Intelligent Control and Automation
Vol.07 No.04(2016), Article ID:70820,17 pages
10.4236/ica.2016.74010
The Possibility of Using RFID System to Automate and Integrate the Attendance of Professors and Students in the Classroom
Majid Meghdadi1, Ahad Abbaszadeh Azar2
1Computer Department, Engineering Faculty, University of Zanjan, Zanjan, Iran
2Department of Computer Engineering, Zanjan Branch, Islamic Azad University, Zanjan, Iran

Copyright © 2016 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY 4.0).
http://creativecommons.org/licenses/by/4.0/



Received: June 16, 2016; Accepted: September 20, 2016; Published: September 23, 2016
ABSTRACT
One of the most important goals followed in most systems is to increase efficiency, reduce errors and enhance ease of data entry tasks such as better services in organizations. Therefore, the use of intelligent tools is of the most important requirements for a management system in order to collect complete and accurate data and create complete information. In management, use of new technologies is recommended to have smart systems and reduce human errors. This study aimed to investigate “professors and students attendance system using RFID” and research population consists of professors and students. Findings show that, as attendance checking system in universities and schools is done through the class list and checking attendance of students needs to spend time and energy so it leads to a waste of valuable time and energy of professors to teach. Therefore, it is essential to use efficient and modern systems, because with the design and implementation of RFID attendance system and replacing the traditional system, time and energy waste could be avoided and attendance system could be promoted to an intelligent and integrated one. The designed system includes a number of hours of presence and absence, delays and rush to pay the salaries of professors at the University with its automatic identification through radio frequency. This system aims to create changes in this area and it is economic in whole.
Keywords:
RFID, Reader, Tag, Attendance System

1. Introduction
Radio Frequency Identification Devices (RFID) are devices to identify radio waves. RFID is a technology for automatic identification of objects. RFID tags are attached to an electronic device or a single product, and at the time of transfer request provide product information such as features of products and so on. RFID tags are small electronic devices that consist of a small chip and an antenna. To clarify, it can be said, RFID devices act like bar codes and magnetic strips on credit cards. For each object, RFID creates a characteristic that will be identified from others. As the information can be read from the barcode or magnetic stripe, RFID could be read by readers and through them information can be received or modified. In recent years, automatic identification procedures have been common among industries, professions and different companies. These methods are used to gather information about people, animals, goods and products in transit. Identification technology with radio-frequency waves is a new technology that is revolutionizing business productivity [1] [2] . Tags readers can quickly scan in thousands of meters per second. Product is detected when moved from one place to another place. Industrial reform of intermediaries, supporting the management chain, the product inventory list, regeneration of animals in rare cases, all can be of RFID applications. A controversial discussion of tags can be used for human identification (especially in attendance system of professors and students).
2. Statement of the Problem
Attendance in the traditional system of universities and schools is done through the class list, this list has been prepared by the education office for every professor and attendance system of professors at the University is done a coordinator. This process also has problems such as a full-time presence of coordinator. However, in some cases when coordinator is at vacation, an alternative responsible would be allocated. The alternative should constantly communicate with professors report his attendance according to the official list to the financial office to pay salaries. Professors should also before and after the classroom visit and report their presence to coordinator. With the start of classes, based on the list provided by the education office, the presence and absence in the classroom is determined. At the end of each semester, this list is returned to education office to check students’ attendance in classes in accordance with educational rules and regulations to remove the course of students with more than three absences, issue examination cards and so on.
According to various studies, the current attendance system in universities has numerous problems; these problems can be listed in several formats as per below:
a) Energy loss of professors: Each professor should check attendance of about 25 to 30 students per session and thus his energy is wasted.
b) Loss of time useful for teaching: Students attendance is naturally associated with the time and spending this time leads to a waste of time that is useful for teaching.
c) Misuse of list to change the absence of a student to attendance: In some cases, it is observed that students ask professors frequently to change their status from absence to presence.
d) The possibility of missing list: Its students’ right to be behaved in justice regarding the presence and absence. It is not possible in case of loss or lack of list.
e) Failure to notify parents of their children’s attendance in school classrooms: Some students without parents’ knowledge or giving false information to the parents instead of attending classes go for fun or elsewhere or on the pretext of attending classes delude family to go to places other than the classroom.
f) Students leave the class after ensuring presence in the class list: Some students may be busy, or for any reason after registering their presence in the class list leave class.
g) Delay or rush of professors in the University and classroom. Some professors for some reason delay to go to class or leave it early than due time.
According to the concepts on which difficulties of attendance system are mentioned in cases, now a new version of the RFID attendance system is offered that has viable advantages compared to traditional systems.
3. The RFID System
RFID systems consist primarily of tag and reader. An RFID tag is known as a transmitter including an antenna and a microchip. Microchip is used to store data and perform data transmission and antenna is used to communicate with the reader. Once a reader requests information from the tag sends identifying information such as ID through the radio frequency signals [3] .
An RFID reader usually includes a RF control unit and electronic equipment such as antenna to communicate through RF. To know how a RFID reader identify a tag and its ID consider a scenario based on Figure 1.
In this figure, the RFID reader sends radio signals at a certain frequency and specified delay (usually hundreds of times per second). Each tag, which has a radio frequency device within range of the reader show its existence by sending a reflection. Each of the tags has an internal antenna and is able to communicate with radio signals in determined frequencies [3] .
The size and shape of the antenna determines what frequency to be activated. Tags use energy of reader to reflect it. Tags can set received signal to send information such
Figure 1. Tags and readers in RFID system.
as identification numbers (ID) to the reader. Different types of tags and readers fit specific types of applications and environments. You must decide what type of tag and reader devices to use, which is optimal in terms of variety to your request. The type of tag will affect directly on the total system cost. In addition, readers have different range of prices and facilities [4] .
3.1. Types of RFID Tags
1. Passive tags: These tags have no internal energy source and their energy is supplied via RF signals sent by the reader and the antenna.
2. Semi-passive tags: Passive tags are very similar to passive tags with the difference that there is a tiny battery in them and they provide the energy needed to activate the internal circuit.
3. Active tags: These tags have an internal energy source in which provides a data transfer capability from greater distance. These three types of tags are different from other aspects such as size, domain of response, and speed of response together. These properties change moving from passive to active tags as follows:
Size, domain, price, speed of response and their reliability increases.
The lifetime of these tags changes as follows: passive > active > semi-passive.
Tags life is different due to two reasons; first, tags that have internal energy source have a limited life due to source and second, small battery in the semi-passive tags has shorter life than active tags energy source [4] .
3.2. Review of the Reader
RFID readers are also called interrogator devices, which are used for identification of tags around them. Readers are found in different shapes and sizes in portable terminals, and you may imagine readers as points to connect the tag to the network.
Reader is a medium between world and tags and consists of four separate parts that are shown in Figure 2.
API: API for the reader is an application program interface that allows you to register events that are made by the RFID tag. The interface provides capabilities such as settings, view and management [5] .
Communications: readers have communicative edge (where there is connection with another device), and like the other communication devices, RFID readers must be able
Figure 2. Components of reader system.
to connect to network. Communication components of readers manage network functions.
Event management: when reader sees a tag, this event is called observation and analysis of observation is called event. Event management defines what kind of events is important enough to be reported or placed in external applications on the network.
Antenna subsystems: is composed of one or more antenna and determines practical and logical interface in reader to receive a response from the tags [5] .
3.3. Frequencies and EPC Standards
Frequency is one of the most important factors affecting the efficiency of RFID system. Almost all RFID systems used in warehouses, distribution centers and supply chain are of three following frequency families:
(MHz 56.13HF) frequency: usually for short distances of about one meter.
(MHz960 ~ 860UHF) frequency: includes second-generation EPC-global standard and will have a range of up to 6 meters [6] [7] .
(GHz 45.2) frequency: is used in active tags and has high range. Usually is used for positioning in large-area. UHF technology provides good coverage area, speed, security and cost-effective equipment that mainly applied programs and systems such as warehouses, product management and manufacturers use [6] .
UHF 2EPC Gen Standard is provided to meet the needs of supply chains and acts in the frequency range of MHz960 ~ 860; in addition there is low possibility of interference with radio systems such as 802.11 radio network standard. The standard has high-speed in identification and reading tags, appropriate distance coverage, and provides electronic product codes that provide unique serial numbering and appropriate amount of memory to store user data [7] [8] .
3.4. The Benefits of Using RFID Technology
Tags can be hidden or embedded in most cases. Due to the fact that tags are offered in different sizes and shapes, users can choose one of them according to their needs. To read the code there is no need for direct contact. Due to the nature of tags (no need for direct contact) there will be no wear and tear. There is no possibility for manipulation of serial codes stored in tags [3] .
4. Some of the Applications of RFID Technology
4.1. Application of RFID in Library System
Official and public libraries continue to increase management on collections of property and maintain and improve customer service. During the last twenty years, libraries spread service from simple and periodic books to devices such as CD and DVD Multi-Media. In addition, many libraries provided computers for users to use the internet as a source of information [9] [10] .
In RFID technology for library management by sticking a tag on the book, which includes all specifications of book and using a series of antennas and readers we can take advantage of preventing the theft, automated systems of book borrowing and controlling the correct order of books on the shelves is shown in Figure 3 [9] [10] .
4.2. Implementation of RFID in IT Industry
In the current systems, there is no need to the line of sight between tag and reader because data connection occurs through the transmission of electromagnetic waves. It causes many products to be identified while importing and exporting. Therefore, the transmission is highly accelerated. In large warehouses with high volumes of input and output, using such benefit produced by RFID, there is considerable return on investment. Whenever one wants, one could check the number of products and their whereabouts. And, if there is shortage of products, a command will be sent to warehouse so that the shelves may be checked and refilled if necessary. Also, while importing or exporting products, the data is registered, warehouse stocks are checked and an order will automatically be sent to supplier, if necessary [11] .
1. Efficiency enhancement.
2. Reduction of errors resulting from data inputs.
3. No need to human forces to do simple and cumbersome tasks.
Extensive information about products and product components, manufacturing processes, the time of manufacture and delivery, its location in the warehouse and can be saved and stored in tags. In Figure 4 application of RFID in the industry is illustrated [11] .
Figure 3. RFID technology for library management.
Figure 4. RFID technology in industry.
4.3. The Use of RFID Technology for Animal Husbandry
Now modern animal husbandry use radio-frequency technology to automatically trace and track livestock. Using this technology, animals will be equipped with a radio-frequency tag. The tags will hang on animal ear, or will be planted subcutaneously or will be attached to other parts of body. This tag contains a unique number that is capable of storing some information in itself. Although it was years ago that for animal identification, we colored them with distinctive color or to make it easier for follow-up we used bells but RFID technology in this short time according to Figure 5 has managed to provide differentiated services in the field of animal husbandry, as well as other sciences [12] [13] .
4.4. Electronic Management of Documents and Files
With the increasing advancement of technology in various fields, procedures have been developed to manage the paper work. RFID is one of the optimum methods used all over the world. In this case, the RFID tags are attached to existing files; this tag has a unique number which data records are searchable in the database [14] [15] .
5. The Proposed Method
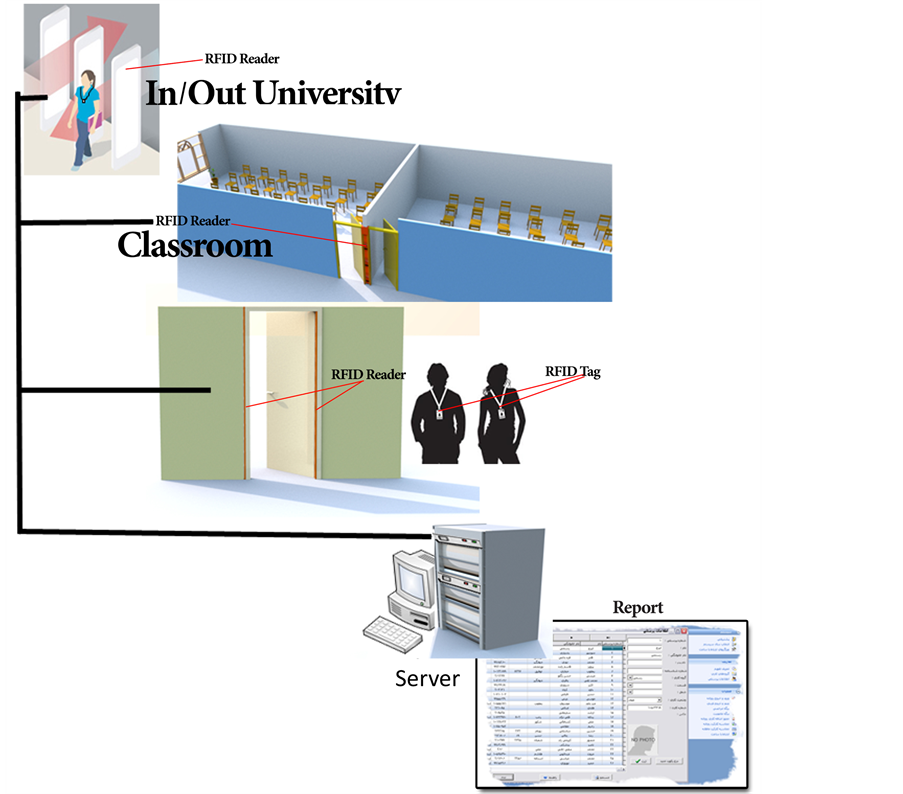
In this study, we examined the introduction of a new system where RFID system can replace coordinating person and it is time saving; the system was investigated from three perspectives is shown in Figure 6.
At first view, without the need for classroom attendance list, the presence of students are registered and professors enter the ID and password to log into their personal system and view hours and number of classes. In addition, the other section in professors’ attendance at the University will be recorded. And from the second view students can also enter the student number and password and log with limited access to see class time and attendance statues. Moreover, from the third view, education office can control presence, absence or delay of students and professors through this system and deal
Figure 5. RFID technology for livestock affairs.
Figure 6. Domain of RFID systems.
in accordance with educational rules and regulations. Using this system the additional costs such as issuing meal card and student card can be prevented. Students can book food one day before in the system and intake food at buffet and the long lines to reserve manually is not required. Meal card system is not embedded in system but has been investigated to be used in future works.
5.1. Block Diagram of the Overall System
In this system, when professors and students enter the university, professors and students information is read by tag reader installed on in the university and classes entrance and will be transmitted through the network to the database server. This processed information is used within an organization such as an university for various applications such as presence and absence of professors and students, entrance control and other purposes which is provided in Figure 7.
Figure 7. Block diagram of the overall system.
5.2. The Overall Diagram of the Overall System
This modular system is designed for traffic data collection and access for people from different fields defined in it, performing the necessary processing and transmission of information to the upper layers of information management systems. Different parts of the system are presented schematically in Figure 8.
6. Implementation and Introduction of Project
Block diagram of the system is visible in Figure 9.
6.1. Hardware of Systems
In the current hardware, if tag is not stored, approaching tag, buzzer gives constant alarm and sends tag code to serial port but relay is not activated. If the card is stored in the memory, approaching card, the buzzer gives one-time output and sends card code to serial port but the relay is activated this time and while the card remains under the
Figure 8. Overall diagram of the system in terms of hardware and software.
Figure 9. Block diagram.
coverage of module’s antenna, the relay remains on and when the card gets farer from the module, relay turns off.
6.1.1. RFID Technology
-Long Range 125 KHz
-Read Only
6.1.2. Database
-Sql Server
6.1.3. Coding Technology
-C #
6.1.4. Applications
-Control the entry and exit of professors
-Recording and reporting entry and exit information in the database
6.1.5. Capabilities
-Removing and adding cards to the system
-Removing and adding cards at once
-Ability to connect to the database through USB port
-Ability to connect to the internal network
6.1.6. Facilities
-Relay output
-Internal memory and antenna
6.1.7. Profile
-The operating voltage of 5 V
-The current consumption of 60 mA
-125 to 130 kHz operating frequency (Long Range)
-Four data output mode (with the user’s choice by pins)
-Effective identification distance of 1 m
-USB output data with transfer rates of 9600
This specifically stated hardware is visible in Figure 10.
6.2. System Software
Software or system interface is programmed with C# programming, including forms for reporting the presence and absence, recording entry and exit of professors and students and communication with the hardware system.
6.2.1. Account Information Form
This form is used to create new users. In addition, on this form the operator's account information can be edited or deleted in Figure 11.
Figure 10. System hardware (board along with the module).
Figure 11. Account information form.
6.2.2. Report form of Professors’ Absences
This form is for general report on the status of attendance of professors also it helps to find the absence at a limited interval in Figure 12.
6.2.3. Professors Delay Report
This form is to display lag professors and professors’ delay can be traced at a specified time limit in Figure 13.
6.2.4. Monitoring Form of Attendance of Professors and Students in the Classroom
One of the most important parts of the system is online monitoring form that at a glance you can see students and professors attendance with the green and red circles in Figure 14.
Figure 12. Professor absences form.
Figure 13. Professors delay report form.
Figure 14. Monitoring form of professors and students.
6.2.5. Relations of Database Tables
As any database could contain one or more tables, the aim of building database is to connect two or more tables.
The included database contains the tables of descriptions of professors, students and employees, classroom descriptions and so on. In order to identify which student is in which class, at which time, with which professor, one should connect the tables of professors, students and classrooms together. In Figure 15 the table having common fields with unique values is main table and the table having common fields with repetitious values is secondary table.
7. Evaluation and Comparison
Let’s assume that the college has 32 classes and 512 students and 32 professors and each reader is 5,000,000 Rials and a computer system costs 12,000,000 Rials and price of each tag is 7000 Rials, the price of meal card is 250,000 Rials and cost of RFID systems except initial cost is 10,000,000 Rials for the maintenance repair of the two devices.
P: professor R: Reader C: Class
S: student Comp: Computer T: Tag
Comp + (R + C) + ((S + T) * C) * (Tag) = The cost of attendance
12,000,000 + (5,000,000 * 32) + (((16 + 1) * 32) * 7000) = 175,738,000
One of the most important and the most efficient ways of management for overcoming the challenges of the presence and absence of traditional methods is attendance systems. The present study assessed the new systems and listed the benefits of and savings of this scenario as follows:
For example, the author analyzed this system at one of the college with 32 professors. Let’s assume 70% of professor are present at the classes (N = 22) and their salary for every an hour of teaching is 250,000 Rials and they have 1 minute of delay or they attend 1 minute early. For simplicity, every course is assumed to be 3 units and 5 classes a
Figure 15. Relations of database.
day are assumed. In the span of a week, 30 sessions and per term (17 weeks), about 510 seasons will be held. The results of calculations and time and cost savings are described below in Table 1 and are evaluated and compared in Figure 16 and Figure 17 for 1 minute and 2 minutes respectively.
Calculation, evaluation and comparison of meal card reservation system for future research and study is presented in Table 2 and Figure 18.
8. Conclusions
The aim of this study is to design and implement RFID attendance system and replace old one by a new system to avoid time and energy wasting to optimize class time and to integrate data and have smart universities and schools.
System was designed for RFID in C# and met the sample needs. Advantages and disadvantages of the use of RFID systems and return on investment are calculated. By implementation and calculations, effectiveness of the proposed system achieved by factorization of the limited sample.
Figure 16. Evaluation and comparison of the costs (with delay or hasten of one minute per session).
Figure 17. Evaluation and comparison of the costs (with delay or hasten of two minutes per session).
Table 1. Evaluation and comparison (with delay or hasten of one minutes per session).
Figure 18. Evaluation and comparison of the cost of meal cards with RFID system.
Table 2. Evaluation and comparison of the cost of meal cards.
The results show that use of the above system had desirable outcomes; Therefore by calculation of return of system cost we might conclude that these systems are more economical in terms of time. It is noteworthy that implemented system to ensure and check and fix its flaws and for efficient and optimal results was tested in a school.
9. Implications for Future Studies
Given that the current system can be used in the future in various fields such as meal card system in this study to guide future researchers and research, costs of RFID systems was evaluated and compared with meal card charges. However, this part of the system has not been considered in this study.
In the future, this system can be used to centralize the relationship between universities online, so they can be controlled by central office and communicate online via the Internet.
Cite this paper
Meghdadi, M. and Abbaszadeh Azar, A. (2016) The Possibility of Using RFID System to Automate and Integrate the Attendance of Professors and Students in the Classroom. Intelligent Control and Automation, 7, 93-109. http://dx.doi.org/10.4236/ica.2016.74010
References
- 1. Bhatt, H. and Glover, B. (2006) RFID Essentials. O’Reilly Pub, New York.
- 2. Ahson, S.A. and Ilyas, M. (2008) RFID Handbook Applications, Technology, Security, and Privacy (Hardcover). CRC Press, Boca Raton, Florida.
http://dx.doi.org/10.1201/9781420055009 - 3. Akpnar, S. and Kaptan, H. (2010) Computer Aided School Administration System Using RFID Technology. Social and Behavioral Sciences, 2, 4392-4397.
http://dx.doi.org/10.1016/j.sbspro.2010.03.699 - 4. Yu, D. (2011) Implementation of RFID Technology in Library Systems “Case Study: Turku City Library”. Thesis, Lahti University of Applied Sciences, Lahti.
- 5. Pérez, J., Seco, F., Milanés, V., Jiménez, A., Díaz, J.C. and de Pedro, T. (2010) An RFID-Based Intelligent Vehicle Speed Controller Using Active Traffic Signals. Sensors, 10, 5872-5887.
http://dx.doi.org/10.3390/s100605872 - 6. Di Giampaolo, E. and Martinelli, F. (2012) A Passive UHF-RFID System for the Localization of an Indoor Autonomous Vehicle. IEEE Transactions on Industrial Electronics, 59, 3961-3970.
http://dx.doi.org/10.1109/TIE.2011.2173091 - 7. Catarinucci, L., Colella, R., Mainetti, L., Mighali, V., Patrono, L., Sergi, I., et al. (2013) Performance Evaluation of a Novel Animals Tracking System Based on UHF RFID Technology. Journal of Communications Software & Systems, 9, 4-13.
- 8. Xing, Z., Wang, L., Wu, C., Li, J. and Zhang, M. (2011) Characteristics and Application of a Novel Loop Antenna to UHF RFID Receivers. International Journal of Antennas and Propagation, 2011, Article ID: 480717, 7 p.
- 9. Renold, A.P. and Joshi, R.R. (2013) An Internet Based RFID Library Management System. 2013 IEEE Conference on Information & Communication Technologies (ICT), Thuckalay, 11-12 April 2013, 932-936.
- 10. Modin, G., Mamdapur, N. and Rajgoli, I.U. (2011) Implementing Radio Frequency Identification Technology in Libraries: Advantages and Disadvantages. International Journal of Library and Information Science, 3, 46-57.
- 11. Kwon, H. and Lee, B. (2005) Compact Slotted Planar Inverted-F RFID Tag Mountable on Metallic Objects. Electronics Letters, 41, 1308-1310.
http://dx.doi.org/10.1049/el:20052940 - 12. Athanasios, S.V., Charalampos, Z.P., Alexander, B.S., Vasileios, A.N. and Eftychia, M.X. (2010) A Complete Farm Management System Based on Animal Identification Using RFID Technology. Special Issue on Information and Communication Technologies in Bio and Earth Sciences, 70, 276-284.
- 13. Ionescu, F., Hutu, R., Cimponeriu, A., Chilintan, M., Urian, R. and Hutu, I. (2010) RFID Technology Used for Monitoring Estrus Temperature in Cow. Lucrari Stiinlifice Medicina Veterinara, 53, 726-732.
- 14. Aguzzi, J., Sbragaglia, V., Sarrià, D., Garcìa, J.A., Costa, C., del Rio, J., et al. (2011) A New Laboratory Radio Frequency Identification (RFID) System for Behavioural Tracking of Marine Organisms. Sensors, 11, 9532-9548.
http://dx.doi.org/10.3390/s111009532 - 15. Huang, C.-T., Wang, S.-J., Wang, W.-L. and Wang, Y.-S. (2012) Construction of an Online RFID Enabled Supply Chain System Reliability Monitoring Model. International Symposium on Computer, Consumer and Control, Taichung, 4-6 June 2012, 626-629.
http://dx.doi.org/10.1109/is3c.2012.163