acts of terrorism and cyberterrorism, it becomes imperative not only to provide a network security (that has never been a full-proof), but to offer a paradigm of a “network security system” which can be applied to networking for the business continuity such as stock market, postal offices, nuclear power plants, and government offices. Availability [1] of networked servers is a major issue in security respects because of rapid growth of Internet. The paper is focused on enhancement of network availability to support more reliable services. Two types of backup servers are considered. Local backup servers are located in same area and hooked up via LAN (Local Area Network) and he remote backup servers are geometrically separated with main servers but remote backups are hooked up by a Virtual Private Network (VPN) with high-speed optical Internet. A VPN is networking between remote servers and clients via using a public telecommunication infrastructure with secure access to their organization’s network. Unlike an expensive system of owned or leased lines, a VPN can provide the organization with the same capabilities, but at a much lower cost. The 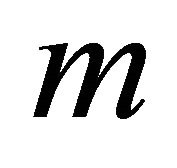 main working servers with the
main working servers with the  local backups and
local backups and  remote backup servers are geometrically separated with main servers.
remote backup servers are geometrically separated with main servers.
The remote (backup) servers are hooked up by a Virtual Private Network (VPN) and can be used during the maintenance of internal backup servers or absence of the repair facility (see Figure 1). The number of the remote backups has the control level  within the total number
within the total number  of remote backups. Unlike previous research from author [2], N-policy is applied to restrict the quantity of external resources. A VPN is networking between remote servers and client via using either a public telecommunication infrastructure such as Internet with secure access to private network and secured network such as military system.
of remote backups. Unlike previous research from author [2], N-policy is applied to restrict the quantity of external resources. A VPN is networking between remote servers and client via using either a public telecommunication infrastructure such as Internet with secure access to private network and secured network such as military system.
In this article we study a class of closed queueing systems with the initial quantity of  main unreliable machines,
main unreliable machines,  reserve machines and
reserve machines and 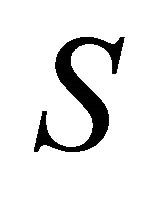 auxiliary reserve machines, also called “super-reserve” machines [3-4]. Main working machines are subject to “exponential failures” and their repairs are rendered (in the FIFO order) by a single repair facility (referred to as the repairman) with generally distributed repair times or replacement times to exchange as new machines. As soon as a main working machine breaks down, it is immediately replaced by a reserve machine if available. The total quantity of working machines must not exceed
auxiliary reserve machines, also called “super-reserve” machines [3-4]. Main working machines are subject to “exponential failures” and their repairs are rendered (in the FIFO order) by a single repair facility (referred to as the repairman) with generally distributed repair times or replacement times to exchange as new machines. As soon as a main working machine breaks down, it is immediately replaced by a reserve machine if available. The total quantity of working machines must not exceed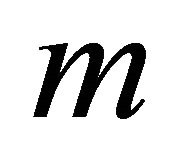 . Occasionally, the group of reserve machines is blocked for the sake of some routine maintenance, and during this
. Occasionally, the group of reserve machines is blocked for the sake of some routine maintenance, and during this
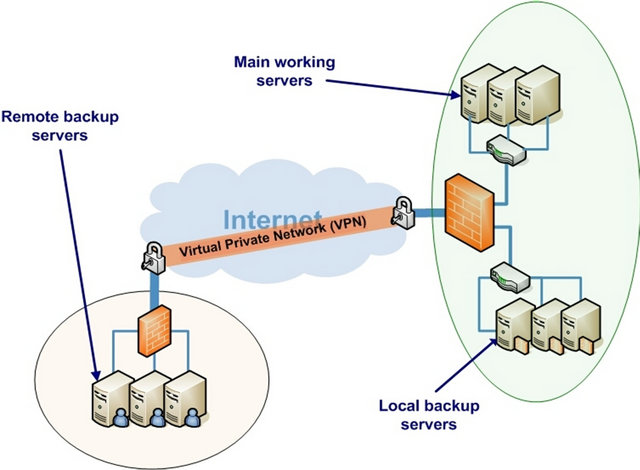
Figure 1. Mixture of the local and the remote backups.
period of time, super-reserve machines take over the duties of reserve machines. The super-reserve facility is “activated” whenever the main and reserve facilities combined are restored to its original quantity , and then the system “regenerates”. While all main machines keep on working, in the event of failures, the system turns to super-reserve facility, and the repairman is unavailable.
, and then the system “regenerates”. While all main machines keep on working, in the event of failures, the system turns to super-reserve facility, and the repairman is unavailable.
Defective machines are replaced by auxiliary reserve machines whose total number is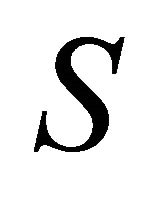 . However, the system tries not exhaust this quantity and sets up a smaller control number
. However, the system tries not exhaust this quantity and sets up a smaller control number . During this period of time, the system is observed only upon some random epochs of time, while dropped machines line up in the “waiting room”. If at one of these observation epochs, the number of defective machines reaches or exceeds
. During this period of time, the system is observed only upon some random epochs of time, while dropped machines line up in the “waiting room”. If at one of these observation epochs, the number of defective machines reaches or exceeds  (after some delay), the repairman returns to his duties, a busy period begins, and thereby the busy cycle continues. This is a more realistic scenario of a reliability system that functions under restricted observations, at least during its maintenance periods. The scenario can be directly applied for network management. The control integer variable
(after some delay), the repairman returns to his duties, a busy period begins, and thereby the busy cycle continues. This is a more realistic scenario of a reliability system that functions under restricted observations, at least during its maintenance periods. The scenario can be directly applied for network management. The control integer variable 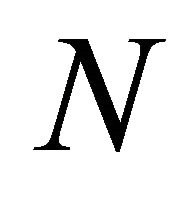 (less than or equal to
(less than or equal to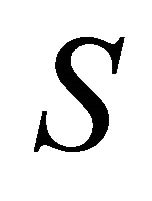 ), whose value, among other parameters, is determined in the framework of a comprehensive optimization. Operational workflow gives the implementation guidelines for network management based on the mathematical results. The mathematical values are the initial conditions for network management operations and the detailed workflow will be explained in this paper.
), whose value, among other parameters, is determined in the framework of a comprehensive optimization. Operational workflow gives the implementation guidelines for network management based on the mathematical results. The mathematical values are the initial conditions for network management operations and the detailed workflow will be explained in this paper.
2. Mathematical Design for Enhance Network Architecture
The Duality Principle [5] is applied and it includes another reliability model, which is more simple than the main model (i.e., Model 1) and to which we will refer as to Model 2. Model 2 is similar to Model 1, except that it does not have the super-reserve facility and idle periods. Besides, the total number of reserve machines is 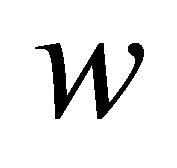 (i.e. less by one than in Model 1. We rather associate it with repairman’s vacations, which are distributed as regular repairs. However, upon his return, the repairman brings a brand new machine, which replaces any one that breaks down during his vacation trip if any such available. Otherwise, the new machine he brings in substitutes any other machine and in both cases the old machine is disposed. Model 2 is directly connected with yet another model, which we will call Model 3. Model 3 is a multichannel queueing system, with buffer of capacity
(i.e. less by one than in Model 1. We rather associate it with repairman’s vacations, which are distributed as regular repairs. However, upon his return, the repairman brings a brand new machine, which replaces any one that breaks down during his vacation trip if any such available. Otherwise, the new machine he brings in substitutes any other machine and in both cases the old machine is disposed. Model 2 is directly connected with yet another model, which we will call Model 3. Model 3 is a multichannel queueing system, with buffer of capacity , and state dependent arrival process, in notation,
, and state dependent arrival process, in notation, .
.
Let  be the successive moments of repair
be the successive moments of repair completions and let
completions and let . be the successive repair durations all during a busy period. (For brevity of notation, we use
. be the successive repair durations all during a busy period. (For brevity of notation, we use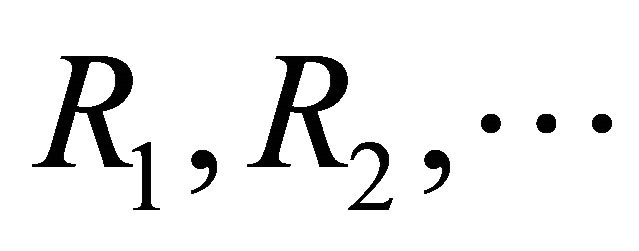 . as generic random variables for every busy period.) The random variables
. as generic random variables for every busy period.) The random variables 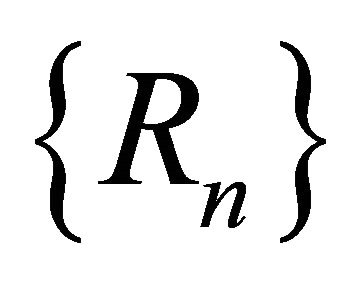 are iid with a common probability distribution function [6]
are iid with a common probability distribution function [6]
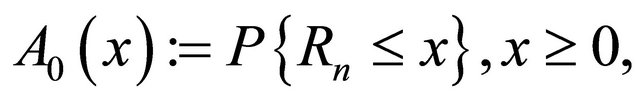 (2.1)
(2.1)
and mean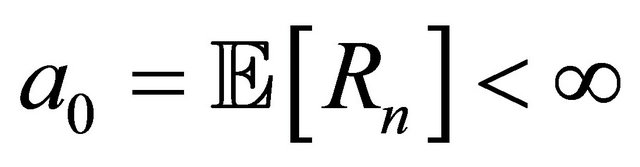 . Each of the main machines breaks down independently of each other and of repairs, and according to the exponential distribution with parameter
. Each of the main machines breaks down independently of each other and of repairs, and according to the exponential distribution with parameter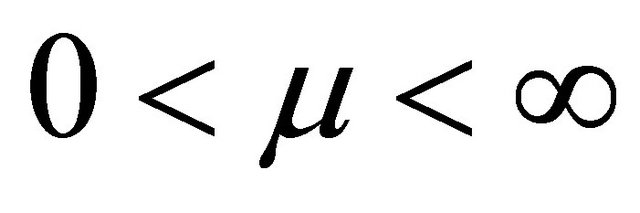 . Notice that
. Notice that 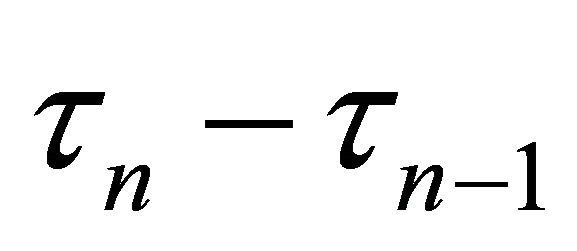 need not equal
need not equal , unless the corresponding repair belongs to a busy period. The prebusy period is included in the busy period; the reason for distinguishing this time from the rest of the busy period is for the descriptional convenience and for below arguments regarding the duality principle. We interpret the entire prebusy period as a part of state dependent service with the first service initiating a busy period distributed as the convolution
, unless the corresponding repair belongs to a busy period. The prebusy period is included in the busy period; the reason for distinguishing this time from the rest of the busy period is for the descriptional convenience and for below arguments regarding the duality principle. We interpret the entire prebusy period as a part of state dependent service with the first service initiating a busy period distributed as the convolution
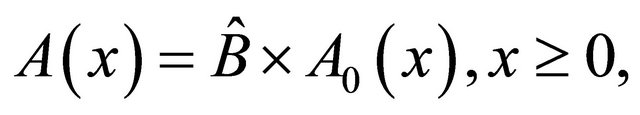 (2.2)
(2.2)
where 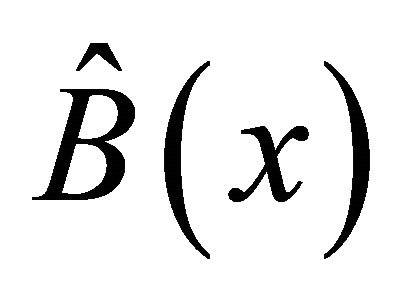 denotes the PDF of the random variable
denotes the PDF of the random variable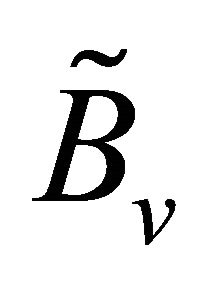 . If at time
. If at time 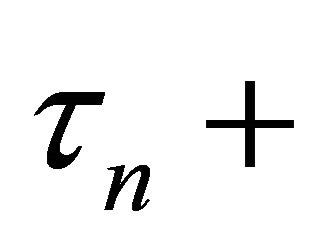 (immediately after the
(immediately after the 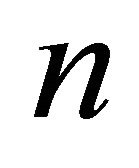 th repair completion), the total quantity of intact (i.e. main working and reserve machines) is less than
th repair completion), the total quantity of intact (i.e. main working and reserve machines) is less than , the busy period goes on.
, the busy period goes on.
Model 3 describes the number of customers in a  queueing system with state dependent arrival stream. More specifically, it is like a multichannel queue
queueing system with state dependent arrival stream. More specifically, it is like a multichannel queue 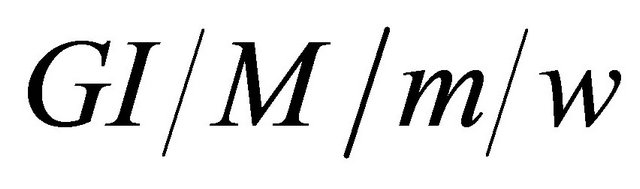 (of Takacs [7]), except for the input is not a “general independent”, but it “varies” dependent on the queue length. If upon any arrival, the total number of customers (including those in service) are less than
(of Takacs [7]), except for the input is not a “general independent”, but it “varies” dependent on the queue length. If upon any arrival, the total number of customers (including those in service) are less than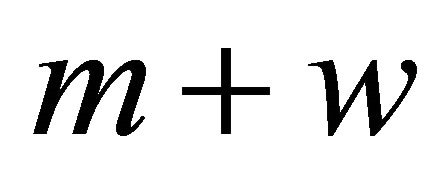 , the PDF of the next inter-arrival time is
, the PDF of the next inter-arrival time is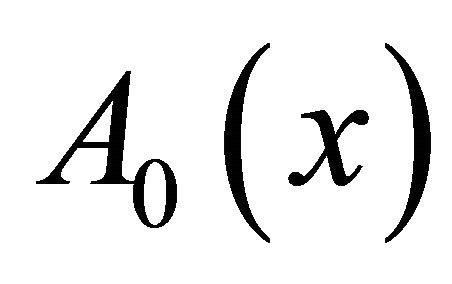 . Otherwise, the customers gets lost and the next inter-arrival time is distributed as
. Otherwise, the customers gets lost and the next inter-arrival time is distributed as  of (2.2). While Models 2 and 3 seem to be identical, we call them stochastically congruent.
of (2.2). While Models 2 and 3 seem to be identical, we call them stochastically congruent.
Let  be the limiting probabilities of the process
be the limiting probabilities of the process  These probabilities exist under the same conditions as those for the embedded process [2].
These probabilities exist under the same conditions as those for the embedded process [2].
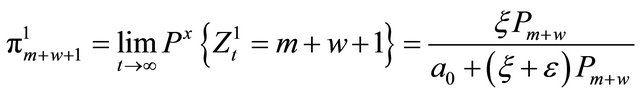 (2.3)
(2.3)
and
 (2.4)
(2.4)
where
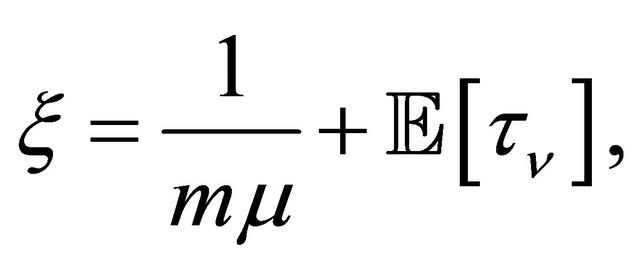
and
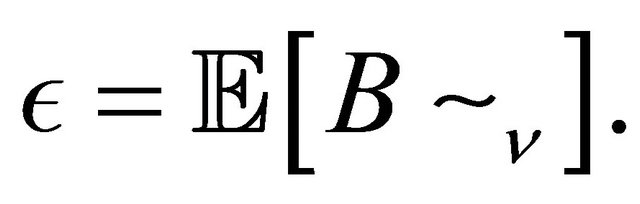
And  is subject to our further consideration.
is subject to our further consideration.
In the other hand, this model is controlled by the socalled “first excess level process” from fluctuation theory. This is a marked three-variate point renewal process with all dependent components. This process by itself can be applied the practical applications such as router design 8. The process will be “terminated” at some of the random observation times when one of its “active” components crosses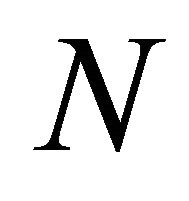 , and because its value can be of any magnitude with positive probability, the first excess level will be curtailed to its maximal number
, and because its value can be of any magnitude with positive probability, the first excess level will be curtailed to its maximal number  should it formally exceed
should it formally exceed . The vacation period ends and the repairman resumes his usual duty. The period of time from
. The vacation period ends and the repairman resumes his usual duty. The period of time from 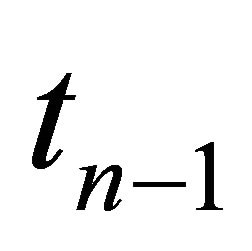 until
until 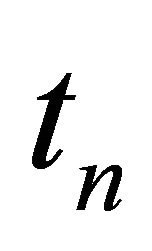 may or may not include a vacation period and we therefore call it the
may or may not include a vacation period and we therefore call it the  th service cycle. During repairman’s vacation period, all
th service cycle. During repairman’s vacation period, all  reserve machines are blocked and the main working facility is backed up by super-reserve machines, which the system “borrows” from a source limited to
reserve machines are blocked and the main working facility is backed up by super-reserve machines, which the system “borrows” from a source limited to 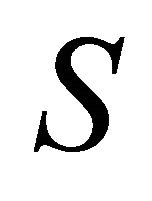 units. While all
units. While all 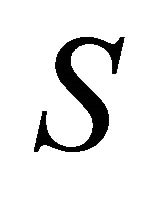 of them are available, the system attempts to utilize not all superreserve machines. Namely, it sets up a threshold
of them are available, the system attempts to utilize not all superreserve machines. Namely, it sets up a threshold , a specific reference number (to be optimized), the system tries not to exceed.
, a specific reference number (to be optimized), the system tries not to exceed.
It is assumed that from the beginning of a vacation period, the status of the system is observed upon some random epochs of time. To simplify notation and without loss of generality we will formalize this process on the first service cycle. Suppose that at , when all of
, when all of 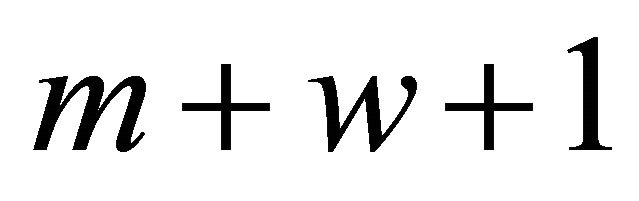 machines become intact, the repairman leaves the main reserve facility, and the system is observed upon the times
machines become intact, the repairman leaves the main reserve facility, and the system is observed upon the times . We will begin with
. We will begin with 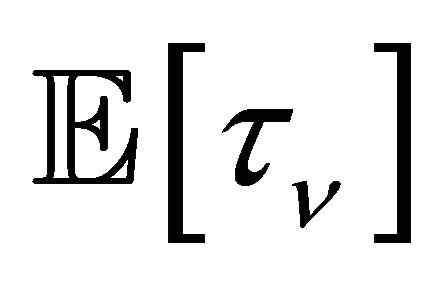 which is the average period of using the super-reserve machines. Let us assume that the random variables
which is the average period of using the super-reserve machines. Let us assume that the random variables 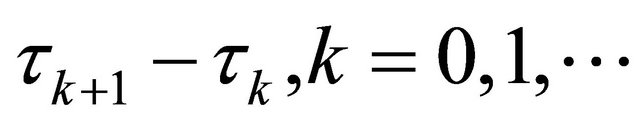 are exponentially distributed, with common mean
are exponentially distributed, with common mean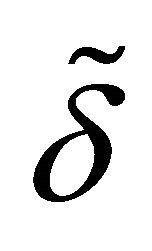 . By the theorem by author [3-4], we have
. By the theorem by author [3-4], we have
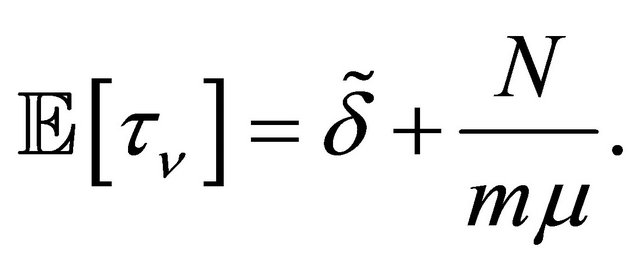
Now, we turn to 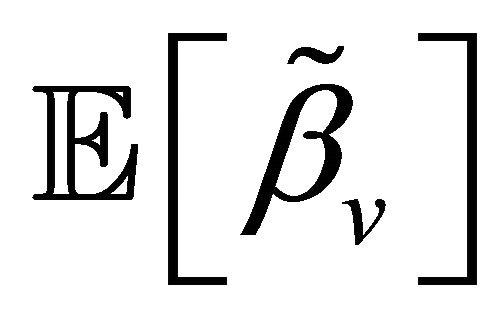 that is the average number of super-reserve machine usage:
that is the average number of super-reserve machine usage:
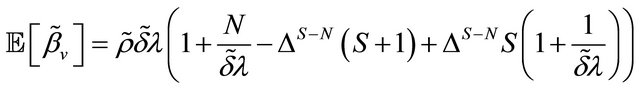
where  is the average repair time for single machine. Since
is the average repair time for single machine. Since , we get
, we get
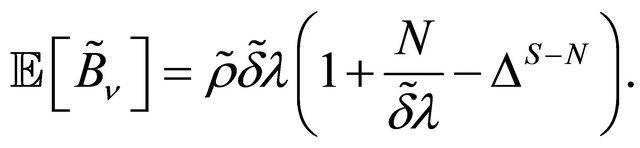
where

Model 3, as mentioned, is the  (multi-channel) queue with state dependent arrivals,
(multi-channel) queue with state dependent arrivals,  parallel channels, and a buffer or waiting room of capacity
parallel channels, and a buffer or waiting room of capacity  [7]. A customer enters a free channel available with his service demand distributed exponentially with parameter
[7]. A customer enters a free channel available with his service demand distributed exponentially with parameter . Model 2, as we see it, is congruent to Model 3, while Model 1 is dual with Model 2 (See Dshalalow [5] and Kim [4]
. Model 2, as we see it, is congruent to Model 3, while Model 1 is dual with Model 2 (See Dshalalow [5] and Kim [4] . The stationary probabilities
. The stationary probabilities 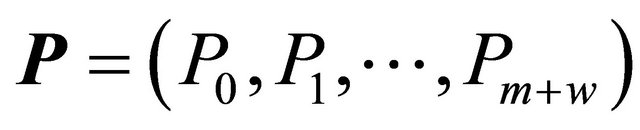 for the embedded process are known to satisfy the following formulas
for the embedded process are known to satisfy the following formulas
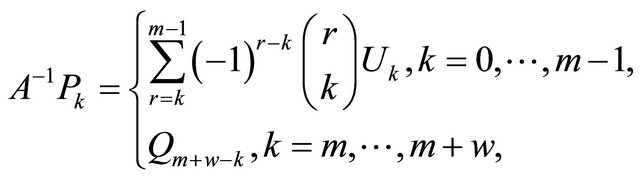
where
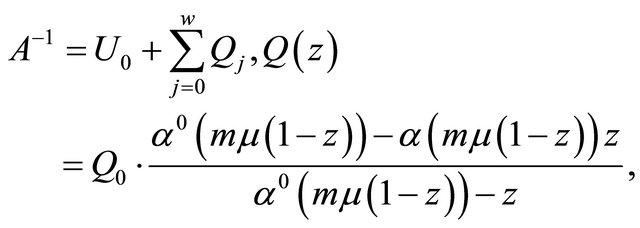 (2.7)
(2.7)


and  of (4.1) is the generating function, convergent in the open disc centered at zero. By using the Kolmogorov differential equation and the semi-regenerative techniques [2-4,8-9], this system has been solved by Dshalalow [6]. The limiting distribution
of (4.1) is the generating function, convergent in the open disc centered at zero. By using the Kolmogorov differential equation and the semi-regenerative techniques [2-4,8-9], this system has been solved by Dshalalow [6]. The limiting distribution  is:
is:
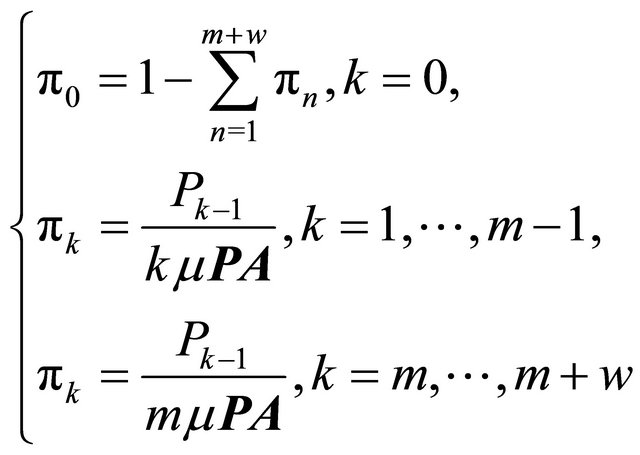 (2.8)
(2.8)
where

For the process  the corresponding formulas yield
the corresponding formulas yield
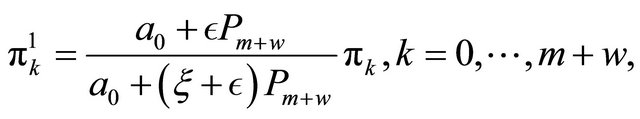 (2.9)
(2.9)
 (2.10)
(2.10)
along with (2.8).
3. Networked Server with Controlled Backup Optimization
The stochastic optimization techniques are used for the sample illustration of the optimization and the stochastic optimization techniques by itself can be applied to realworld problems such as computer-networking, human resources and manufacturing process. Let a strategy, say , specify, ahead of the time, a set of acts we impose on the system and the system can be subject to a set
, specify, ahead of the time, a set of acts we impose on the system and the system can be subject to a set  of cost functions. The general formula of stochastic optimization is [2-4]:
of cost functions. The general formula of stochastic optimization is [2-4]:
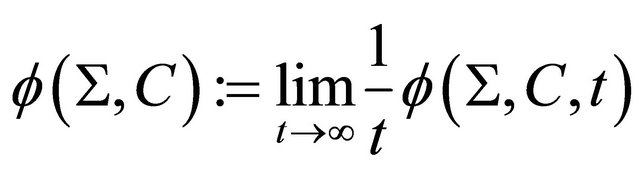 (3.1)
(3.1)
Now we turn to convergence theorems for semiregenerative, semi-Markov, and Markov renewal processes [10],

to arrive at the objective function 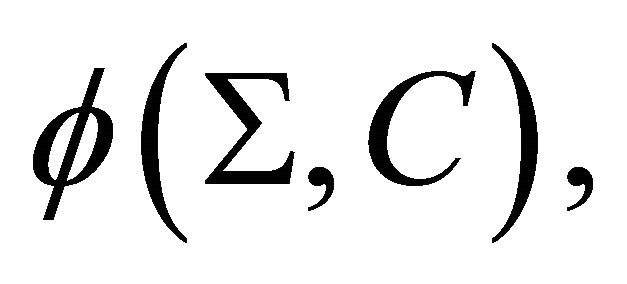 which gives the total expected rate of all processes over an infinite horizon. As a reasonable performance measure, let us consider the reliability factor
which gives the total expected rate of all processes over an infinite horizon. As a reasonable performance measure, let us consider the reliability factor , which represents the probability of the number of intact machines at any moment of time in equilibrium:
, which represents the probability of the number of intact machines at any moment of time in equilibrium:
 (3.2)
(3.2)
This is not only a reliability measure of the system, but it can also serve as a constraint to an optimally functioning the system. We arrive at the following expression for the sample objective function [2]:
 (3.3)
(3.3)
Take the total number of main networked servers as 2 and the total number of local backups is . We are setting up the maximal availability of remote backup servers to 15. Hence,
. We are setting up the maximal availability of remote backup servers to 15. Hence,  and
and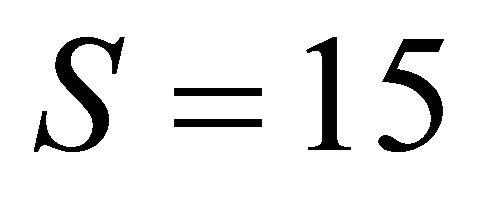 .
.
Now, we calculate 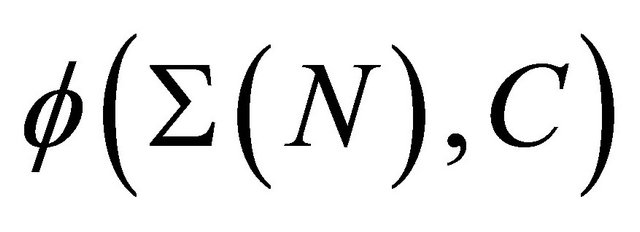 and
and  that gives a minimum for
that gives a minimum for . In other words, the control level
. In other words, the control level  stands for the excess level of remote backup which minimizes the total cost of this system. Below is a plot of
stands for the excess level of remote backup which minimizes the total cost of this system. Below is a plot of  for
for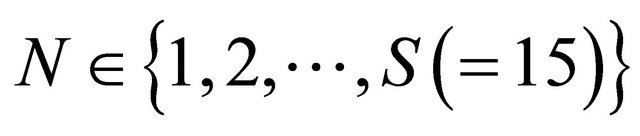 .
.
Our calculation yields that 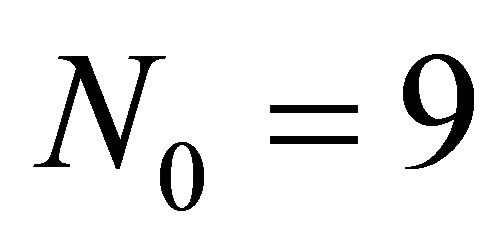 for which the minimal cost equals 15.6445. It means that we allocate our internal resources to 2 main
for which the minimal cost equals 15.6445. It means that we allocate our internal resources to 2 main and 4 internal
and 4 internal 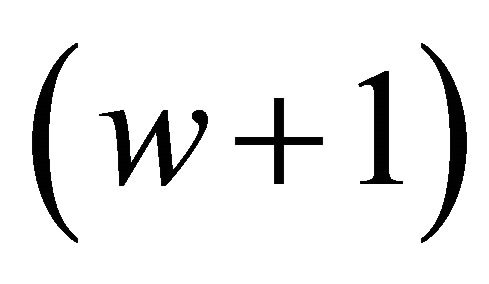 networked servers and obtain the threshold value
networked servers and obtain the threshold value  which gives us the decision point that is the number of remote backups which we need from external resources to minimize the cost of the backup system. Using the above example of our model, we arrive at the reliability factor is
which gives us the decision point that is the number of remote backups which we need from external resources to minimize the cost of the backup system. Using the above example of our model, we arrive at the reliability factor is . It tells us that the likelihood of having at least
. It tells us that the likelihood of having at least 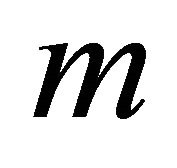 intact main networked server is 0.2607.
intact main networked server is 0.2607.
4. Algorithmic Implementations for the Enhanced Network Architecture
The network architecture that has mentioned in the previous is the mathematical and theoretical approach to analyze the stochastic model. The operational method is the guideline for actual implementation. The workflow of operating the enhance network management can be easily adapted for software programming and simulation. All of the mathematical results from the previous sections are applied into the operational method as the initial conditions. The variables need to be defined for using the results from the mathematical model. Number of iteration, number of main and backup servers, the status of the repair facility are some of key factors for implementation. The variables for operations of enhanced network management are as follow:
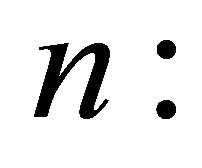 number of iterations
number of iterations
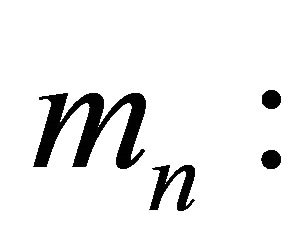 number of main servers at iteration
number of main servers at iteration 
 number of local backup servers at iteration
number of local backup servers at iteration 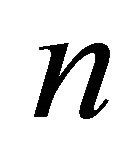
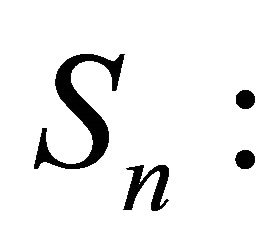 number of remote backup servers at iteration
number of remote backup servers at iteration 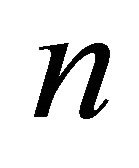
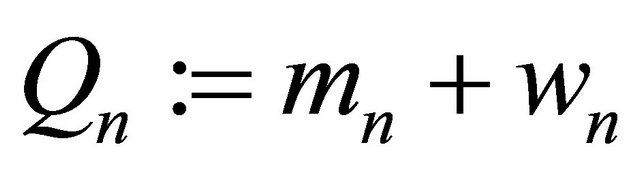
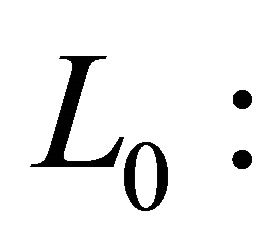 control level of remote backup servers
control level of remote backup servers
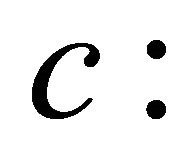 counting number of remote backup usage
counting number of remote backup usage
 number of servers that have been fixed within Iterations
number of servers that have been fixed within Iterations

The values in the mathematical model are applied as the initial conditions in the operational workflow but the notations are different. The delta of notations between mathematical model and operational method is shown in Table 1.
The operational workflow can be presented after defining the initial condition (see Figure 2) The workflow is the depiction of a sequence of operations for enhanced network management that is focused on service availability.
If the operations is applied in the example case in Section 3, the actual values of the initial condition are given:
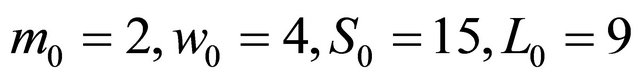
based on the delta list (see Table 1) The network management based on above operation workflow gives the optimal performance in server availability perspective.
5. Conclusion
In this article theoretical approaches of the network defense model is presented. Unlike simulated model, we can find the explicit formulas that is the key elements of the complex model. In addition, this model can be also applied various real-world applications such as network system design 8 and software architecture [11]. Analytically tractable results are obtained by using a duality principle
Table 1. Delta list of the initial condition.

Figure 2. Operations workflow of enhance network.
(which enables us to treat a more rudimentary system), semi-regenerative analysis, and the theory of fluctuations of multivariate marked renewal processes. The results are applied in the framework of optimization problems.
REFERENCES
- D. Russell and G. T. Ganemi Sr., “Computer Security Basics,” O’ Reilly and Asso. Inc., Sebastopol, 2006.
- S.-K. Kim, “Enhanced Networked Server mgt. with Random Remote Backups,” Proceedings of SPIE 5244, Orlando, 7 September 2003, pp. 106-114. doi:10.1117/12.511412
- S.-K. Kim, “Enhanced Management Method of Storage Area Network (SAN) Server with Random Remote Backups,” Mathematical and Computer Modelling, Vol. 42, No. 9-10, 2005, pp. 947-958. doi:10.1016/j.mcm.2005.06.006
- S.-K. Kim, “Enhanced Stochastic Methodology for Combined Architecture of e-Commerce and Security Networks,” Mathematical Problems in Engineering, Vol. 2009, 2009, Article ID: 691680.
- J. H. Dshalalow, “On a Duality Principle in Processes of Servicing Machines with Double Control,” Journal of Applied Mathematics, Vo. 1, No. 3, 1988, pp. 245-251.
- J. H. Dshalalow, “Queueing Systems with State Dependent Parameters,” In: J. H. Dshalalow, Ed., Frontiers in Queueing, CRC Press, Boca Raton, 1997, pp. 61-116.
- L. Takacs, “Some Probability Questions in the Theory of Telephone Traffic,” Magyar Tudományos Akadémia. Matematikai és Fizikai Osztály Közleményei, Vol. 8, 1958, pp. 155-175.
- S.-K. Kim, “Design of Stochastic Hitless-Prediction Router by Using the First Exceed Level Theory,” Mathematical Methods in the Applied Sciences, Vol. 28, No. 12, 2005, pp. 1481-1490. doi:10.1002/mma.626
- J. H. Dshalalow, “On the Multiserver Queue with Finite Waiting Room and Controlled Input,” Advanced Applied Probability, Vol. 17, No. 2, 1985, pp. 408-423. doi:10.2307/1427148
- E. Cinlar, “Introduction to Stochastic Processes,” Prentice Hall, Englewood Cliffs, 1975.
- S.-K. Kim, “Design of Enhanced Software Protection Architecutre by Using Theory of Inventive Problem Solving,” IEEE Proceedings of IEEM, Hong Kong, 8-11 December 2009, pp. 978-982.

