Communications and Network
Vol.6 No.2(2014), Article ID:46373,18 pages
DOI:10.4236/cn.2014.62016
Analysis of Different Call Admission Control Strategies and Its Impact on the Performance of LTE-Advanced Networks
Mahammad A. Safwat1, Hesham M. El-Badawy1, Ahmad Yehya2, Hosni El-Motaafy3
1Network Planning Department, National Telecommunication Institute, Cairo, Egypt
2Department of Electrical Engineering, Al-Azhar University, Cairo, Egypt
3Department of Electronics and Computer Engineering, HIT, Tenth of Ramdan City, Egypt
Email: mahammad.safwat@gmail.com, heshamelbadawy@ieee.org, ahmed_yahya_1@yahoo.com, hosni.motaafy@gmail.com
Copyright © 2014 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 20 April 2014; revised 15 May 2014; accepted 25 May 2014
ABSTRACT
The call admission control (CAC) optimizes the use of allocated channels against offered traffic maintaining the required quality of service (QoS). Provisioning QoS to user at cell-edge is a challenge where there is limitation in cell resources due to inter-cell interference (ICI). Soft Frequency Reuse is ICI mitigation scheme that controls the distribution of resources between users. In this paper, the Impact of four CAC schemes (Cutoff Priority scheme (CP), Uniform Fractional Guard Channel (UFGC), Limited Fractional Guard Channel (LFGC), New Call Bounding (NCB) scheme) at cell-edge have investigated using queuing analysis in a comparative manner. The comparison is based on two criteria. The first criterion guarantees a particular level of service to already admitted users while trying to optimize the revenue obtained. The second criterion determines the minimum of number of radio resources that provides hard constraints in both of blocking and dropping probabilities. The four schemes are compared at different scenarios of new and handover call arrival rates.
Keywords:Call Admission Control, Soft Frequency Reuse, QoS

1. Introduction
With the rapid development of wireless network communication, careful allocation of radio resources plays a significant role in achieving the required QoS in wireless cellular networks and considerable efforts have been focused on call admission control (CAC) in order to maintain the required QoS [1] . Cell-edge is an area at cell which is difficult to maintain suitable QoS for its users. This is because there is a limitation in radio resources due to inter-cell interference (ICI) [2] and sharing the radio resources with handover users.
Modern ICI mitigation schemes divide the cell into cell-edge and cell-core. In these schemes the users are divided according to their locations from the e-NodeB and the resources they can access to cell-edge and cell-core users. One of the most ICI mitigation schemes, which are used in LTE-Advanced network, is Soft Frequency Reuse (SFR). In SFR scheme, for each cell in the network; the cell is divided into two parts: cell-edge and cellcore. In addition, the available Resource Blocks (RBs) (basic resource element in LTE networks) are divided into cell-edge RBs and cell-core RBs. All of users within each cell are also divided into two groups which based on the SINR: cell-edge users and cell-core users. It is called SFR as the frequency partition only applies to the cell edge users, the cell edge users are restricted to use this frequency sub-band only and all frequency bands are available to the cell-core users. So the effective frequency reuse factor is still close to one [2] [3] .
Cell-edge performance is such a subject that faces challenge in modeling and analysis. What makes the modeling difficult is that, to achieve some sense of accuracy, one need to consider ICI impact as well as handover traffic effect from adjacent cells.
Handoff priority-based CAC schemes have great impact on cell-edge users. First of all it occurs on cell-edges and secondly it depends on cell-edge radio resources. Therefore we cannot ignore its effect in cell-edge performance. The handover process depends on the policy that control handover access to the cell which in turn depends on the associated CAC scheme adopted.
Various handoff priority-based CAC schemes have been proposed. One of these schemes depends on reserving a portion of channel for handoff calls; whenever a channel is released, it is returned to the common poll of channels. This scheme is called the cutoff priority scheme [4] . On the other hand, the fractional guard channels schemes which depend on admitting a new call with certain probability. This scheme was first proposed by Ramjee et al. [5] and used extensively thereafter [6] -[9] ; it is shown to be more general than the cutoff priority scheme. A CAC scheme named New Call Bounding (NCB) scheme [10] -[12] smoothly throttles the admission rates of calls according to their priorities as well as it aims to provide multiple prioritized traffic with a desired QoS. In the rigid division-based CAC scheme, all channels allocated to a cell are divided into two groups: one to be used by all calls and the other for handover calls only [13] .
In [14] , a traffic analysis is evolved for soft frequency reuse ICI mitigation scheme using queuing model and the performance metrics of blocking and outage probability is deduced in terms of resources availability. Handover users’ traffic is not addressed in the analysis. In [15] , the SFR is modeled in collaboration with UFGC schemes and blocking probability is deduced in cell-edge and cell-core separately.
The applied CAC scheme affects on the cell-edge performance. Each CAC scheme behaves differently according to network conditions and traffic load. Consequently by using the most suitable scheme according to network condition, the system performance can be optimized. So a comparison between the different CAC schemes is deeply needed. According to this comparison, the scheme that provides better performance will be preferred.
In this work, a comparison between different CAC schemes is evolved in collaboration with SFR in order to evaluate each scheme impact on cell-edge performance. The evaluation is based on the two QoS parameters: New call Blocking probability and handover dropping probability. Four schemes are addressed in this work; Cutoff priority scheme, Uniform Fractional Guard Channel, Limited Fractional Guard Channel and New Call Bounding scheme. This comparison is based on applying some restrictions on each scheme and compares the response against these restrictions. Two criteria will be adopted in this comparison [5] [16] :
• System behaviour with hard constraint on dropping probability: in this criterion, the parameters setting are adjusted for new call blocking optimality while the dropping probability meets its constraint at specific new call and handover arrival rate.
• System behaviour with hard constraint on dropping and blocking probabilities: in this criterion, in order to meet specific constraint in both of dropping and blocking probabilities (which are two contradictory performance metrics), the number of radio resources should be increased. So each scheme parameters are adjusted to meet the first metric and the number of radio resources is increased to meet the second.
The first criterion guarantees a particular level of service to already admitted users while trying to optimize the revenue obtained. The second criterion is more of network design problem where radio resources need to be allocated a priori based on, for example, traffic projection. In the second criterion, the preference will be the minimum number of radio resources required to fulfil blocking and dropping constraints.
Another important aspect of these criteria is the design of algorithms for determining the optimal setting for parameters associated with the criteria. It is important that the algorithms are simple and efficient.
2. Schemes Models
In the following, Four CAC schemes will be introduced and modeled using queuing theory. In order to investigate the traffic analysis at cell-edge, the CAC schemes are merged with SFR in the proposed models. Then their performance metrics will be deduced in order to compare between them according to the mentioned criteria.
The cutoff priority technique keeps a certain amount of channels to handover calls only while the rest of the channels can be shared by both new calls and handover calls. Hence, handover calls are given higher priority over new calls, and as a result the reduction in the handover probability comes at the expense of higher blocking rate. Figure 1 illustrates the state diagram of Cutoff priority scheme with SFR.
In Fractional Guard Channel the new call is admitted by a certain probability which is a decreasing (or, more accurately, non-increasing) function of the number of occupied channels while a handover call is admitted as long as there is a free channel. Uniform FGC is special case of FGC where the acceptance probability has a constant probability that is independent of number of occupied channel. While Limited FGC is another type of FGC in which the acceptance probability varies between three values (1, βl, 0) according to channels occupation. Figure 2 depicts the state diagram of Fractional Guard Channel with SFR for UFGC and Limited FGC.
In New Call Bounding scheme, a threshold is used to limit the number of new calls in the cells. Handover calls are only blocked if all channels are occupied. The scheme works as follows: if the number of new calls in a cell exceeds a threshold when a new call arrives, the new call will be blocked; otherwise it will be admitted. The handover call is rejected only when all channels in the cell are used up. The idea behind this scheme is that we would rather accept fewer customers than drop the ongoing calls in the future, because customers are more sensitive to call dropping than to call blocking. Figure 3 illustrates the state diagram of New Call Bounding scheme with SFR.

Figure 1. The state diagram of Cutoff priority scheme with SFR.
 (a)
(a)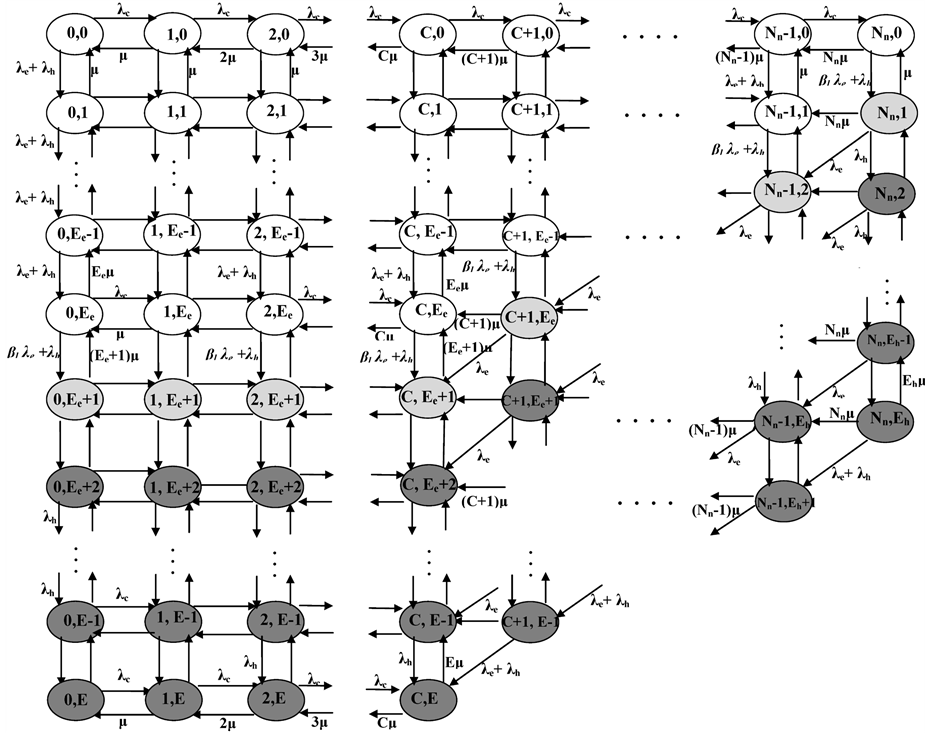 (b)
(b)
Figure 2. The state diagram of Fractional Guard Channel with SFR (a) UFGC (b) LFGC.
The four schemes are modelled using queuing analysis. For the sake of more inspection of traffic analysis at cell-edge, the resources at cell-edge are modelled in a separate dimension. The resources are distributed between cell-edge and cell-core according to SFR policies.
In the Markov representation of the four schemes which shown in Figures 1-3, Cutoff priority scheme, LFGC and UFGC scheme are modelled using two dimension Markov chains while NCB is modelled using three di-

Figure 3. The state diagram of new call bounding scheme with SFR.
mensions Markov chain to separate between new and handover call at cell-edge. In each scheme, the state space Γ is defined with i representing the number of RBs used by cell-core users, j representing the number of RBs used by cell-edge users and k representing the number of RBs used by handover users (for NCB only). Let N denotes the number of available RBs that can be used for transmission in each transmission time interval (TTI) in the cell. The maximum number of RBs that can be assigned to the edge-users and core-users is E and C respectively; so we get E + C = N. Let λ denotes the arrival rate of new call and λc, λe, denote the arrival rate for new calls in cell-core, cell-edge respectively. So λ = λc + λe.. λh is the arrival rate for handover calls. The current work considers that the arrival process for new calls and the arrival process for handoff calls are all Poisson. The channel holding times (μ) for new calls and handoff calls are exponentially distributed, and for simplicity it is assumed to be equal for three users. Each scheme has its own parameter setting as follow:
Cutoff priority scheme: the number of guard channels reserved for handover users T as shown in Figure 1. Let Ee denotes the number of cell-edge radio resources which are available for new call and handover users.
Uniform Fractional Guard Channel: the percent at which the new call is admitted at cell-edge which is called “acceptance probability β*” as shown in Figure 2(a).
Limited Fractional Guard Channel: The number of guard channels T and the new call acceptance probability βl as shown in Figure 2(b).
New Call Bounding scheme: the maximum number of RB that can be assigned for new call M as shown in Figure 3.
The proposed queuing model can be solved using Successive over Relaxation (SOR) method to get steady state probability for each state. The SOR is an iterative method [14] [15] that used to solve the set of linear equation. Most models under investigation are irreversible Markov process. So, the SOR may be one of the most suited techniques to obtain steady state probabilities and the required performance metrics. SOR not only supports the feasible solution but also, it gives sufficient stability for the obtained results. Performance metrics can be obtained from this steady state probability.
In this method, a new set of equations, called SOR equations, are deduced from balance equations, the left hand side of these equations is a new value of steady state probability which is obtained iteratively using previous value for steady state probability on the right hand side. The speed of convergence is determined by relaxation factor ω, the choice of relaxation factor is not necessarily easy, and depends upon the properties of the coefficient matrix. For symmetric, positive-definite matrices it can be proven that 0 < ω < 2 will lead to convergence, but we are generally interested in faster convergence rather than just convergence. Figure 4 depicts the flow chart of SOR algorithm.
3. System Performance Metrics
In this work, we will use blocking and dropping probabilities to evaluate system performance. Cell blocking probability is the probability that a new arriving cell-core user and a cell-edge user are blocked. In this work, only cell-edge part will be evaluated. Let ψb be the subsets of states where a new arriving cell-edge user are blocked.
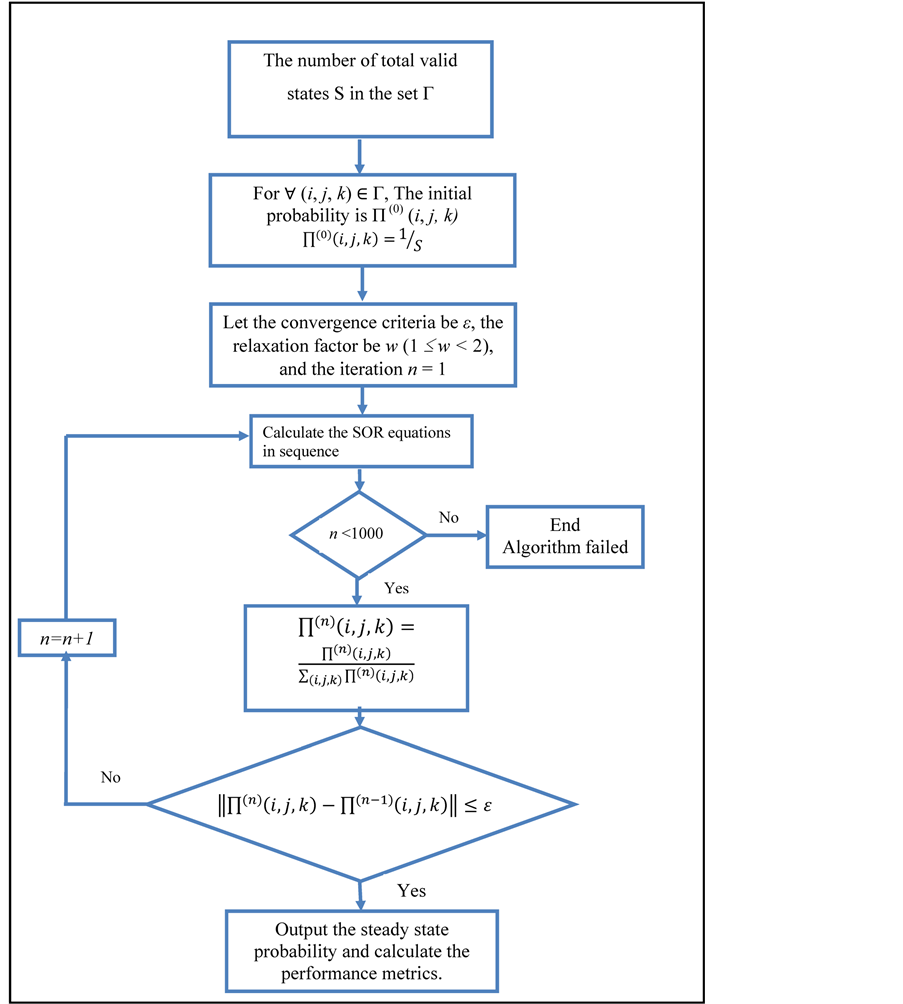
Figure 4. Flow chart for SFR algorithm.
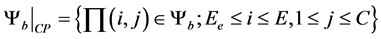 (1)
(1)
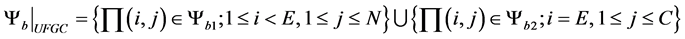 (2)
(2)
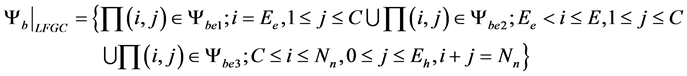 (3)
(3)
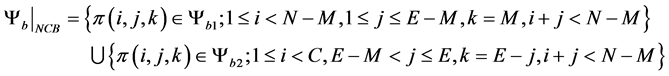 (4)
(4)
Then the blocking probability is calculated as [10] :
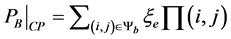 (5)
(5)
 (6)
(6)
 (7)
(7)
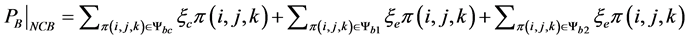 (8)
(8)
where ξe is the probability that there are users at the edge of the cell.
Finally let ψd be the subsets of states where the system forces to terminate the ongoing handover call.
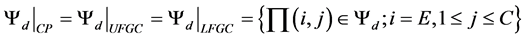 (9)
(9)
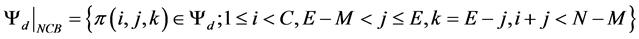 (10)
(10)
Then the cell dropping probability is calculated as:
 (11)
(11)
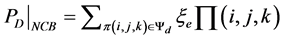 (12)
(12)
4. Comparison Criteria
4.1. Schemes Behavior with Hard Constraint on Dropping Probability
For a given number of channels, algorithms for determining the optimal parameters setting for each scheme will be deduced.
4.1.1. Cutoff Priority Scheme
The objective of this part is to minimize the number of guard channels T opt which meets a hard constraint on dropping probability Dh. Algorithm 1 is used to find Topt. It can be described from Figure 5 as follows: At the beginning, the algorithm starts with minimum number of guard channels (Topt = 1) then increase Topt until the handover dropping probability PD meets its constraint. If Topt = E while handover dropping probability PD does not meet its constraint then the available radio resources for handover calls does not satisfy the level of QoS and the number of allocated channels to the cell is not sufficient and the algorithm terminates.
4.1.2. Uniform Fractional Guard Channel
The optimal value of new call acceptance probability
 that fulfils the first criteria in UFGC will be deduced. This will minimize the
new call blocking probability subjected to a hard constraint on handover dropping
probability or minimize PB such that PD ≤ Dh.
that fulfils the first criteria in UFGC will be deduced. This will minimize the
new call blocking probability subjected to a hard constraint on handover dropping
probability or minimize PB such that PD ≤ Dh.
The presented algorithm in [5] will be used to find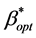 . This algorithm
is given in Figure 6 and can be described as follows:
At the beginning, the algorithm considers two cases: the first the case when all
channels are
. This algorithm
is given in Figure 6 and can be described as follows:
At the beginning, the algorithm considers two cases: the first the case when all
channels are
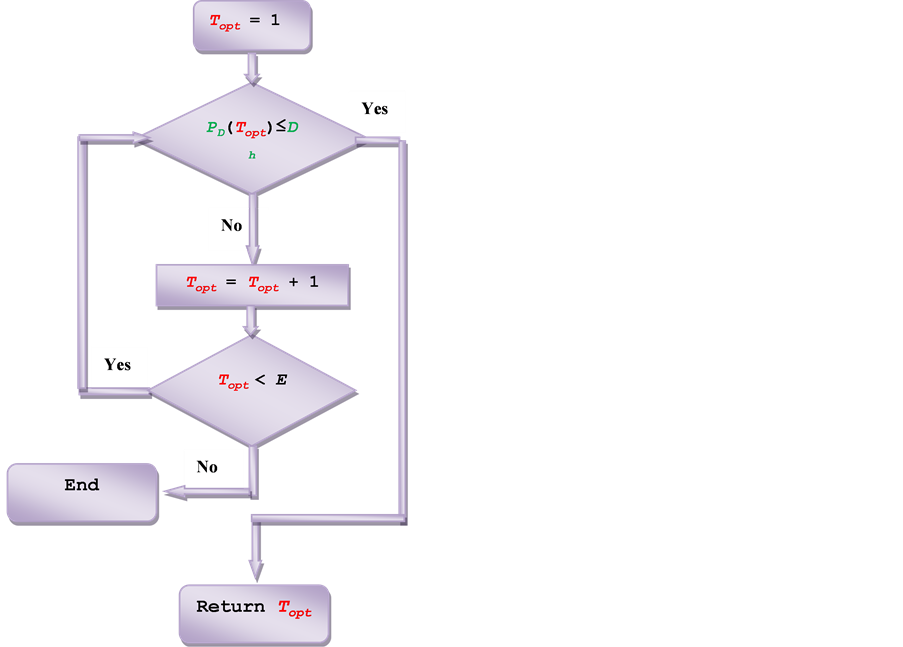
Figure 5. Algorithm 1 for adjust T to meet first criteria constraint.
exclusively used for handover calls. If the exclusive use of channels for handover
calls does not satisfy the level of QoS, then the number of allocated channels to
the cell is not sufficient and the algorithm terminates; the second the case when
all channels are shared between handover and new calls. If the complete sharing
satisfies the level of QoS, then the algorithm considers that
 and the algorithm terminates; otherwise the algorithm searches for the optimal value
of
and the algorithm terminates; otherwise the algorithm searches for the optimal value
of . The search method used in this algorithm
is binary search.
. The search method used in this algorithm
is binary search.
4.1.3. Limited Fractional Guard Channel
In LFGC, there are two parameters to adjust; the number of guard channels T and the new call acceptance probability βl. The presence of two parameters instead of one as other schemes leads to more flexibility and more capability for scheme control but this is in price of scheme complexity.
The proposed algorithm should control the two parameters. So, it is more complex and depends on merging Algorithm 1 & 2. Figure 7 illustrates Algorithm 3 to adjust both of T and βl to minimize blocking probability while maintain dropping probability under specific level. The algorithm starts by T = 1 and βl = 0, then the number of guard channels increases one by one till satisfy the level of QoS. While the required level is met, the new call acceptance probability βl is adjusted using Algorithm 2 to fine tuning the scheme parameters with required constraints and obtaining minimum blocking probability.
4.1.4. New Call Bounding Scheme
The objective of this part is to obtain the maximum number of allowable new calls that maintain the dropping probability less than Dh. Figure 8 illustrates Algorithm 4 for optimizing Mopt which can be described as follows: At the beginning, the algorithm starts with maximum number of allowable new call (Mopt = E) then decrease Mopt until the handover dropping probability PD meets its constraint. If Mopt = 0 while handover dropping probability PD does not meet its constraint then the available resources for handover calls does not satisfy the level of QoS and the number of allocated channels to the cell is not sufficient and the algorithm terminates.
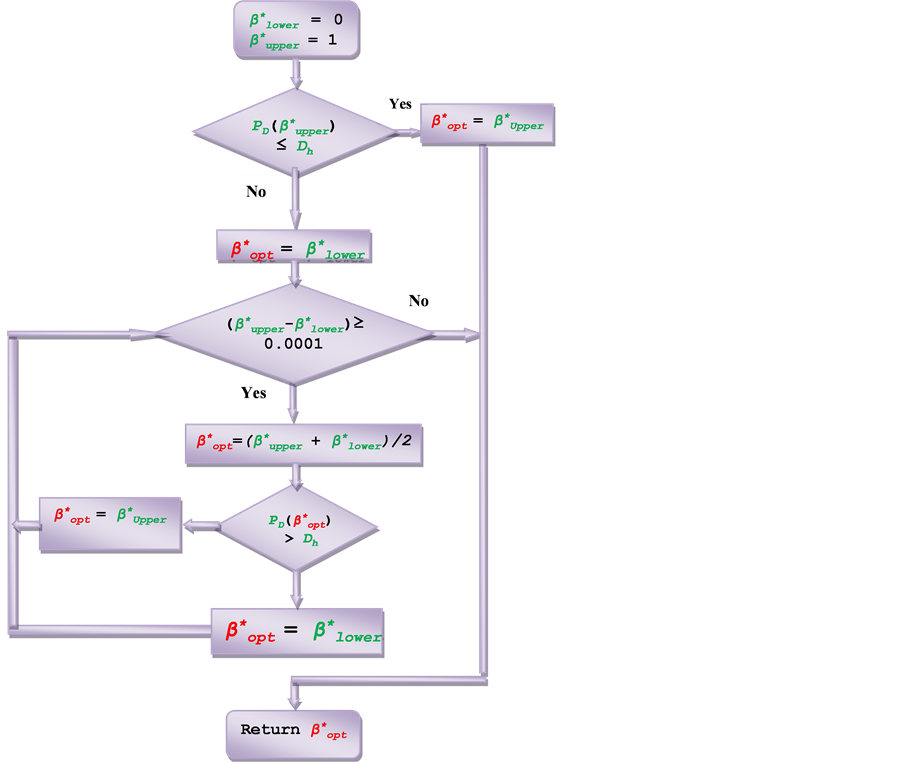
Figure 6. Algorithm 2 for adjust β* to meet first criteria constraint.

Figure 7. Algorithm 3 for adjust T & βl to meet first criteria constraint.

Figure 8. Algorithm 4 for adjust M to meet first criteria constraint.
4.2. Schemes Behavior with Hard Constraint on Dropping Probability and Blocking Probability
The blocking probability and the dropping probability are two contradictory performance metrics. It is very difficult to meet specific constraint in both of them by only adjust one parameter. So to solve this trade-off; the number of resources should be increased at each scheme. The objective of algorithms in this section is to minimizing the number of additive channels while satisfying the constraint in dropping and blocking probability.
The algorithms in the last section can be used to meet the first metric constraint and then we can add more resources till we meet second metric constraint. In the following, the algorithms to apply the second criteria at each scheme are concluded. Then the scheme with least resources will be elected.
4.2.1. Cutoff Priority Scheme
The objective of this algorithm is obtaining the minimum number of channels that meet the two constraints. The algorithm starts as illustrated in Figure 9 with minimum number of channels (Ec = 1) and minimum number of guard channels (Topt = 1) then increase Ec until the new call blocking probability meets its constraint. Then the algorithm starts to satisfy the dropping probability constraint without loose the adjusted blocking level. This is done by increasing Topt until the handover dropping probability PD meets its constraint without any increase in radio resources. After that a final check for blocking probability is executed and if it does not satisfy the required level, the radio resources should increase one by one again. Any tuning in Topt should starts with Topt = 0 to maintain optimality in blocking probability.
4.2.2. Uniform Fractional Guard Channel
Figure 10 depicts the algorithm to meet second criteria in UFGC. At the beginning, Ec and β* are proposed to be 1 for both then the radio resources increase one by one till The blocking probability constraint is met. Then β* is tuned according to Algorithm 2 to satisfy the dropping probability constraint. Applying Algorithm 2 may deviate the blocking over its constraint so additional radio resources may be added. Algorithm 2 should be applied each time channel is added.
4.2.3. Limited Fractional Guard Channel
In LFGC, there are three parameters to adjust (T, βl, Ec). So, it is more complex and depends on merging Algo-
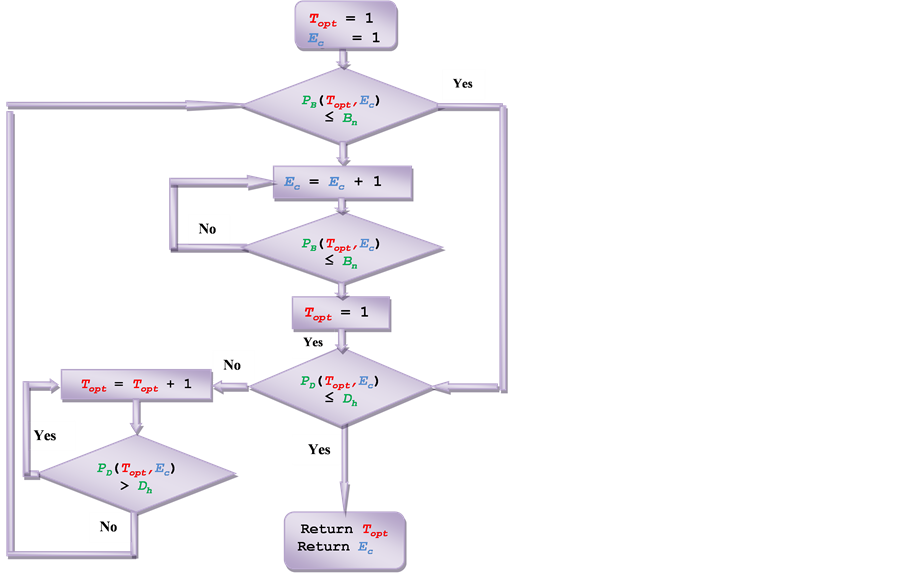
Figure 9. Algorithm 5 for obtaining minimum RBs in Cutoff priority scheme.

Figure 10. Algorithm 6 for obtaining minimum RBs in UFGC scheme.
rithm 3 & 4. Figure 11 illustrates the algorithm to meet second criteria. At the beginning, the three parameters are adjusted to 1. The blocking level of QoS is satisfied by adding channel one by one. T & βl are then adjusted using Algorithm 3 to meet the dropping level of QoS. A transition between blocking adjust and dropping adjust is executed till the two metrics are met.
4.2.4. New Call Bounding Scheme
Figure 12 illustrates applying the second criteria with new call bounding scheme. The algorithm starts with maximum number of allowable new call (M = E) and minimum number of radio resources (Ec = 1) then increase Ec until the new call blocking probability PB meets its constraint. After that M decreases one by one till dropping probability meets its constraint. An important check should be done to Mopt after adding each channel in order to optimize M to be compatible with number of channels change.
5. Numerical Results and Analysis
In this section, the impact of four schemes of CAC in collaboration with SFR on cell-edge is analyzed and evaluated in comparative manner. The blocking probability PB and dropping probability PD are the metrics under consideration for QoS. The queuing model parameters for the presented results are as follow: the available RB in the cell (N) is 48, the ratio of cell-edge RBs to total cell RBs is 1/3; the probability that there are users at the edge of the cell ξe is 1/2, the mean service period (μ) is 90 seconds. The SOR parameters are ω = 1.05, the convergence condition ε = 10−5 and n = 1000.
5.1. Schemes Comparison Based on First Criteria
Figures 13-15 depict the blocking probability
of each scheme at cell-edge with hard constraint of dropping probability Dh.
The scheme parameters Topt,
 , βl & Mopt of Cutoff
priority scheme, FGC and New Call Bounding scheme respectively are adjusted to meet
the constraint of first criteria using Algorithms 1, 2, 3 & 4.
, βl & Mopt of Cutoff
priority scheme, FGC and New Call Bounding scheme respectively are adjusted to meet
the constraint of first criteria using Algorithms 1, 2, 3 & 4.
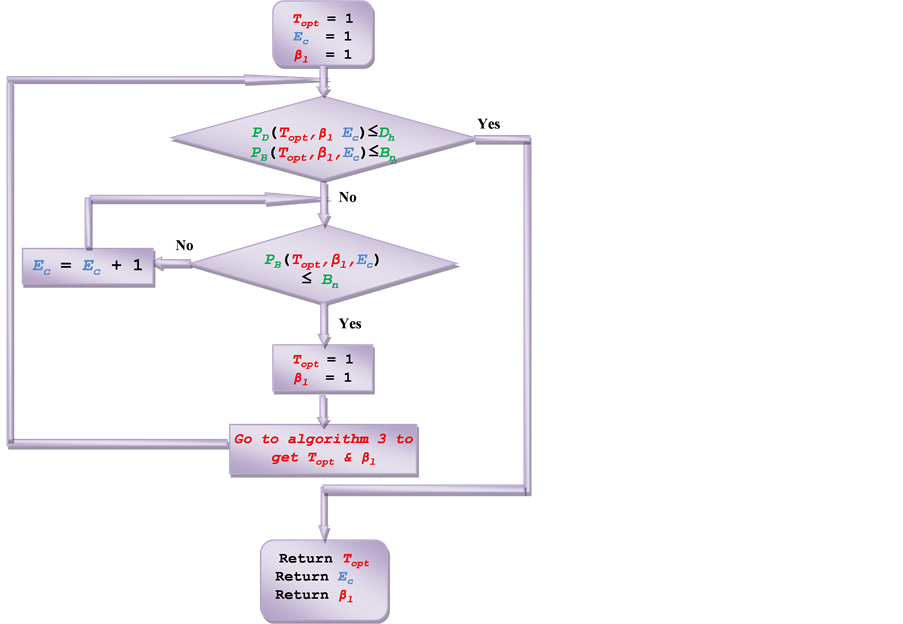
Figure 11. Algorithm 7 for obtaining minimum RBs in LFGC scheme.
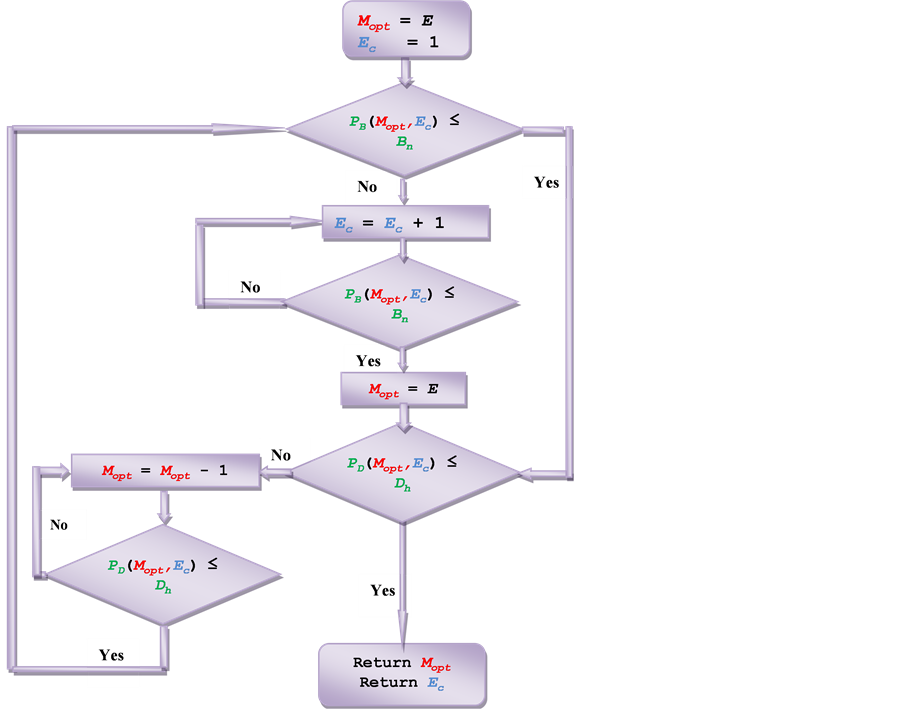
Figure 12. Algorithm 8 for obtaining minimum RBs in NCB scheme.

Figure 13. Comparison between the schemes based on first criteria at different new call arrival rate, λh = 0.25 λe call/sec.
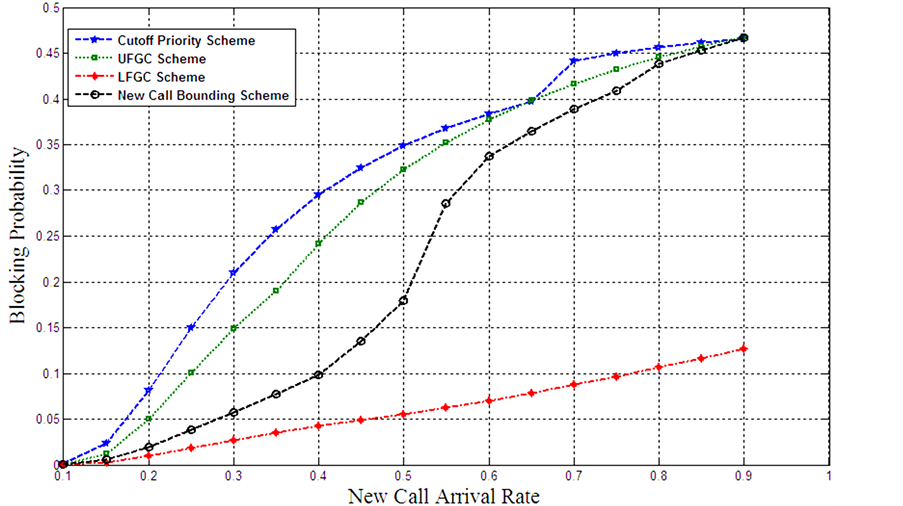
Figure 14. Comparison between the schemes based on first criteria at different new call arrival rate, λh = 0.5 λe call/sec.

Figure 15. Comparison between the schemes based on first criteria at different handover arrival rate.
Figure 13 and Figure 14 illustrate the blocking probability at cell-edge as a function of new call arrival rate at light and heavy handover traffic load when the maximum allowable dropping probability Dh is 0.2. The proposed handover arrival rate at Figure 13 and Figure 14 are 0.25 and 0.5 of new call arrival rate at cell-edge respectively. It is clear that the LFGC scheme provides minimum blocking probability than the other three schemes as illustrated from Figure 13.
Similar results are observed from Figure 14 when the handover arrival rate is 0.5 of new call arrival rate. The LFGC provides best performance then NCB, UFGC and finally the cutoff priority scheme.
Figure 15 illustrates the obtained blocking probability as a function of handover arrival rate. The maximum allowable dropping probability at cell-edge in the obtained results Dh is 0.2 and The proposed new call arrival rate is 0.7 call/sec. It can be noticed from the results that the impact of increasing handover arrival rates on LFGC scheme dose not differ much than its impact in new call arrival rates. LFGC provides minimum blocking probability than the other schemes regardless of handover traffic. After LFGC with significantly great values, NCB scheme appears and then UFGC and finally cutoff priority scheme.
The comparison between the schemes according to Figures 13-15 refers that the best network performance under hard constraint of dropping probability can be obtained using LFGC scheme at different new call and handover arrival rate. The interpretation of the obtained results as follow: each scheme has its own parameters that deeply affect the obtained performance metrics. In the cutoff priority scheme, the dominant parameter is the number of guard channels T. By adjusting T, the minimum blocking probability that maintain the dropping probability at certain level can be obtained. This can be adopted by increase (or decrease) T by unity step. Changing the number of guard channels by one channel has significant effect on both of blocking and dropping probabilities. So the unity step in cutoff priority scheme is significant large and will lead to have bad blocking probability. On the other hand, the dominant parameter in UFGC is the acceptance probability of new call β*. Although the unity step of β* is extremely low (fraction or less), but its effects covers all channels. So, any slight change in β* has significant effect on blocking and dropping probabilities. The unity step in NCB is one channel and its effect is similar to cutoff priority scheme. On the contrary, LFGC is adjusted by using of the two parameters T & βl. So, large steps can be adjusted by changing the number of guard channels while the acceptance probability can be used for fine tuning as its impact cover only one channel.
It can be concluded that to guarantee a particular level of service for admitted call while minimizing the blocking of new one, the best scheme to use is LFGC scheme then NCB and after that UFGC & cutoff priority scheme. This is valid at different traffic load of new call and handover arrival rate as illustrated in Figures 13-15.
5.2. Schemes Comparison Based on Second Criteria
In order to meet the contradictory constraints of dropping and blocking probability, we will follow Algorithms 4, 5 & 6 for the schemes under investigation. Figures 14-16 depict the minimum number of required channels at cell-edge for each scheme to meet the second criteria constraint.
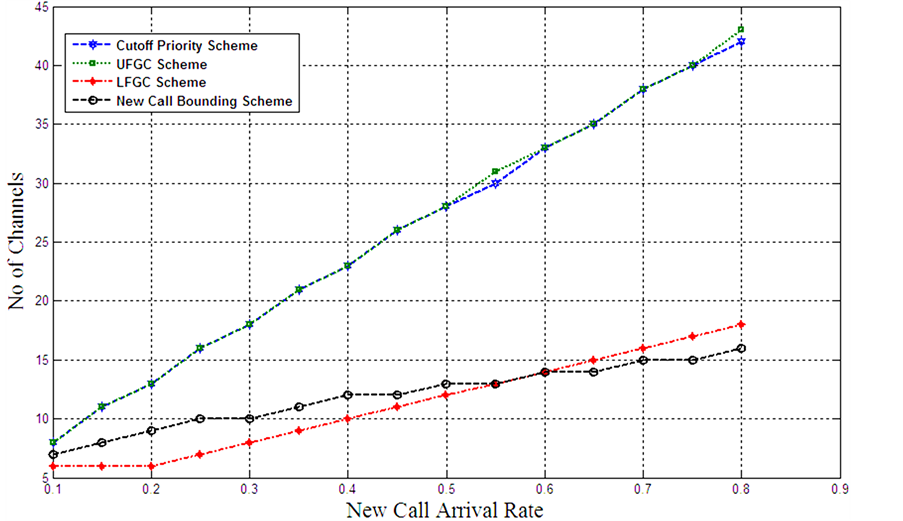
Figure 16. Comparison between the schemes based on second criteria at different new call arrival rate, λh = 0.25 λe call/sec.
Figure 16 illustrates the no of channels at different new call arrival rate. The required constraint of blocking (Bn) and dropping probability (Dh) at cell-edge in the obtained results are 0.1 & 0.2 respectively. The proposed handover arrival rate is 0.25 of new call arrival rate at cell-edge.
It can be observed from Figure 16 that LFGC & NCB require less channels to satisfy the QoS levels with a comparative advantage to LFGC at low new call arrival rates and to NCB at large new call arrival rates. While the cutoff priority scheme and UFGC act similar at different new call arrival rates.
When the handover arrival rate increases to 0.5 of new call arrival rate, it does not affect on similarities between cutoff priority and UFGC scheme as shown in Figure 17. While LFGC requires the least channels regardless of the rates of new call arrival.
Figure 18 depicts the no of channels at different handover arrival rate. The proposed new call arrival rate in the obtained results is 0.7 call/sec. It can be noticed from the results that the LFGC scheme requires minimum channels, then NCB scheme. UFGC requires almost the same radio resources as the cutoff priority schemes.
Figures 16-18 illustrate that generally LFGC requires minimum radio resources to meets hard constraint of QoS. NCB provides better system performance than UFGC and Cutoff priority scheme. Finally UFGC and Cutoff priority scheme behave similar at different new call and handover rates.
Although LFGC provides best performance in the investigated criteria, but this is in price of scheme complexity. LFGC depends on two parameters as explained before. In addition, the associated algorithms to perform the criteria are more complex than other schemes as there are two parameters to adjust in case of first criteria and three parameters in case second criteria.
6. Conclusion
In this paper, the impact of call admission control schemes on cell-edge is discussed. A traffic analysis at the cell-edge is addressed by merging different CAC schemes with Soft Frequency Reuse. Four CAC schemes have investigated using queuing analysis in a comparative manner. The comparison is based on two criteria. The first criterion guarantees a particular level of service to already admitted users while trying to optimize the revenue obtained. The second criterion provides hard constraints in blocking new call and dropping handover one by control the number of radio resources. Algorithms for optimal parameters setting to meet criteria constraint for the four schemes are developed. From numerical analysis and results we can conclude that each scheme has its condi-
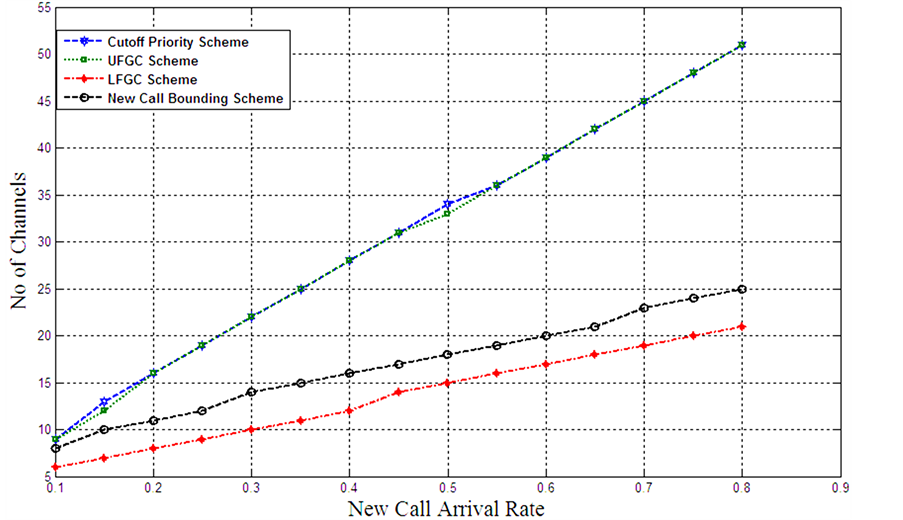
Figure 17. Comparison between the schemes based on second criteria at different new call arrival rate, λh = 0.5 λe call/sec.
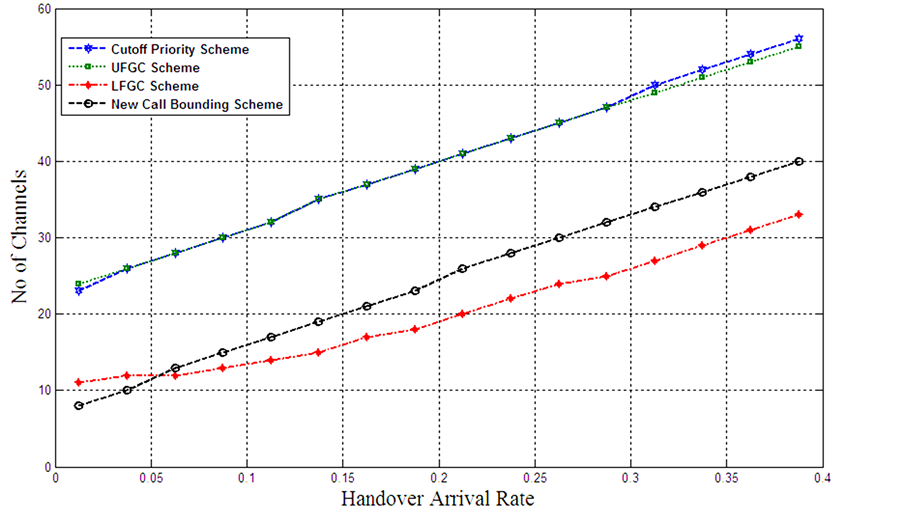
Figure 18. Comparison between the schemes based on second criteria at different handover arrival rate.
tions to provide best performance. The LFGC scheme behaves better even under heavy load of dropping and blocking rates but this is in price of the complexity. The performance of the other three schemes is close with comparative advantage to NCB.
References
- Huang, G.-S., et al. (2010) A Novel Dynamic Call Admission Control Policy for Wireless Network. Journal of Central South University of Technology, 17, 110-116.
- Qian, M.L., et al. (2012) Inter-Cell Interference Coordination through Adaptive Soft Frequency Reuse in LTE Networks. Wireless Communications and Networking Conference (WCNC), 2012 IEEE.
- R1-050507: Soft Frequency Reuse Scheme for UTRAN LTE. Huawei 3GPP TSG RAN WG1 Meeting no.41 Athens, Greece, May 2005.
- Hong, D. and Rappaport, S. (1986) Traffic Model and Performance Analysis for Cellular Mobile Radio Telephone Systems with Prioritized and Nonprioritized Handoff Procedures. IEEE Transactions on Vehicular Technology, 35, 77-92. http://dx.doi.org/10.1109/T-VT.1986.24076
- Ramjee, R., Nagarajan, R. and Towsley, D. (1996) On Optimal Call Admission Control in Cellular Networks. Proc. 15th Annual Joint Conf. IEEE Comp. and Commun. Societies (INFOCOM ’96), 1, 43-50.
- Vazquez-Avila, J., Cruz-Perez, F.A.C. and Orti-goza-Guerrero, L. (2006) Performance Analysis of Fractional Guard Channel Policies in Mobile Cellular Networks. IEEE Transactions on Wireless Communications, 5, 301-305. http://dx.doi.org/10.1109/TWC.2006.1611053
- Goswami, V. and Swain. P.K. (2012) Analysis of Finite Population Limited Fractional Guard Channel Call Admission Scheme in Cellular Networks) Procedia Engineering, 30, 759-766. http://dx.doi.org/10.1016/j.proeng.2012.01.925
- Kim, C., Klimenok, V.I. and Dudin. A.N. (2014) Analysis and Optimization of Guard Channel Policy in Cellular Mobile Networks with Account of Retrials. Computers & Operations Research, 43, 181-190. http://dx.doi.org/10.1016/j.cor.2013.09.005
- Chau, T.-C., Michael Wong, K.Y. and Bo, L. (2006) Optimal Call Admission Control with QoS Guarantee in a Voice/Data Integrated Cellular Network. IEEE Transactions on Wireless Communications, 5, 1133-1141.
- Fang, Y. (2003) Thinning Schemes for Call Admission Control in Wireless Networks. IEEE Transactions on Computers, 52, 685-87. http://dx.doi.org/10.1109/TC.2003.1197135
- Fang, Y. and Yi, Z. (2002) Call Admission Control Schemes and Performance Analysis in Wireless Mobile Networks. IEEE Transactions on Vehicular Technology, 51, 371-82.
- Firouzi, Z. and Hamid, B. (2009) A New Call Admission Control Scheme Based on New Call Bounding and Thinning II Schemes in Cellular Mobile Networks. IEEE International Conference on Electro/Information Technology, 2009. eit'09.
- Schneps-Schneppe, M. and Iversen, V.B. (2012) Call Admission Control in Cellular Networks. Mobile Networks, InTech, Zagreb, 111-136.
- Li, S., Wen, X.M., Liu, Z.J., Zheng, W. and Sun. Y. (2010) Queue Anlysis of Soft Frequency Reuse Scheme in LTE-Advanced. Second International Conference on Computer Modeling and Simulation, 2010. ICCMS'10, 1, 248-252.
- Safwat, M.A., El-Badawy, H.M., Yehya, A. and El-Motaafy, H. (2013) Performance Assessment for LTE-Advanced Networks with Uniform Fractional Guard Channel over Soft Frequency Reuse Scheme. Wireless Engineering and Technology, 4, 161. http://dx.doi.org/10.4236/wet.2013.44024
- Kolate, V.S., Patil, G.I. and Bhide. A.S. (2012) Call Admission Control Schemes and Handoff Prioritization in 3G Wireless Mobile Networks. International Journal of Engineering and Innovative Technology (IJEIT), 1, 92-97.

