Z. CHEN ET AL.171
and energy consumption per bit, the plot of energy con-
sumption per bit versus the throughput can compare the
energy saving performance of CLAC and TLAC fairly
and clearly.
In order to generate this plot, some assumptions must
be made about the parameters of the WSN. It is assumed
that the WSN consist of 16N
sensor nodes. A data
rate of , a noise power of
and a frequency bandwidth of are chosen
for the physical layer. A transmit probability
20kbpsR110dbmw
N
P
20kHzB
116p
is used for TLAC. The resulting energy consumption per
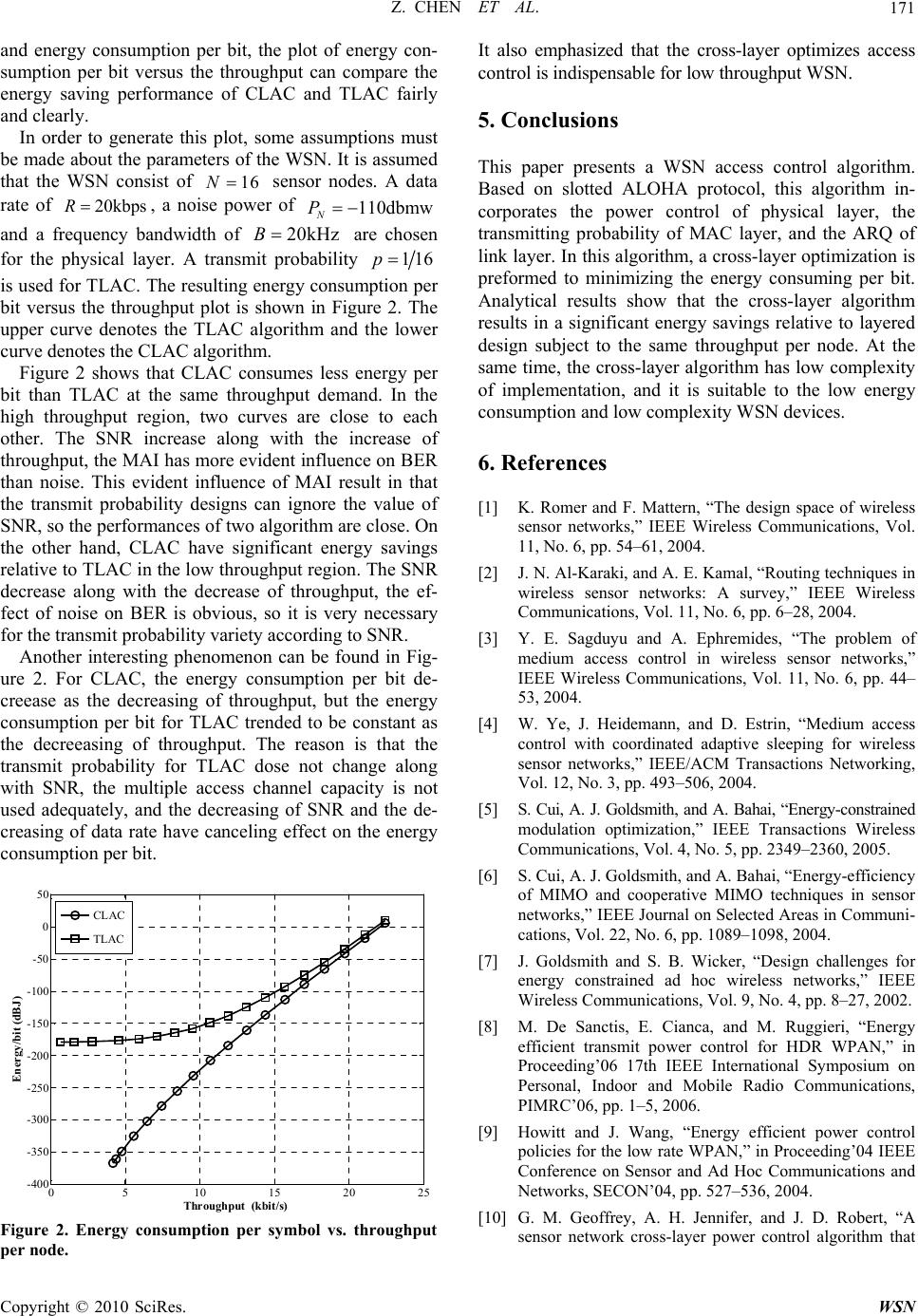
bit versus the throughput plot is shown in Figure 2. The
upper curve denotes the TLAC algorithm and the lower
curve denotes the CLAC algorithm.
Figure 2 shows that CLAC consumes less energy per
bit than TLAC at the same throughput demand. In the
high throughput region, two curves are close to each
other. The SNR increase along with the increase of
throughput, the MAI has more evident influence on BER
than noise. This evident influence of MAI result in that
the transmit probability designs can ignore the value of
SNR, so the performances of two algorithm are close. On
the other hand, CLAC have significant energy savings
relative to TLAC in the low throughput region. The SNR
decrease along with the decrease of throughput, the ef-
fect of noise on BER is obvious, so it is very necessary
for the transmit probability variety according to SNR.
Another interesting phenomenon can be found in Fig-
ure 2. For CLAC, the energy consumption per bit de-
creease as the decreasing of throughput, but the energy
consumption per bit for TLAC trended to be constant as
the decreeasing of throughput. The reason is that the
transmit probability for TLAC dose not change along
with SNR, the multiple access channel capacity is not
used adequately, and the decreasing of SNR and the de-
creasing of data rate have canceling effect on the energy
consumption per bit.
05 10 15 20 25
-400
-350
-300
-250
-200
-150
-100
-50
0
50
Throughput (kbit/s)
Energy/bit (dBJ)
CLAC
TLAC
Figure 2. Energy consumption per symbol vs. throughput
per node.
It also emphasized that the cross-layer optimizes access
control is indispensable for low throughput WSN.
5. Conclusions
This paper presents a WSN access control algorithm.
Based on slotted ALOHA protocol, this algorithm in-
corporates the power control of physical layer, the
transmitting probability of MAC layer, and the ARQ of
link layer. In this algorithm, a cross-layer optimization is
preformed to minimizing the energy consuming per bit.
Analytical results show that the cross-layer algorithm
results in a significant energy savings relative to layered
design subject to the same throughput per node. At the
same time, the cross-layer algorithm has low complexity
of implementation, and it is suitable to the low energy
consumption and low complexity WSN devices.
6. References
[1] K. Romer and F. Mattern, “The design space of wireless
sensor networks,” IEEE Wireless Communications, Vol.
11, No. 6, pp. 54–61, 2004.
[2] J. N. Al-Karaki, and A. E. Kamal, “Routing techniques in
wireless sensor networks: A survey,” IEEE Wireless
Communications, Vol. 11, No. 6, pp. 6–28, 2004.
[3] Y. E. Sagduyu and A. Ephremides, “The problem of
medium access control in wireless sensor networks,”
IEEE Wireless Communications, Vol. 11, No. 6, pp. 44–
53, 2004.
[4] W. Ye, J. Heidemann, and D. Estrin, “Medium access
control with coordinated adaptive sleeping for wireless
sensor networks,” IEEE/ACM Transactions Networking,
Vol. 12, No. 3, pp. 493–506, 2004.
[5] S. Cui, A. J. Goldsmith, and A. Bahai, “Energy-constrained
modulation optimization,” IEEE Transactions Wireless
Communications, Vol. 4, No. 5, pp. 2349–2360, 2005.
[6] S. Cui, A. J. Goldsmith, and A. Bahai, “Energy-efficiency
of MIMO and cooperative MIMO techniques in sensor
networks,” IEEE Journal on Selected Areas in Communi-
cations, Vol. 22, No. 6, pp. 1089–1098, 2004.
[7] J. Goldsmith and S. B. Wicker, “Design challenges for
energy constrained ad hoc wireless networks,” IEEE
Wireless Communications, Vol. 9, No. 4, pp. 8–27, 2002.
[8] M. De Sanctis, E. Cianca, and M. Ruggieri, “Energy
efficient transmit power control for HDR WPAN,” in
Proceeding’06 17th IEEE International Symposium on
Personal, Indoor and Mobile Radio Communications,
PIMRC’06, pp. 1–5, 2006.
[9] Howitt and J. Wang, “Energy efficient power control
policies for the low rate WPAN,” in Proceeding’04 IEEE
Conference on Sensor and Ad Hoc Communications and
Networks, SECON’04, pp. 527–536, 2004.
[10] G. M. Geoffrey, A. H. Jennifer, and J. D. Robert, “A
sensor network cross-layer power control algorithm that
Copyright © 2010 SciRes. WSN